While playing around in my lab learning BGP I configured iBGP with Multiprotocol Extensions (exchanging routing information for IPv6 and legacy IP) between two Cisco routers, a Palo Alto Networks firewall, and a Fortinet FortiGate firewall. Following are all configuration steps from their GUI (Palo) as well as their CLIs (Cisco, Fortinet). It’s just a “basic” lab because I did not configure any possible parameter such as local preference or MED but left almost all to its defaults, except neighboring from loopbacks, password authentication and next-hop-self.
Lab
Some notes about the lab:
- AS number: 64512 (out of the private range, RFC 6996, IANA AS Numbers)
- Neighboring via IPv6 for IPv6-Address-Family and via IPv4 for IPv4-Address-Family for all peers, except between the two Cisco routers that used merely IPv6. Those were the only ones who were able to use this single neighborship for both address families. The Palo Alto does not except using an IPv6 neighbor for IPv4 routes (and vice versa) while the FortiGate accepted the config commands but made wrong routing entries out of it. I don’t know why.
- Neighboring via loopback addresses for Palo and both Cisco routers, but not for the FortiGate. Just to have some variance in the lab.
- MD5 password authentication for all neighbors, except for the IPv4 ones between Palo and both Cisco routers. Again for having some variance.
- The Palo Alto firewall is my gateway to the the Internet. It redistributes its default routes (::/0 and 0.0.0.0/0) to its iBGP neighbors.
- The FortiGate has just one dual-stacked network to propagate.
- Behind the two Cisco routers, named R4 and R5, some more internal routes coming from OSPFv3 for IPv6 and OSPFv2 for legacy IP are redistributed to the other iBGP neighbors as well.
- Those redistributed routes have some variances, too. For IPv6, there are some /64 routes, one aggregated /63 route, one /127 transfer segment, a few /128 loopback addresses, and one aggregated /127 route. Same for IPv4, where an aggregated/summarized /23 exists, as well as /32 host routes, and a /31 aggregated route.
A picture is worth a thousand words. And I have two for you. ;) The first one shows my overall CCNP TSHOOT lab with BGP on the left-hand side, while the second one depicts the BGP settings:
So, let’s dig into the lab.
Cisco Router
Two 2851 routers with IOS 15.1(4)M12a. Note the no bgp default ipv4-unicast command in order to NOT have any neighbors activated for the IPv4 address family by default.
Configuration for R4:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 |
R4#show running-config | section bgp router bgp 64512 bgp router-id 192.168.255.14 bgp log-neighbor-changes no bgp default ipv4-unicast neighbor 2003:DE:2016:120::F02:443 remote-as 64512 neighbor 2003:DE:2016:120::F02:443 description Forti-v6 neighbor 2003:DE:2016:120::F02:443 password 7 012315550A52485E7119 neighbor 2003:DE:2016:1FF::1 remote-as 64512 neighbor 2003:DE:2016:1FF::1 description Palo-v6 Loopback neighbor 2003:DE:2016:1FF::1 password 7 080B4346074A4B4644 neighbor 2003:DE:2016:1FF::1 update-source Loopback0 neighbor 2003:DE:2016:1FF::15 remote-as 64512 neighbor 2003:DE:2016:1FF::15 description R5-Dual Loopback neighbor 2003:DE:2016:1FF::15 password 7 045D04090D205E neighbor 2003:DE:2016:1FF::15 update-source Loopback0 neighbor 192.168.120.33 remote-as 64512 neighbor 192.168.120.33 description Forti-v4 neighbor 192.168.120.33 password 7 0236170A5A5F41701C1B neighbor 192.168.255.1 remote-as 64512 neighbor 192.168.255.1 description Palo-v4 Loopback neighbor 192.168.255.1 update-source Loopback0 ! address-family ipv4 network 192.168.121.0 redistribute ospf 4 match internal external 1 external 2 neighbor 2003:DE:2016:1FF::15 activate neighbor 2003:DE:2016:1FF::15 next-hop-self neighbor 192.168.120.33 activate neighbor 192.168.120.33 next-hop-self neighbor 192.168.255.1 activate neighbor 192.168.255.1 next-hop-self exit-address-family ! address-family ipv6 redistribute ospf 1 match internal external 1 external 2 network 2003:DE:2016:121::/64 neighbor 2003:DE:2016:120::F02:443 activate neighbor 2003:DE:2016:120::F02:443 next-hop-self neighbor 2003:DE:2016:1FF::1 activate neighbor 2003:DE:2016:1FF::1 next-hop-self neighbor 2003:DE:2016:1FF::15 activate neighbor 2003:DE:2016:1FF::15 next-hop-self exit-address-family |
The config for R5 is almost identical:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 |
R5#show running-config | section bgp router bgp 64512 bgp router-id 192.168.255.15 bgp log-neighbor-changes no bgp default ipv4-unicast neighbor 2003:DE:2016:120::F02:443 remote-as 64512 neighbor 2003:DE:2016:120::F02:443 description Forti-v6 neighbor 2003:DE:2016:120::F02:443 password 7 046B18575E78021F594C neighbor 2003:DE:2016:1FF::1 remote-as 64512 neighbor 2003:DE:2016:1FF::1 description Palo-v6 Loopback neighbor 2003:DE:2016:1FF::1 password 7 080B4346074A4B4644 neighbor 2003:DE:2016:1FF::1 update-source Loopback0 neighbor 2003:DE:2016:1FF::14 remote-as 64512 neighbor 2003:DE:2016:1FF::14 description R4-Dual Loopback neighbor 2003:DE:2016:1FF::14 password 7 045D04090D205E neighbor 2003:DE:2016:1FF::14 update-source Loopback0 neighbor 192.168.120.33 remote-as 64512 neighbor 192.168.120.33 description Forti-v4 neighbor 192.168.120.33 password 7 06361C701D1747485542 neighbor 192.168.255.1 remote-as 64512 neighbor 192.168.255.1 description Palo-v4 Loopback neighbor 192.168.255.1 update-source Loopback0 ! address-family ipv4 network 192.168.121.0 redistribute ospf 4 match internal external 1 external 2 neighbor 2003:DE:2016:1FF::14 activate neighbor 2003:DE:2016:1FF::14 next-hop-self neighbor 192.168.120.33 activate neighbor 192.168.120.33 next-hop-self neighbor 192.168.255.1 activate neighbor 192.168.255.1 next-hop-self exit-address-family ! address-family ipv6 redistribute ospf 1 match internal external 1 external 2 network 2003:DE:2016:121::/64 neighbor 2003:DE:2016:120::F02:443 activate neighbor 2003:DE:2016:120::F02:443 next-hop-self neighbor 2003:DE:2016:1FF::1 activate neighbor 2003:DE:2016:1FF::1 next-hop-self neighbor 2003:DE:2016:1FF::14 activate neighbor 2003:DE:2016:1FF::14 next-hop-self exit-address-family |
And this is a bunch of show commands from R4:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 |
R4#show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP + - replicated route, % - next hop override Gateway of last resort is 192.168.120.1 to network 0.0.0.0 S* 0.0.0.0/0 [1/0] via 192.168.120.1 B 192.168.100.0/24 [200/0] via 192.168.120.33, 1d03h 192.168.120.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.120.0/24 is directly connected, GigabitEthernet0/0 L 192.168.120.24/32 is directly connected, GigabitEthernet0/0 192.168.121.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.121.0/24 is directly connected, GigabitEthernet0/1 L 192.168.121.4/32 is directly connected, GigabitEthernet0/1 192.168.122.0/30 is subnetted, 1 subnets O 192.168.122.0 [110/13] via 192.168.121.42, 1d10h, GigabitEthernet0/1 O E2 192.168.124.0/24 [110/20] via 192.168.121.42, 1d10h, GigabitEthernet0/1 O E2 192.168.127.0/24 [110/20] via 192.168.121.42, 1d10h, GigabitEthernet0/1 O E2 192.168.128.0/23 [110/20] via 192.168.121.42, 1d10h, GigabitEthernet0/1 192.168.255.0/24 is variably subnetted, 6 subnets, 2 masks S 192.168.255.1/32 [1/0] via 192.168.120.1, GigabitEthernet0/0 S 192.168.255.2/32 [1/0] via 192.168.120.33, GigabitEthernet0/0 O 192.168.255.11/32 [110/2] via 192.168.121.42, 1d10h, GigabitEthernet0/1 O E2 192.168.255.12/31 [110/20] via 192.168.121.42, 1d07h, GigabitEthernet0/1 C 192.168.255.14/32 is directly connected, Loopback0 S 192.168.255.15/32 [1/0] via 192.168.120.25, GigabitEthernet0/0 R4# R4# R4#show ipv6 route IPv6 Routing Table - default - 17 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea, IS - ISIS summary D - EIGRP, EX - EIGRP external, NM - NEMO, ND - Neighbor Discovery l - LISP O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2 S ::/0 [1/0] via 2003:DE:2016:120::1 B 2003:DE:2016:100::/64 [200/0] via 2003:DE:2016:120::F02:443 C 2003:DE:2016:120::/64 [0/0] via GigabitEthernet0/0, directly connected L 2003:DE:2016:120::24/128 [0/0] via GigabitEthernet0/0, receive C 2003:DE:2016:121::/64 [0/0] via GigabitEthernet0/1, directly connected L 2003:DE:2016:121::4/128 [0/0] via GigabitEthernet0/1, receive O 2003:DE:2016:122::/127 [110/13] via FE80::21E:7AFF:FE79:3F10, GigabitEthernet0/1 OE2 2003:DE:2016:124::/64 [110/20] via FE80::21E:7AFF:FE79:3F10, GigabitEthernet0/1 OE2 2003:DE:2016:127::/64 [110/20] via FE80::21E:7AFF:FE79:3F10, GigabitEthernet0/1 OE2 2003:DE:2016:128::/63 [110/20] via FE80::21E:7AFF:FE79:3F10, GigabitEthernet0/1 S 2003:DE:2016:1FF::1/128 [1/0] via 2003:DE:2016:120::1, GigabitEthernet0/0 S 2003:DE:2016:1FF::2/128 [1/0] via 2003:DE:2016:120::F02:443, GigabitEthernet0/0 O 2003:DE:2016:1FF::11/128 [110/1] via FE80::21E:7AFF:FE79:3F10, GigabitEthernet0/1 OE2 2003:DE:2016:1FF::12/127 [110/20] via FE80::21E:7AFF:FE79:3F10, GigabitEthernet0/1 LC 2003:DE:2016:1FF::14/128 [0/0] via Loopback0, receive S 2003:DE:2016:1FF::15/128 [1/0] via 2003:DE:2016:120::25, GigabitEthernet0/0 L FF00::/8 [0/0] via Null0, receive R4# R4# R4#show bgp all summary For address family: IPv4 Unicast BGP router identifier 192.168.255.14, local AS number 64512 BGP table version is 51, main routing table version 51 10 network entries using 1360 bytes of memory 18 path entries using 1008 bytes of memory 12/7 BGP path/bestpath attribute entries using 1536 bytes of memory 0 BGP route-map cache entries using 0 bytes of memory 0 BGP filter-list cache entries using 0 bytes of memory BGP using 3904 total bytes of memory BGP activity 27/8 prefixes, 130/96 paths, scan interval 60 secs Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd 2003:DE:2016:1FF::15 4 64512 84 84 51 0 0 01:05:28 8 192.168.120.33 4 64512 1911 1846 51 0 0 1d03h 1 192.168.255.1 4 64512 3844 3650 51 0 0 1d03h 1 For address family: IPv6 Unicast BGP router identifier 192.168.255.14, local AS number 64512 BGP table version is 60, main routing table version 60 9 network entries using 1440 bytes of memory 16 path entries using 1280 bytes of memory 10/6 BGP path/bestpath attribute entries using 1280 bytes of memory 0 BGP route-map cache entries using 0 bytes of memory 0 BGP filter-list cache entries using 0 bytes of memory BGP using 4000 total bytes of memory BGP activity 27/8 prefixes, 130/96 paths, scan interval 60 secs Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd 2003:DE:2016:120::F02:443 4 64512 1911 1848 60 0 0 1d03h 1 2003:DE:2016:1FF::1 4 64512 3849 3658 60 0 0 1d03h 1 2003:DE:2016:1FF::15 4 64512 84 84 60 0 0 01:05:28 7 R4# R4# R4#show bgp all For address family: IPv4 Unicast BGP table version is 51, local router ID is 192.168.255.14 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale, m multipath, b backup-path, x best-external, f RT-Filter Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path r>i0.0.0.0 192.168.255.1 100 0 ? *>i192.168.100.0 192.168.120.33 100 0 i * i192.168.120.0 32.3.0.222 0 100 0 ? *> 0.0.0.0 0 32768 ? * i192.168.121.0 32.3.0.222 0 100 0 i *> 0.0.0.0 0 32768 i * i192.168.122.0/30 32.3.0.222 13 100 0 ? *> 192.168.121.42 13 32768 ? * i192.168.124.0 32.3.0.222 20 100 0 ? *> 192.168.121.42 20 32768 ? * i192.168.127.0 32.3.0.222 20 100 0 ? *> 192.168.121.42 20 32768 ? * i192.168.128.0/23 32.3.0.222 20 100 0 ? *> 192.168.121.42 20 32768 ? * i192.168.255.11/32 32.3.0.222 2 100 0 ? *> 192.168.121.42 2 32768 ? * i192.168.255.12/31 32.3.0.222 20 100 0 ? *> 192.168.121.42 20 32768 ? For address family: IPv6 Unicast BGP table version is 60, local router ID is 192.168.255.14 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale, m multipath, b backup-path, x best-external, f RT-Filter Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path r>i::/0 2003:DE:2016:1FF::1 100 0 ? *>i2003:DE:2016:100::/64 2003:DE:2016:120::F02:443 100 0 i * i2003:DE:2016:121::/64 2003:DE:2016:1FF::15 0 100 0 i *> :: 0 32768 i * i2003:DE:2016:122::/127 2003:DE:2016:1FF::15 13 100 0 ? *> FE80::21E:7AFF:FE79:3F10 13 32768 ? * i2003:DE:2016:124::/64 2003:DE:2016:1FF::15 20 100 0 ? *> FE80::21E:7AFF:FE79:3F10 20 32768 ? * i2003:DE:2016:127::/64 2003:DE:2016:1FF::15 20 100 0 ? *> FE80::21E:7AFF:FE79:3F10 20 32768 ? * i2003:DE:2016:128::/63 2003:DE:2016:1FF::15 20 100 0 ? *> FE80::21E:7AFF:FE79:3F10 20 32768 ? * i2003:DE:2016:1FF::11/128 2003:DE:2016:1FF::15 1 100 0 ? *> FE80::21E:7AFF:FE79:3F10 1 32768 ? * i2003:DE:2016:1FF::12/127 2003:DE:2016:1FF::15 20 100 0 ? *> FE80::21E:7AFF:FE79:3F10 20 32768 ? For address family: IPv4 Multicast R4# R4# R4#show bgp ipv4 unicast neighbors 192.168.255.1 BGP neighbor is 192.168.255.1, remote AS 64512, internal link Description: Palo-v4 Loopback BGP version 4, remote router ID 192.168.255.1 BGP state = Established, up for 1d04h Last read 00:00:08, last write 00:00:24, hold time is 90, keepalive interval is 30 seconds Neighbor sessions: 1 active, is not multisession capable (disabled) Neighbor capabilities: Route refresh: advertised and received(new) Four-octets ASN Capability: advertised Address family IPv4 Unicast: advertised and received Graceful Restart Capability: received Remote Restart timer is 120 seconds Address families advertised by peer: IPv4 Unicast (was not preserved) Multisession Capability: Message statistics: InQ depth is 0 OutQ depth is 0 Sent Rcvd Opens: 1 1 Notifications: 0 0 Updates: 6 2 Keepalives: 3663 3862 Route Refresh: 0 0 Total: 3670 3865 Default minimum time between advertisement runs is 0 seconds For address family: IPv4 Unicast Session: 192.168.255.1 BGP table version 51, neighbor version 51/0 Output queue size : 0 Index 2, Advertise bit 0 2 update-group member NEXT_HOP is always this router Slow-peer detection is disabled Slow-peer split-update-group dynamic is disabled Sent Rcvd Prefix activity: ---- ---- Prefixes Current: 8 1 (Consumes 56 bytes) Prefixes Total: 48 1 Implicit Withdraw: 40 0 Explicit Withdraw: 0 0 Used as bestpath: n/a 1 Used as multipath: n/a 0 Outbound Inbound Local Policy Denied Prefixes: -------- ------- Bestpath from this peer: 5 n/a Bestpath from iBGP peer: 4 n/a Invalid Path: 5 n/a Total: 14 0 Number of NLRIs in the update sent: max 5, min 0 Last detected as dynamic slow peer: never Dynamic slow peer recovered: never Address tracking is enabled, the RIB does have a route to 192.168.255.1 Connections established 2; dropped 1 Last reset 1d04h, due to User reset of session 1 Transport(tcp) path-mtu-discovery is enabled Graceful-Restart is disabled Connection state is ESTAB, I/O status: 1, unread input bytes: 0 Connection is ECN Disabled, Mininum incoming TTL 0, Outgoing TTL 255 Local host: 192.168.255.14, Local port: 36390 Foreign host: 192.168.255.1, Foreign port: 179 Connection tableid (VRF): 0 Maximum output segment queue size: 50 Enqueued packets for retransmit: 0, input: 0 mis-ordered: 0 (0 bytes) Event Timers (current time is 0x84DE11C): Timer Starts Wakeups Next Retrans 3666 0 0x0 TimeWait 0 0 0x0 AckHold 3865 3787 0x0 SendWnd 0 0 0x0 KeepAlive 0 0 0x0 GiveUp 0 0 0x0 PmtuAger 99793 99792 0x84DE16B DeadWait 0 0 0x0 Linger 0 0 0x0 ProcessQ 0 0 0x0 iss: 1926740908 snduna: 1926810872 sndnxt: 1926810872 irs: 1109640163 rcvnxt: 1109713663 sndwnd: 15544 scale: 0 maxrcvwnd: 16384 rcvwnd: 16042 scale: 0 delrcvwnd: 342 SRTT: 1000 ms, RTTO: 1003 ms, RTV: 3 ms, KRTT: 0 ms minRTT: 0 ms, maxRTT: 1000 ms, ACK hold: 200 ms Status Flags: active open Option Flags: nagle, path mtu capable IP Precedence value : 6 Datagrams (max data segment is 1460 bytes): Rcvd: 7528 (out of order: 0), with data: 3864, total data bytes: 73499 Sent: 7504 (retransmit: 0, fastretransmit: 0, partialack: 0, Second Congestion: 0), with data: 3665, total data bytes: 69963 Packets received in fast path: 0, fast processed: 0, slow path: 0 fast lock acquisition failures: 0, slow path: 0 R4# R4# R4#show bgp ipv4 unicast neighbors 192.168.255.1 advertised-routes BGP table version is 51, local router ID is 192.168.255.14 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale, m multipath, b backup-path, x best-external, f RT-Filter Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *> 192.168.120.0 0.0.0.0 0 32768 ? *> 192.168.121.0 0.0.0.0 0 32768 i *> 192.168.122.0/30 192.168.121.42 13 32768 ? *> 192.168.124.0 192.168.121.42 20 32768 ? *> 192.168.127.0 192.168.121.42 20 32768 ? *> 192.168.128.0/23 192.168.121.42 20 32768 ? *> 192.168.255.11/32 192.168.121.42 2 32768 ? *> 192.168.255.12/31 192.168.121.42 20 32768 ? Total number of prefixes 8 R4# R4# R4#show bgp ipv4 unicast neighbors 192.168.255.1 routes BGP table version is 51, local router ID is 192.168.255.14 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale, m multipath, b backup-path, x best-external, f RT-Filter Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path r>i0.0.0.0 192.168.255.1 100 0 ? Total number of prefixes 1 R4# |
Palo Alto Networks Firewall
A PA-200 with PAN-OS 8.0.7. Palo Alto Networks offers a great GUI from which BGP can be configured completely. Hence no CLI here but only some show commands later on. I additionally enabled ECMP to have both routes (via R4 and R5) to all the other networks in the FIB.
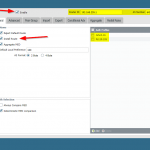
Following are the configuration steps for the Palo:
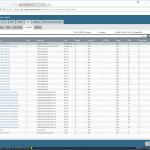
And these are some “show” screenshots, More Runtime Stats:
As well as a bunch of show commands from the CLI:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 370 371 372 373 374 375 376 377 378 379 380 381 382 383 384 385 386 387 388 389 390 391 392 393 394 395 396 397 398 399 400 |
weberjoh@pa> show routing protocol bgp summary ========== router id: 192.168.255.1 virtual router: default reject default route: yes redist default route: allow Install BGP routes: yes Graceful Restart: supported AS size: 2 Local AS: 64512 Local member AS: 0 Cluster id: 0.0.0.0 Default local preference: 100 Always compare MED: no Aggregate regardless MED: yes Deterministic MED processing: yes Accept ORF: no Accept CISCO style prefix: yes mp-bgp-enable: yes afi-safi-ipv4-unicast: yes afi-safi-ipv6-unicast: yes rib-out entries: current 6, peak 6 peer FG100D-v4: AS 64512, Established, IP 192.168.120.33 bgpAfiIpv4/unicast pfx: Accepted pfx: 1, Advertised pfx: 1 peer R4-v4: AS 64512, Established, IP 192.168.255.14 bgpAfiIpv4/unicast pfx: Accepted pfx: 8, Advertised pfx: 1 peer R5-v4: AS 64512, Established, IP 192.168.255.15 bgpAfiIpv4/unicast pfx: Accepted pfx: 8, Advertised pfx: 1 peer FG100D-v6: AS 64512, Established, IP 2003:de:2016:120:0:0:f02:443 bgpAfiIpv6/unicast pfx: Accepted pfx: 1, Advertised pfx: 1 peer R4-v6: AS 64512, Established, IP 2003:de:2016:1ff:0:0:0:14 bgpAfiIpv6/unicast pfx: Accepted pfx: 7, Advertised pfx: 1 peer R5-v6: AS 64512, Established, IP 2003:de:2016:1ff:0:0:0:15 bgpAfiIpv6/unicast pfx: Accepted pfx: 7, Advertised pfx: 1 weberjoh@pa> weberjoh@pa> weberjoh@pa> show routing protocol bgp peer peer-name R4-v4 ========== Peer: R4-v4 (id 7) virtual router: default Peer router id: 192.168.255.14 Remote AS: 64512 Peer group: iBGP-Cisco (id 5) Peer status: Established, for 102376 seconds Password set: no Passive: no Multi-hop TTL: 255 Remote Address: 192.168.255.14:36390 Local Address: 192.168.255.1:179 (R) reflector client: not-client same confederation: no send aggr confed as-path: yes peering type: Unspecified Connect-Retry interval: 15 Open Delay: 0 Idle Hold: 15 Prefix limit: 5000 Holdtime: 90 (config 90) Keep-Alive interval: 30 (config 30) Update messages: in 79, out 8 Total messages: in 36361, out 38249 Last update age: 14 Last error: HoldTimer expired (4) Flap counts: 8, established 4 times (R) ORF entries: 0 Nexthop set to self: yes use 3rd party as next-hop: no override nexthop to peer: no ---------- remove private AS number: no ---------- Capability: Multiprotocol Extensions(1) value: IPv4 Unicast Capability: Route Refresh(yes) Capability: 4-Byte AS Number(65) value: 64512 Capability: Route Refresh (Cisco)(yes) ---------- Prefix counter for: bgpAfiIpv4 / unicast Incoming Prefix: Accepted 8, Rejected 0, Total 8 Outgoing Prefix: 1 Advertised Prefix: 1 weberjoh@pa> weberjoh@pa> weberjoh@pa> show routing protocol bgp peer peer-name R4-v6 ========== Peer: R4-v6 (id 9) virtual router: default Peer router id: 192.168.255.14 Remote AS: 64512 Peer group: iBGP-Cisco (id 5) Peer status: Established, for 102396 seconds Password set: yes Passive: no Multi-hop TTL: 255 Remote Address: 2003:de:2016:1ff:0:0:0:14:65513 Local Address: 2003:de:2016:1ff:0:0:0:1:179 (R) reflector client: not-client same confederation: no send aggr confed as-path: yes peering type: Unspecified Connect-Retry interval: 15 Open Delay: 0 Idle Hold: 15 Prefix limit: 5000 Holdtime: 90 (config 90) Keep-Alive interval: 30 (config 30) Update messages: in 66, out 6 Total messages: in 36353, out 38219 Last update age: 8 Last error: HoldTimer expired (4) Flap counts: 11, established 3 times (R) ORF entries: 0 Nexthop set to self: yes use 3rd party as next-hop: no override nexthop to peer: no ---------- remove private AS number: no ---------- Capability: Multiprotocol Extensions(1) value: IPv6 Unicast Capability: Route Refresh(yes) Capability: 4-Byte AS Number(65) value: 64512 Capability: Route Refresh (Cisco)(yes) ---------- Prefix counter for: bgpAfiIpv6 / unicast Incoming Prefix: Accepted 7, Rejected 0, Total 7 Outgoing Prefix: 1 Advertised Prefix: 1 weberjoh@pa> weberjoh@pa> weberjoh@pa> show routing route virtual-router default flags: A:active, ?:loose, C:connect, H:host, S:static, ~:internal, R:rip, O:ospf, B:bgp, Oi:ospf intra-area, Oo:ospf inter-area, O1:ospf ext-type-1, O2:ospf ext-type-2, E:ecmp, M:multicast VIRTUAL ROUTER: default (id 1) ========== destination nexthop metric flags age interface next-AS 0.0.0.0/0 87.190.30.97 10 A S ethernet1/1 10.49.253.0/24 vr untrust-DSL 10 A S default/i3 10.49.254.0/24 vr untrust-DSL 10 A S default/i3 87.190.30.96/27 87.190.30.104 0 A C ethernet1/1 87.190.30.104/32 0.0.0.0 0 A H 192.168.5.0/24 0.0.0.0 10 A S tunnel.5 192.168.7.0/24 0.0.0.0 10 A S tunnel.7 192.168.9.0/24 0.0.0.0 10 A S tunnel.9 192.168.29.0/24 0.0.0.0 10 A S tunnel.29 192.168.90.0/24 0.0.0.0 10 A S tunnel.90 192.168.100.0/24 192.168.120.33 A?B 1039715 0 192.168.110.0/24 192.168.110.1 0 A C ethernet1/4.110 192.168.110.1/32 0.0.0.0 0 A H 192.168.115.0/24 192.168.110.23 10 A S ethernet1/4.110 192.168.120.0/24 192.168.120.1 0 A C ethernet1/4.120 192.168.120.0/24 192.168.255.14 0 ?B 6187 0 192.168.120.0/24 192.168.255.15 0 ?B 6187 0 192.168.120.1/32 0.0.0.0 0 A H 192.168.121.0/24 192.168.255.14 0 A?B E 6187 0 192.168.121.0/24 192.168.255.15 0 A?B E 6187 0 192.168.122.0/30 192.168.255.14 13 A?B E 6187 0 192.168.122.0/30 192.168.255.15 13 A?B E 6187 0 192.168.123.0/24 192.168.123.1 0 A C ethernet1/3 192.168.123.1/32 0.0.0.0 0 A H 192.168.124.0/24 192.168.255.14 20 A?B E 6187 0 192.168.124.0/24 192.168.255.15 20 A?B E 6187 0 192.168.125.0/24 192.168.125.1 0 A C ethernet1/4.125 192.168.125.1/32 0.0.0.0 0 A H 192.168.126.0/25 192.168.126.0 10 A S tunnel.99 192.168.127.0/24 192.168.255.14 20 A?B E 6187 0 192.168.127.0/24 192.168.255.15 20 A?B E 6187 0 192.168.128.0/23 192.168.255.14 20 A?B E 6187 0 192.168.128.0/23 192.168.255.15 20 A?B E 6187 0 192.168.177.0/24 192.168.177.1 0 A C ethernet1/4.177 192.168.177.1/32 0.0.0.0 0 A H 192.168.255.1/32 0.0.0.0 0 A H 192.168.255.2/32 192.168.120.33 10 A S ethernet1/4.120 192.168.255.11/32 192.168.255.14 2 A?B E 6187 0 192.168.255.11/32 192.168.255.15 2 A?B E 6187 0 192.168.255.12/31 192.168.255.14 20 A?B E 6187 0 192.168.255.12/31 192.168.255.15 20 A?B E 6187 0 192.168.255.14/32 192.168.120.24 10 A S ethernet1/4.120 192.168.255.15/32 192.168.120.25 10 A S ethernet1/4.120 ::/0 2003:de:2016::1 10 A S ethernet1/1 2003:de:2016::/64 2003:de:2016::cafe 0 A C ethernet1/1 2003:de:2016::cafe/128 :: 0 A H 2003:de:2016:100::/64 2003:de:2016:120::f02:443 A?B 1039733 0 2003:de:2016:110::/64 2003:de:2016:110::1 0 A C ethernet1/4.110 2003:de:2016:110::1/128 :: 0 A H 2003:de:2016:115::/64 2003:de:2016:110::d04:443 10 A S ethernet1/4.110 2003:de:2016:120::/64 2003:de:2016:120::1 0 A C ethernet1/4.120 2003:de:2016:120::1/128 :: 0 A H 2003:de:2016:121::/64 2003:de:2016:1ff::14 0 A?B E 6187 0 2003:de:2016:121::/64 2003:de:2016:1ff::15 0 A?B E 6187 0 2003:de:2016:122::/127 2003:de:2016:1ff::14 13 A?B E 6187 0 2003:de:2016:122::/127 2003:de:2016:1ff::15 13 A?B E 6187 0 2003:de:2016:123::/64 2003:de:2016:123::1 0 A C ethernet1/3 2003:de:2016:123::1/128 :: 0 A H 2003:de:2016:124::/64 2003:de:2016:1ff::14 20 A?B E 6187 0 2003:de:2016:124::/64 2003:de:2016:1ff::15 20 A?B E 6187 0 2003:de:2016:125::/64 2003:de:2016:125::1 0 A C ethernet1/4.125 2003:de:2016:125::1/128 :: 0 A H 2003:de:2016:127::/64 2003:de:2016:1ff::14 20 A?B E 6187 0 2003:de:2016:127::/64 2003:de:2016:1ff::15 20 A?B E 6187 0 2003:de:2016:128::/63 2003:de:2016:1ff::14 20 A?B E 6187 0 2003:de:2016:128::/63 2003:de:2016:1ff::15 20 A?B E 6187 0 2003:de:2016:160::/60 :: 10 A S tunnel.3 2003:de:2016:177::/64 2003:de:2016:177::1 0 A C ethernet1/4.177 2003:de:2016:177::1/128 :: 0 A H 2003:de:2016:1ff::1/128 :: 0 A H 2003:de:2016:1ff::2/128 2003:de:2016:120::f02:443 10 A S ethernet1/4.120 2003:de:2016:1ff::11/128 2003:de:2016:1ff::14 1 A?B E 6187 0 2003:de:2016:1ff::11/128 2003:de:2016:1ff::15 1 A?B E 6187 0 2003:de:2016:1ff::12/127 2003:de:2016:1ff::14 20 A?B E 6187 0 2003:de:2016:1ff::12/127 2003:de:2016:1ff::15 20 A?B E 6187 0 2003:de:2016:1ff::14/128 2003:de:2016:120::24 10 A S ethernet1/4.120 2003:de:2016:1ff::15/128 2003:de:2016:120::25 10 A S ethernet1/4.120 total routes shown: 77 weberjoh@pa> weberjoh@pa> weberjoh@pa> show routing route virtual-router default type bgp flags: A:active, ?:loose, C:connect, H:host, S:static, ~:internal, R:rip, O:ospf, B:bgp, Oi:ospf intra-area, Oo:ospf inter-area, O1:ospf ext-type-1, O2:ospf ext-type-2, E:ecmp, M:multicast VIRTUAL ROUTER: default (id 1) ========== destination nexthop metric flags age interface next-AS 192.168.100.0/24 192.168.120.33 A?B 1039721 0 192.168.120.0/24 192.168.255.14 0 ?B 6192 0 192.168.120.0/24 192.168.255.15 0 ?B 6192 0 192.168.121.0/24 192.168.255.14 0 A?B E 6192 0 192.168.121.0/24 192.168.255.15 0 A?B E 6192 0 192.168.122.0/30 192.168.255.14 13 A?B E 6192 0 192.168.122.0/30 192.168.255.15 13 A?B E 6192 0 192.168.124.0/24 192.168.255.14 20 A?B E 6192 0 192.168.124.0/24 192.168.255.15 20 A?B E 6192 0 192.168.127.0/24 192.168.255.14 20 A?B E 6192 0 192.168.127.0/24 192.168.255.15 20 A?B E 6192 0 192.168.128.0/23 192.168.255.14 20 A?B E 6192 0 192.168.128.0/23 192.168.255.15 20 A?B E 6192 0 192.168.255.11/32 192.168.255.14 2 A?B E 6192 0 192.168.255.11/32 192.168.255.15 2 A?B E 6192 0 192.168.255.12/31 192.168.255.14 20 A?B E 6192 0 192.168.255.12/31 192.168.255.15 20 A?B E 6192 0 2003:de:2016:100::/64 2003:de:2016:120::f02:443 A?B 1039739 0 2003:de:2016:121::/64 2003:de:2016:1ff::14 0 A?B E 6192 0 2003:de:2016:121::/64 2003:de:2016:1ff::15 0 A?B E 6192 0 2003:de:2016:122::/127 2003:de:2016:1ff::14 13 A?B E 6192 0 2003:de:2016:122::/127 2003:de:2016:1ff::15 13 A?B E 6192 0 2003:de:2016:124::/64 2003:de:2016:1ff::14 20 A?B E 6192 0 2003:de:2016:124::/64 2003:de:2016:1ff::15 20 A?B E 6192 0 2003:de:2016:127::/64 2003:de:2016:1ff::14 20 A?B E 6192 0 2003:de:2016:127::/64 2003:de:2016:1ff::15 20 A?B E 6192 0 2003:de:2016:128::/63 2003:de:2016:1ff::14 20 A?B E 6192 0 2003:de:2016:128::/63 2003:de:2016:1ff::15 20 A?B E 6192 0 2003:de:2016:1ff::11/128 2003:de:2016:1ff::14 1 A?B E 6192 0 2003:de:2016:1ff::11/128 2003:de:2016:1ff::15 1 A?B E 6192 0 2003:de:2016:1ff::12/127 2003:de:2016:1ff::14 20 A?B E 6192 0 2003:de:2016:1ff::12/127 2003:de:2016:1ff::15 20 A?B E 6192 0 total routes shown: 32 weberjoh@pa> weberjoh@pa> weberjoh@pa> show routing fib virtual-router default total virtual-router shown : 1 -------------------------------------------------------------------------------- virtual-router name: default interfaces: ethernet1/1 ethernet1/3 ethernet1/4.110 ethernet1/4.120 ethernet1/4.125 ethernet1/4.177 loopback.1 tunnel.3 tunnel.5 tunnel.7 tunnel.9 tunnel.29 tunnel.90 tunnel.99 route table: flags: u - up, h - host, g - gateway, e - ecmp, * - preferred path maximum of fib entries for device: 1000 maximum of IPv4 fib entries for device: 1000 maximum of IPv6 fib entries for device: 1000 number of fib entries for device: 81 maximum of fib entries for this fib: 1000 number of fib entries for this fib: 41 number of fib entries shown: 41 id destination nexthop flags interface mtu -------------------------------------------------------------------------------- 61 0.0.0.0/0 87.190.30.97 ug ethernet1/1 1500 34 10.49.253.0/24 untrust-DSL u default/i3 0 33 10.49.254.0/24 untrust-DSL u default/i3 0 60 87.190.30.96/27 0.0.0.0 u ethernet1/1 1500 59 87.190.30.104/32 0.0.0.0 uh ethernet1/1 1500 32 192.168.5.0/24 0.0.0.0 u tunnel.5 1500 28 192.168.7.0/24 0.0.0.0 u tunnel.7 1500 31 192.168.9.0/24 0.0.0.0 u tunnel.9 1500 30 192.168.29.0/24 0.0.0.0 u tunnel.29 1500 29 192.168.90.0/24 0.0.0.0 u tunnel.90 1500 86 192.168.100.0/24 192.168.120.33 ug ethernet1/4.120 1500 63 192.168.110.0/24 0.0.0.0 u ethernet1/4.110 1500 62 192.168.110.1/32 0.0.0.0 uh ethernet1/4.110 1500 64 192.168.115.0/24 192.168.110.23 ug ethernet1/4.110 1500 66 192.168.120.0/24 0.0.0.0 u ethernet1/4.120 1500 286 192.168.121.0/24 192.168.120.24 uge ethernet1/4.120 1500 286 192.168.121.0/24 192.168.120.25 uge* ethernet1/4.120 1500 110 192.168.123.0/24 0.0.0.0 u ethernet1/3 1500 0 192.168.124.0/24 192.168.120.24 uge ethernet1/4.120 1500 0 192.168.124.0/24 192.168.120.25 uge* ethernet1/4.120 1500 71 192.168.125.0/24 0.0.0.0 u ethernet1/4.125 1500 288 192.168.127.0/24 192.168.120.24 uge ethernet1/4.120 1500 288 192.168.127.0/24 192.168.120.25 uge* ethernet1/4.120 1500 65 192.168.120.1/32 0.0.0.0 uh ethernet1/4.120 1500 287 192.168.122.0/30 192.168.120.24 uge ethernet1/4.120 1500 287 192.168.122.0/30 192.168.120.25 uge* ethernet1/4.120 1500 109 192.168.123.1/32 0.0.0.0 uh ethernet1/3 1500 70 192.168.125.1/32 0.0.0.0 uh ethernet1/4.125 1500 39 192.168.126.0/25 192.168.126.0 ug tunnel.99 1500 321 192.168.128.0/23 192.168.120.24 uge ethernet1/4.120 1500 321 192.168.128.0/23 192.168.120.25 uge* ethernet1/4.120 1500 73 192.168.177.0/24 0.0.0.0 u ethernet1/4.177 1500 72 192.168.177.1/32 0.0.0.0 uh ethernet1/4.177 1500 13 192.168.255.1/32 0.0.0.0 uh loopback.1 1500 67 192.168.255.2/32 192.168.120.33 ug ethernet1/4.120 1500 327 192.168.255.12/31 192.168.120.24 uge ethernet1/4.120 1500 327 192.168.255.12/31 192.168.120.25 uge* ethernet1/4.120 1500 290 192.168.255.11/32 192.168.120.24 uge ethernet1/4.120 1500 290 192.168.255.11/32 192.168.120.25 uge* ethernet1/4.120 1500 68 192.168.255.14/32 192.168.120.24 ug ethernet1/4.120 1500 69 192.168.255.15/32 192.168.120.25 ug ethernet1/4.120 1500 -------------------------------------------------------------------------------- --------------------------------------------------------------------------------------------------------------------------- virtual-router name: default interfaces: ethernet1/1 ethernet1/3 ethernet1/4.110 ethernet1/4.120 ethernet1/4.125 ethernet1/4.177 loopback.1 tunnel.3 tunnel.5 tunnel.7 tunnel.9 tunnel.29 tunnel.90 tunnel.99 route table: flags: u - up, h - host, g - gateway, e - ecmp, * - preferred path maximum of fib entries for device: 1000 maximum of IPv4 fib entries for device: 1000 maximum of IPv6 fib entries for device: 1000 number of fib entries for device: 81 maximum of fib entries for this fib: 1000 number of fib entries for this fib: 34 number of fib entries shown: 34 id destination nexthop flags interface mtu --------------------------------------------------------------------------------------------------------------------------- 47 0:0:0:0:0:0:0:0/0 2003:de:2016::1 ug ethernet1/1 1500 46 2003:de:2016:0:0:0:0:0/64 :: u ethernet1/1 1500 45 2003:de:2016:0:0:0:0:cafe/128 :: uh ethernet1/1 1500 21 2003:de:2016:160:0:0:0:0/60 :: u tunnel.3 1500 70 2003:de:2016:100:0:0:0:0/64 2003:de:2016:120::f02:443 ug ethernet1/4.120 1500 49 2003:de:2016:110:0:0:0:0/64 :: u ethernet1/4.110 1500 50 2003:de:2016:115:0:0:0:0/64 2003:de:2016:110::d04:443 ug ethernet1/4.110 1500 48 2003:de:2016:110:0:0:0:1/128 :: uh ethernet1/4.110 1500 52 2003:de:2016:120:0:0:0:0/64 :: u ethernet1/4.120 1500 322 2003:de:2016:121:0:0:0:0/64 2003:de:2016:120::24 uge ethernet1/4.120 1500 322 2003:de:2016:121:0:0:0:0/64 2003:de:2016:120::25 uge* ethernet1/4.120 1500 94 2003:de:2016:123:0:0:0:0/64 :: u ethernet1/3 1500 331 2003:de:2016:124:0:0:0:0/64 2003:de:2016:120::24 uge ethernet1/4.120 1500 331 2003:de:2016:124:0:0:0:0/64 2003:de:2016:120::25 uge* ethernet1/4.120 1500 57 2003:de:2016:125:0:0:0:0/64 :: u ethernet1/4.125 1500 324 2003:de:2016:127:0:0:0:0/64 2003:de:2016:120::24 uge ethernet1/4.120 1500 324 2003:de:2016:127:0:0:0:0/64 2003:de:2016:120::25 uge* ethernet1/4.120 1500 51 2003:de:2016:120:0:0:0:1/128 :: uh ethernet1/4.120 1500 323 2003:de:2016:122:0:0:0:0/127 2003:de:2016:120::24 uge ethernet1/4.120 1500 323 2003:de:2016:122:0:0:0:0/127 2003:de:2016:120::25 uge* ethernet1/4.120 1500 93 2003:de:2016:123:0:0:0:1/128 :: uh ethernet1/3 1500 56 2003:de:2016:125:0:0:0:1/128 :: uh ethernet1/4.125 1500 0 2003:de:2016:128:0:0:0:0/63 2003:de:2016:120::24 uge ethernet1/4.120 1500 0 2003:de:2016:128:0:0:0:0/63 2003:de:2016:120::25 uge* ethernet1/4.120 1500 59 2003:de:2016:177:0:0:0:0/64 :: u ethernet1/4.177 1500 58 2003:de:2016:177:0:0:0:1/128 :: uh ethernet1/4.177 1500 13 2003:de:2016:1ff:0:0:0:1/128 :: uh loopback.1 1500 53 2003:de:2016:1ff:0:0:0:2/128 2003:de:2016:120::f02:443 ug ethernet1/4.120 1500 0 2003:de:2016:1ff:0:0:0:12/127 2003:de:2016:120::24 uge ethernet1/4.120 1500 0 2003:de:2016:1ff:0:0:0:12/127 2003:de:2016:120::25 uge* ethernet1/4.120 1500 326 2003:de:2016:1ff:0:0:0:11/128 2003:de:2016:120::24 uge ethernet1/4.120 1500 326 2003:de:2016:1ff:0:0:0:11/128 2003:de:2016:120::25 uge* ethernet1/4.120 1500 54 2003:de:2016:1ff:0:0:0:14/128 2003:de:2016:120::24 ug ethernet1/4.120 1500 55 2003:de:2016:1ff:0:0:0:15/128 2003:de:2016:120::25 ug ethernet1/4.120 1500 --------------------------------------------------------------------------------------------------------------------------- weberjoh@pa> |
Fortinet FortiGate Firewall
An FG-100D with firmware v5.6.3. The GUI from Fortinet concerning BGP is completely useless. You can only configure the mere neighbors via IPv4, but no IPv6, no address families, no password, and all the other stuff. Everything must be done via the CLI. (Why is this called a next generation firewall?)
This is the config. Note the set ibgp-multipath enable command in the beginning to have those equal routes via R4 and R5 in the routing table again:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 |
config router bgp set as 64512 set router-id 192.168.255.2 set ibgp-multipath enable config neighbor edit "2003:de:2016:120::24" set activate disable set next-hop-self6 enable set remote-as 64512 set password ENC uSYvRjLrl44R/OyblhLdUmUjG9/8y7/e9zmFmjNYoVRg4lTDQdMWu0+wY2f6v69KHTpQj1RQUw0K/0Nwq75sTc8pQuxZnPGIJHM3dtJTfPcQZ9vsvviR5hYRSR6DJlfbHII0Kv+YGRTXAVBZkmkpXohsNI32V3iVXTp6Xd96fJwCgoO4s1am1Tje8+NmV/owDgavEg== next edit "2003:de:2016:120::25" set activate disable set next-hop-self6 enable set remote-as 64512 set password ENC opDMzuT3VKmMCzL/PY70+9fn9K/xPs7KBJ6kqDZ/JPbjOUCXPun2R+8hRSe1AoLbeBE/zeShp6lBnhEBG61kjZ6HLSSHLbgf7JmWC0dmF4CnoCIApAH1e/pa0QZ2CXMJRSpcG98LAqwk8mReTUz/pjkgl8ft2Q6XkA9O1rGpoQnbXyJNRLcmQ9p1Sagp1kiEKARRQg== next edit "192.168.120.24" set activate6 disable set next-hop-self enable set remote-as 64512 set password ENC wTuWbiTUWPzy8+BnfaiATnfLPz+8uSOqJNwL22VrIBfwf6r7MtU8rR5KxR1cLwkvnHfYVuL6/XLzH8ZHFXML7x6clE8JQPEQLY704g55K5ydGQ5WWrtYxuNRX/nAPUVs6PLobqkmAgnGIh2TOajCrjm5eawIODhBbMzoGV2C9FLMBUqSOU5GFb15abvVbF6dZ/Kx/Q== next edit "192.168.120.25" set activate6 disable set next-hop-self enable set remote-as 64512 set password ENC 24TWnVPrRyNeiM30OdktPYjjUBeosFUqOx8SV+I6EHMH4Di/weInDyAzPhAO9eo0/TxDjR2LDLq9B6p0Tdo62a/EdmDxW+PaWg2xX28Ws9Z0215d5gL6ZkYwT1YpZnH5+sbv6cedAEhqiZk8Fet42g/DmTMtycKK7S3u0rurjMwoklqNgsR8eP1QcJoOshYQHJwkWA== next edit "192.168.120.1" set activate6 disable set next-hop-self enable set remote-as 64512 set password ENC BVCfc9xgXb7MI8pkVBW2xGXKj8Ly08KpL1gWKCUXsKnGeU06Ng1A/hX/zEx4Iq3Yjr6VyqGBud86D2OMqvCizg1KpP0Jp4BcLleYxmnoip03nnlQBJWjZB8SJbe3XjwrZ2p39KuS4MTb9gzLRSxTfHobDJuqWuUH9/oOVpmqKXouUATs0mtgbv53qGDdWY+mysaJSQ== next edit "2003:de:2016:120::1" set activate disable set next-hop-self6 enable set remote-as 64512 set password ENC VPlHANfBLIsa0XWyvhwrQAzpOTd0kfh+93C3nteWXSgVlKrk2IxKtyLZ3emt9RThBddAb4y1Qwacz7JI+qYi+gK0T6BZYRGEiLw+jnv81enWCw0ZJsChLpGkQA+Cv0mUE8pw37+mz7ws/rPybtujrLuJMeXmUqWyTeYvZ4E/e7s1ZoFR5nRUs2i/9jYBInDIHa2H7w== next end config network edit 1 set prefix 192.168.100.0 255.255.255.0 next end config network6 edit 1 set prefix6 2003:de:2016:100::/64 next end end |
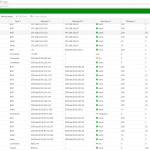
At least the GUI can be used to have a look at the routing table. :P The default routes are learned via BGP, as well as many other routes that are load-shared over R4 and R5:
Much more information can be monitored through the CLI of course:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 |
fg # get router info routing-table all Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default B* 0.0.0.0/0 [200/0] via 192.168.120.1, wan1, 01w5d01h C 192.168.100.0/24 is directly connected, lan C 192.168.120.0/24 is directly connected, wan1 B 192.168.121.0/24 [200/0] via 192.168.120.25, wan1, 01:58:48 [200/0] via 192.168.120.24, wan1, 01:58:48 B 192.168.122.0/30 [200/13] via 192.168.120.25, wan1, 01:58:48 [200/13] via 192.168.120.24, wan1, 01:58:48 B 192.168.124.0/24 [200/20] via 192.168.120.25, wan1, 01:58:48 [200/20] via 192.168.120.24, wan1, 01:58:48 B 192.168.127.0/24 [200/20] via 192.168.120.25, wan1, 01:58:48 [200/20] via 192.168.120.24, wan1, 01:58:48 B 192.168.128.0/23 [200/20] via 192.168.120.25, wan1, 01:58:48 [200/20] via 192.168.120.24, wan1, 01:58:48 S 192.168.255.1/32 [10/0] via 192.168.120.1, wan1 C 192.168.255.2/32 is directly connected, loopback1 B 192.168.255.11/32 [200/2] via 192.168.120.25, wan1, 01:58:48 [200/2] via 192.168.120.24, wan1, 01:58:48 B 192.168.255.12/31 [200/20] via 192.168.120.25, wan1, 01:58:48 [200/20] via 192.168.120.24, wan1, 01:58:48 S 192.168.255.14/32 [10/0] via 192.168.120.24, wan1 S 192.168.255.15/32 [10/0] via 192.168.120.25, wan1 fg # fg # fg # get router info6 routing-table IPv6 Routing Table Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 I - IS-IS, B - BGP * - candidate default Timers: Uptime B* ::/0 [200/0] via 2003:de:2016:120::1, wan1, 01w5d01h C ::1/128 via ::, root, 02w3d10h C 2003:de:2016:100::/64 via ::, lan, 02w3d04h C 2003:de:2016:120::/64 via ::, wan1, 02w3d05h B 2003:de:2016:121::/64 [200/0] via 2003:de:2016:120::25, wan1, 01:59:12 [200/0] via 2003:de:2016:120::24, wan1, 01:59:12 B 2003:de:2016:122::/127 [200/13] via 2003:de:2016:120::25, wan1, 01:59:12 [200/13] via 2003:de:2016:120::24, wan1, 01:59:12 B 2003:de:2016:124::/64 [200/20] via 2003:de:2016:120::25, wan1, 01:59:12 [200/20] via 2003:de:2016:120::24, wan1, 01:59:12 B 2003:de:2016:127::/64 [200/20] via 2003:de:2016:120::25, wan1, 01:59:12 [200/20] via 2003:de:2016:120::24, wan1, 01:59:12 B 2003:de:2016:128::/63 [200/20] via 2003:de:2016:120::25, wan1, 01:59:12 [200/20] via 2003:de:2016:120::24, wan1, 01:59:12 S 2003:de:2016:1ff::1/128 [10/0] via 2003:de:2016:120::1, wan1, 02w0d09h C 2003:de:2016:1ff::2/128 via ::, loopback1, 02w0d11h B 2003:de:2016:1ff::11/128 [200/1] via 2003:de:2016:120::25, wan1, 01:59:12 [200/1] via 2003:de:2016:120::24, wan1, 01:59:12 B 2003:de:2016:1ff::12/127 [200/20] via 2003:de:2016:120::25, wan1, 01:59:12 [200/20] via 2003:de:2016:120::24, wan1, 01:59:12 S 2003:de:2016:1ff::14/128 [10/0] via 2003:de:2016:120::24, wan1, 02w0d09h S 2003:de:2016:1ff::15/128 [10/0] via 2003:de:2016:120::25, wan1, 02w0d09h C fe80::/64 via ::, lan, 02w3d04h K ff00::/8 via ::, wan1, 02w3d10h fg # fg # fg # get router bgp as : 64512 router-id : 192.168.255.2 keepalive-timer : 60 holdtime-timer : 180 always-compare-med : disable bestpath-as-path-ignore: disable bestpath-cmp-confed-aspath: disable bestpath-cmp-routerid: disable bestpath-med-confed : disable bestpath-med-missing-as-worst: disable client-to-client-reflection: enable dampening : disable deterministic-med : disable ebgp-multipath : disable ibgp-multipath : enable enforce-first-as : enable fast-external-failover: enable log-neighbour-changes: enable network-import-check: enable ignore-optional-capability: enable cluster-id : 0.0.0.0 confederation-identifier: 0 default-local-preference: 100 scan-time : 60 distance-external : 20 distance-internal : 200 distance-local : 200 synchronization : disable graceful-restart : disable aggregate-address: aggregate-address6: neighbor: == [ 2003:de:2016:120::24 ] ip: 2003:de:2016:120::24 == [ 2003:de:2016:120::25 ] ip: 2003:de:2016:120::25 == [ 192.168.120.24 ] ip: 192.168.120.24 == [ 192.168.120.25 ] ip: 192.168.120.25 == [ 192.168.120.1 ] ip: 192.168.120.1 == [ 2003:de:2016:120::1 ] ip: 2003:de:2016:120::1 neighbor-group: neighbor-range: network: == [ 1 ] id: 1 network6: == [ 1 ] id: 1 redistribute: == [ connected ] name: connected status: disable route-map: == [ rip ] name: rip status: disable route-map: == [ ospf ] name: ospf status: disable route-map: == [ static ] name: static status: disable route-map: == [ isis ] name: isis status: disable route-map: redistribute6: == [ connected ] name: connected status: disable route-map: == [ rip ] name: rip status: disable route-map: == [ ospf ] name: ospf status: disable route-map: == [ static ] name: static status: disable route-map: == [ isis ] name: isis status: disable route-map: admin-distance: fg # fg # fg # get router info bgp summary BGP router identifier 192.168.255.2, local AS number 64512 BGP table version is 32 1 BGP AS-PATH entries 0 BGP community entries Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd 192.168.120.1 4 64512 54701 54382 24 0 0 01w5d01h 1 192.168.120.24 4 64512 26306 27227 28 0 0 1d04h45m 8 192.168.120.25 4 64512 26319 27204 31 0 0 02:00:39 8 Total number of neighbors 3 fg # fg # fg # get router info6 bgp summary BGP router identifier 192.168.255.2, local AS number 64512 BGP table version is 39 1 BGP AS-PATH entries 0 BGP community entries Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd 2003:de:2016:120::1 4 64512 54766 54389 28 0 0 01w5d01h 1 2003:de:2016:120::24 4 64512 27385 28330 32 0 0 1d04h49m 7 2003:de:2016:120::25 4 64512 27273 28198 37 0 0 02:05:05 7 Total number of neighbors 3 fg # fg # fg # get router info bgp neighbors 192.168.120.24 BGP neighbor is 192.168.120.24, remote AS 64512, local AS 64512, internal link BGP version 4, remote router ID 192.168.255.14 BGP state = Established, up for 00:04:33 Last read 00:00:22, hold time is 180, keepalive interval is 60 seconds Configured hold time is 180, keepalive interval is 60 seconds Neighbor capabilities: Route refresh: advertised and received (old and new) Address family IPv4 Unicast: advertised and received Received 26320 messages, 0 notifications, 0 in queue Sent 27235 messages, 3 notifications, 0 in queue Route refresh request: received 0, sent 0 Minimum time between advertisement runs is 30 seconds For address family: IPv4 Unicast BGP table version 34, neighbor version 32 Index 1, Offset 0, Mask 0x2 NEXT_HOP is always this router Community attribute sent to this neighbor (both) 8 accepted prefixes 1 announced prefixes Connections established 8; dropped 7 Local host: 192.168.120.33, Local port: 2715 Foreign host: 192.168.120.24, Foreign port: 179 Nexthop: 192.168.120.33 Nexthop global: 2003:de:2016:120::f02:443 Nexthop local: fe80::926c:acff:fe07:58b0 BGP connection: non shared network Last Reset: 00:04:39, due to BGP Notification sent Notification Error Message: (CeaseUnspecified Error Subcode) fg # fg # fg # get router info bgp neighbors 192.168.120.24 advertised-routes BGP table version is 34, local router ID is 192.168.255.2 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *>i192.168.100.0 192.168.120.33 100 32768 i Total number of prefixes 1 fg # fg # fg # get router info bgp neighbors 192.168.120.24 routes BGP table version is 34, local router ID is 192.168.255.2 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, S Stale Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path * i192.168.120.0 192.168.120.24 0 100 0 ? * i192.168.121.0 192.168.120.24 0 100 0 i * i192.168.122.0/30 192.168.120.24 13 100 0 ? * i192.168.124.0 192.168.120.24 20 100 0 ? * i192.168.127.0 192.168.120.24 20 100 0 ? * i192.168.128.0/23 192.168.120.24 20 100 0 ? * i192.168.255.11/32 192.168.120.24 2 100 0 ? * i192.168.255.12/31 192.168.120.24 20 100 0 ? Total number of prefixes 8 fg # fg # fg # get router info6 bgp neighbors 2003:de:2016:120::1 BGP neighbor is 2003:de:2016:120::1, remote AS 64512, local AS 64512, internal link BGP version 4, remote router ID 192.168.255.1 BGP state = Established, up for 01w5d01h Last read 00:00:14, hold time is 90, keepalive interval is 30 seconds Configured hold time is 180, keepalive interval is 60 seconds Neighbor capabilities: Route refresh: advertised and received (old and new) Address family IPv6 Unicast: advertised and received Received 54744 messages, 28 notifications, 0 in queue Sent 54392 messages, 3 notifications, 0 in queue Route refresh request: received 0, sent 0 Minimum time between advertisement runs is 30 seconds For address family: IPv6 Unicast BGP table version 39, neighbor version 28 Index 5, Offset 0, Mask 0x20 Graceful restart: received NEXT_HOP is always this router Community attribute sent to this neighbor (both) 1 accepted prefixes 1 announced prefixes Connections established 6; dropped 5 Local host: 2003:de:2016:120::f02:443, Local port: 179 Foreign host: 2003:de:2016:120::1, Foreign port: 50013 Nexthop: 192.168.255.2 Nexthop global: 2003:de:2016:120::f02:443 Nexthop local: fe80::926c:acff:fe07:58b0 BGP connection: shared network Last Reset: 01w5d01h, due to BGP Notification sent Notification Error Message: (Hold Timer Expired/Unspecified Error Subcode) fg # fg # fg # get router info6 bgp neighbors 2003:de:2016:120::1 advertised-routes BGP table version is 39, local router ID is 192.168.255.2 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *>i2003:de:2016:100::/64 2003:de:2016:120::f02:443(fe80::926c:acff:fe07:58b0) 100 32768 i Total number of prefixes 1 fg # fg # fg # get router info6 bgp neighbors 2003:de:2016:120::1 routes BGP table version is 39, local router ID is 192.168.255.2 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, S Stale Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *>i::/0 2003:de:2016:120::1 0 100 0 ? Total number of prefixes 1 fg # fg # |
Haha, a lot of stuff. ;) Ciao.
Featured image “Himmlischer Wegweiser/Heavenly fingerpost” by Frank Müller is licensed under CC BY-NC 2.0.