It’s really great that the FortiGate firewalls have a DHCPv6 server implemented. With this mandatory service, IPv6-only networks can be deployed directly behind a FortiGate because the stateless DHCPv6 server provides the DNS server addresses. (This is unlike Palo Alto or Cisco which have no DHCPv6 server implemented.)
However, the configuration on the FortiGate is really bad because nothing of the IPv6 features can be set via the GUI. (And this is called a Next-Generation Firewall? Not only the features count, but also the usability!) Everything must be done through the CLI which is sometimes hard to remember. Therefore I am publishing this memo of the appropriate CLI configuration commands.
Coming from Cisco devices (which only have the CLI ;)), the structure of the command line interface from Fortinet is quite different. That’s ok but I need some memos for that. What I really don’t like are the inconsistencies within the CLI, e.g. sometimes it’s called “ipv6”, sometimes “ip6”. Oh oh. At least the IPv6 policies can be configured through the GUI.
I am running a FortiWiFi 90D with FortiOS v5.2.4, build688.
End-User Interface w/ DHCPv6
A basic end-user interface needs an IPv6 address, router advertisements with the O-flag (for using stateless DHCPv6), as well as an advertised prefix with the O- and A-flag. Furthermore, a stateless DHCPv6 server provides the DNS server addresses. Here we go:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
config system interface edit "fg-trust3" config ipv6 set ip6-allowaccess ping https ssh set ip6-address 2003:51:6012:162::1/64 set ip6-send-adv enable set ip6-other-flag enable config ip6-prefix-list edit 2003:51:6012:162::/64 set autonomous-flag enable set onlink-flag enable next end end next end config system dhcp6 server edit 1 set domain "webernetz.net" set interface "fg-trust3" set dns-server1 2001:4860:4860::8888 set dns-server2 2001:4860:4860::4444 next end |
Of course, there are much more options to fine-tune the timers, etc. But the just listed commands are the very basic configuration steps to make it running.
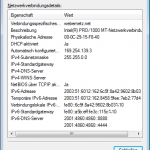
For your interest, this is how my IPv6-only network on a Windows 7 machine looks like with the just proposed settings:
End-User Interface w/ RDNSS
Tested on a FortiGate FG-90D with firmware v5.6.8 build1672 (GA), I am using the “IPv6 Router Advertisement Options for DNS Configuration”, RFC 8106, namely the recursive DNS server option (RDNSS) and DNS search list option (DNSSL). With these two options there is no need for any kind of DHCPv6 anymore. Everything solely relies on the RA, hence only SLAAC is used. Note that the O-flag is NOT sent anymore:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
config system interface edit "internal" config ipv6 set ip6-address 2001:470:1f0b:16b0::1/64 set ip6-allowaccess ping https ssh set ip6-send-adv enable config ip6-prefix-list edit 2001:470:1f0b:16b0::/64 set autonomous-flag enable set onlink-flag enable set rdnss 2620:fe::fe set dnssl "weberlab.de" next end end next end |
Looking at those RAs with Wireshark you can see all these options in place, while there is no flag set in the RA itself. (The “on-link” and “autonomous address-configuration” flags are within the prefix information option. Those are not seen in the following screenshot):
Routing
For routing IPv6 traffic within the network, static routes or OSPFv3 are quite common. The commands for those are the following. (Have a look at my OSPFv3 blog post which lists the appropriate commands for many other firewall and router devices.)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
config router static6 edit 1 set gateway 2003:51:6012:101::1 set device "wan1" next end config router ospf6 set auto-cost-ref-bandwidth 10000 set router-id 172.16.1.6 config area edit 0.0.0.0 next end config ospf6-interface edit "wan1" set interface "wan1" next edit "fg-trust3" set interface "fg-trust3" next end set passive-interface "fg-trust3" end |
Show and Get and Diagnose
To verify the working settings of the FortiGate, this CLI commands can be used:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 |
fd-wv-fw04 # diagnose ipv6 address list dev=73 devname=fg-trust3 flag=P scope=0 prefix=64 addr=2003:51:6012:162::1 dev=70 devname=vsys_fgfm flag=P scope=254 prefix=128 addr=::1 dev=68 devname=vsys_ha flag=P scope=254 prefix=128 addr=::1 dev=63 devname=fg-trust flag=P scope=0 prefix=64 addr=2003:51:6012:160::1 dev=59 devname=root flag=P scope=254 prefix=128 addr=::1 dev=6 devname=wan1 flag=P scope=0 prefix=64 addr=2003:51:6012:101::6 dev=6 devname=wan1 flag=P scope=253 prefix=10 addr=fe80::a5b:eff:fe3c:115d dev=73 devname=fg-trust3 flag=P scope=253 prefix=10 addr=fe80::a5b:eff:fe3c:115c dev=63 devname=fg-trust flag=P scope=253 prefix=10 addr=fe80::a5b:eff:fe3c:115c fd-wv-fw04 # diagnose ipv6 neighbor-cache list ifindex=6 ifname=wan1 ff02::5 33:33:00:00:00:05 state=00000040 use=241 confirm=8282556 update=8276556 ref=1 ifindex=6 ifname=wan1 ff02::6 33:33:00:00:00:06 state=00000040 use=455 confirm=6566 update=566 ref=1 ifindex=59 ifname=root :: 00:00:00:00:00:00 state=00000040 use=8278891 confirm=8284891 update=8278891 ref=10 ifindex=73 ifname=fg-trust3 ff02::c 33:33:00:00:00:0c state=00000040 use=261418 confirm=267418 update=261418 ref=1 ifindex=6 ifname=wan1 2003:51:6012:101::1 00:19:e2:a1:f9:8a state=00000002 use=151 confirm=470 update=470 ref=2 ifindex=73 ifname=fg-trust3 2003:51:6012:162:8458:5fee:7eb2:77d4 00:0c:29:15:f8:40 state=00000002 use=2076 confirm=2016 update=2016 ref=2 ifindex=6 ifname=wan1 fe80::20c:29ff:fe63:2159 00:0c:29:63:21:59 state=00000004 use=6676402 confirm=6676402 update=2760067 ref=1 ifindex=6 ifname=wan1 fe80::219:e2ff:fea1:f98a 00:19:e2:a1:f9:8a state=00000002 use=0 confirm=77 update=77 ref=3 fd-wv-fw04 # get router info6 routing-table IPv6 Routing Table Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 I - IS-IS, B - BGP * - candidate default Timers: Uptime S* ::/0 [10/0] via 2003:51:6012:101::1, wan1, 23:00:41 C ::1/128 via ::, root, 23:00:49 O 2003:50:aa3d:1dfe:b2c6:9aff:fefd:ca97/128 [110/10010] via fe80::219:e2ff:fea1:f98a, wan1, 22:59:59 C 2003:51:6012:101::/64 via ::, wan1, 23:00:49 O 2003:51:6012:110::/64 [110/110] via fe80::219:e2ff:fea1:f98a, wan1, 22:59:59 O 2003:51:6012:130::/64 [110/110] via fe80::2a94:fff:fea8:772d, wan1, 22:59:59 C 2003:51:6012:160::/64 via ::, fg-trust, 23:00:49 C 2003:51:6012:162::/64 via ::, fg-trust3, 15:34:22 O 2003:51:6012:180::/64 [110/20] via fe80::20c:29ff:fe63:2159, wan1, 22:59:59 C fe80::/10 via ::, fg-trust3, 15:34:22 |
Featured image “grüne Wiese mit Blick auf Kirchberg an der Raab” by Edi Schwarzl is licensed under CC BY-NC 2.0.



Nice article thanks. You can enable IPv6 in the Fortinet GUI by enabling the IPv6 feature in the dashboard.
Hey Lee.
Yes, that is correct, BUT you can only configure the IPv6 address, static route, and the IPv6 policy. You can NOT configure anything else which is mandatory for IPv6 to run such as router advertisements, prefix-list, DHCPv6, or any routing protocol. ;(
Thanks to your blog I found the ip6-send-adv flag ;-) !!
I am struggling to get an IPv6 setup running between 2 vdom’s with an inter vdom link. Aaahhhhhh. I am beginning to think Fortinet forgot to think about this option.
Ever tried such a setup ?
I just found my error!!
On a Fortigate, in the IPv6 policy you are allowed to use IPv4 services, even if they make no sense. I made a rule to allow PING, but that was only defined for IPv4, after creating a PING6 for ICMP6 everything worked.
The interface for IPv6 policy should prevent you using IPv4 objects and vice versa.
Indeed Fortigate has a very “next generation” GUI interface!!!
Hello all,
In FG-300C
i have configured IPv6 in my WAN port and LAN port also all-to-all policy configured but i am unable to ping ISP gateway from internal network as well firewall.
Please help me for the solution
Thanks
Kalidas
Hey Kalidas,
please check the following:
– To be able to ping the firewall, you must allow “Ping” within the “IPv6 Administrative Access” section on the interface.
– Please double check the correct IPv6 addresses configured on the interfaces.
– Do you have the correct static IPv6 routes, especially the default route?
– Have a look at the IPv6 neighbor cache (diagnose ipv6 neighbor-cache list) to verify whether the LAN and WAN side really gets some neighbors.
– Verify that you have correctly configure an IPv6 policy (!) and not an IPv4 policy. (Due to the **** design of FortiGates you have two different policies for each protocol.)
Ciao,
Johannes
How can I add an address ipv4 to a rule ipv6.
I’m trying to replicate my policies in order to have load balance with another internet connection that uses ipv6
Hi Jhon.
You cannot add an IPv4 address (object) into an IPv6 rule. Welcome to the bad policy design of Fortinet. ;(
hi,
from ipv6 to ipv4 ?
ipv6 -> ipv6 (fortigate)ipv4-> ipv4(router) -> internet
How do I route? (When the gateway is ipv4.)
Do not use policy64?
Oh, you must solve a couple of problems until you can use that. You need DNS64 and NAT64 among others.
Hello,
Nice article, I’ve a question.
I tried IPV6 6 month ago and I’ve a lot of configuration. How can I “clean” my Ipv6 section to try new configuration. I’ve 5 section “edit” Under ipv6 section and want to reset this part of configuration.
Hey Jerome,
similar to all other “edit” sections within the FortiGate CLI you can “delete” those statements. (And for “set” commands you can “unset” them.)
For example, if you have the following:
config ip6-prefix-list
edit 2003:51:6012:162::/64
–> If you are in the “config ip6-prefix-list” config path you can do the following:
delete 2003:51:6012:162::/64
Ciao, Johannes
Hello Johannes,
Many thanks
Jerome
Hello, my device is Fortigate 92D running Fortios 6.0.4 and Fortios 5.4, there are problems in both system versions, I set IPv6 and DHCP6, the computer can not obtain IPv6 IP through DHCP6, but can pass slaac Obtain a set of IPv6 IP. If I set the IPv6 IP to the network card, the computer can’t ping the internal gateway, and I can’t connect to the external network. But the Fortigate can ping the internal gateway and the external network. My settings are as follows. Can you help me to see where the settings are wrong?
PS: I am from Taiwan, some English is not good, please forgive me….
wan1:
config system interface
edit “wan1”
set vdom “root”
set ip 211.***.***.*** 255.255.255.0
set type physical
set estimated-upstream-bandwidth 40000
set estimated-downstream-bandwidth 100000
set role wan
set snmp-index 1
config ipv6
set ip6-address 2001:b030:****:****::1/64
end
next
end
internal:
config system interface
edit “internal”
set vdom “root”
set ip 192.168.1.1 255.255.255.0
set allowaccess ping https ssh http fgfm capwap
set type hard-switch
set device-identification enable
set device-identification-active-scan enable
set role lan
set snmp-index 5
config ipv6
set ip6-address 2001:b030:****:****::1/64
set ip6-allowaccess ping https ssh http fgfm capwap
set dhcp6-information-request enable
set ip6-send-adv enable
set ip6-other-flag enable
config ip6-prefix-list
edit 2001:b030:****:****::/64
set autonomous-flag enable
set onlink-flag enable
next
end
end
next
end
dhcp6:
config system dhcp6 server
edit 1
set lease-time 86400
set subnet 2001:b030:****:****::/64
set interface “internal”
config ip-range
edit 1
set start-ip 2001:b030:****:****::2
set end-ip 2001:b030:****:****::200
next
end
set dns-server1 2001:b000:168::1
set dns-server2 2001:b000:168::2
set dns-server3 2001:4860:4860::8888
next
end
Hello cf,
I am sorry, but I cannot troublehsoot your issue remotely. Please open a ticket at Fortinet for further troubleshooting.
Try to capture the RAs from the FortiGate and analyze them in Wireshark. Have a look at the flags (A, O, M, etc.). Are they correctly set according to your setup?
You can also try different clients. Windows/Android/iOS behave differently when it comes to SLAAC vs. stateful DHCPv6.
Cheers,
Johannes
Hello cf,
Did you find your problem concerning IPv6 on Fortigate 92D?
I just spent around 6 hours troubleshooting the same things and I’ve found the problem. I thought I’d let you know:
Fortigate/Fortiwifi 92D does not support STP (hardware limitation). A command has been introduced starting FortiOS 5.4.1 (yes, still applicable today with version 6.0.4) that messes with IPv6 behavior (among other things). Just disable it:
Config system global
set hw-switch-ether-filter disable
end
It’s actually written in the release notes… If we just bothered reading those. lol.
Enjoy,
hello
Does anyone knows if there is a problem to assign both ipv4 and ipv6 on the same interface.
I tried doing that but got this error message:
edit LAN_1
set secondary-IP enable
config ipv6
config ip6-extra-addr
edit fd9d:22d3:cd28:7257::2/64
end
Please configure primary IPv6 address prefix first
object set operator error, -20 discard the setting
Command fail. Return code -20
i think this was my mistake ..
i didn’t notice the primary ip6 addressing :)
Dear All,
i am unable to ping IPv6 ISP gateway from forigate-30E (v6.0.4 build0231 (GA))
WAN IP configured 2401:0:4000::50b/127
gateway -2401:0:4000::50a
static default route added towards 2401:0:4000::50a
Ipv6 policy configured & all traffic allowed for any interface
but still not able to ping Ipv6 gate .
stats:
execute ping6 2401:0:4000::50b
PING 2401:0:4000::50b(2401:0:4000::50b) from 2401:0:4000::50b : 56 data bytes
64 bytes from 2401:0:4000::50b: icmp_seq=1 ttl=64 time=0.077 ms
64 bytes from 2401:0:4000::50b: icmp_seq=2 ttl=64 time=0.053 ms
64 bytes from 2401:0:4000::50b: icmp_seq=3 ttl=64 time=0.040 ms
64 bytes from 2401:0:4000::50b: icmp_seq=4 ttl=64 time=0.051 ms
64 bytes from 2401:0:4000::50b: icmp_seq=5 ttl=64 time=0.041 ms
— 2401:0:4000::50b ping statistics —
5 packets transmitted, 5 packets received, 0% packet loss, time 4043ms
rtt min/avg/max/mdev = 0.040/0.052/0.077/0.014 ms
execute ping6 2401:0:4000::50a
PING 2401:0:4000::50a(2401:0:4000::50a) from 2401:0:4000::50b : 56 data bytes
— 2401:0:4000::50a ping statistics —
5 packets transmitted, 0 packets received, 100% packet loss, time 10013ms
please urgent support required
You’re probably confusing my blog with a support hotline? :D
Hey Muhammad.
Just some ideas:
– It is not recommended to configure /127 networks. You should go for /64 (unless your ISP forces you to use /127).
– Are you pinging from the correct interface? You can set the source interface via “execute ping6-options source”
– Have you verified the NDP cache? (Which is like ARP with IPv4.) That is: Is the MAC address of your default gateway resolved correctly by the FortiGate?
Ciao
Johannes
Hello all,
I played around with IPv6 and DHCPv6 in FortiOS (6.0.13) because I want to send the NTP server information to the clients by the dhcp6 server of the Fortigate.
I share this there maybe someone else can find it with help of Bing, Google and so on.
Now my setting configured like this:
config system dhcp6 server
edit 64
set rapid-commit enable
set lease-time 7200
set domain “ipv6only.nat64.lan”
set subnet 2001:db8:f0:6464::/64
set interface “port3”
set option1 56 ‘0001001020010db800f00002000000000ac30123’ # NTP IPv6 server address 2001:db8:f0:2::ac3:123
set option2 56 ‘00030013013302646504706f6f6c036e7470036f726700’ # IPv6 NTP server hostname (FQDN) 3.de.pool.ntp.org
config ip-range
edit 1
set start-ip 2001:db8:f0:6464::6401
set end-ip 2001:db8:f0:6464::64ff
next
end
set dns-server1 2001:db8:f0:3::53
set dns-server2 2001:db8:f0:8::53
next
end
You can use option1 or option2 or both, depending if you want to publish an ipv6 address or a hostname.
You can publish several hostnames, too. For this I recommend to read (and understand) RFC 5908, chapter 4.3. For me it was a small fight.
@Johannes: If you prefer to have a more detailed post with more details how to create the hex string, please contact me. I can prepare this.