In my last blogpost I showed how to perform a DNSSEC KSK rollover. I did it quite slowly and carefully. This time I am looking into an emergency rollover of the KSK. That is: What to do if your KSK is compromised and you must replace it IMMEDIATELY.
I am listing the procedures and commands I used to replace the KSK of my delegated subdomain dyn.weberdns.de with BIND. And, as you might already suggested, I am showing DNSViz graphs after every step since it greatly reveals the current DNSKEYs etc.
RFC 6781, “DNSSEC Operational Practices, Version 2”, describes all steps in case of a KSK compromise in section 4.2.1. There are two methods how to replace a compromised KSK, by either breaking the chain of trust or by keeping it intact. I decided to train the “Emergency Key Rollover Keeping the Chain of Trust Intact” version. This is basically the same as the normal “Double-Signature KSK rollover” described in section 4.1.2. That is:
- introduce a new KSK (so that both KSKs sign the ZSK),
- upload the new DS to the parent to replace (!) the DS record immediately,
- wait until the TTL of the old DS record expires,
- and remove the old KSK from your zone.
That is, there are two time critical things to keep in mind:
- Since you must transfer the new DS record to your parent zone, you must wait until they publish it. If you can use an API, you’re lucky. If you must send it manually via mail and must wait for a human response, you’re not lucky…
- You must wait until the TTL of the old DS record times out.

In my scenario I trained the emergency KSK rollover on one of my own delegated zones, dyn.weberdns.de. That is: I am controlling the actual zone as well as the parent zone. Good prerequisite for testing purposes. ;) Furthermore my TTL for the DS record was set to 3600 s = 1 h. Hence I was able to rollover (and delete) the compromised DNSKEY within one hour!
It was Friday evening, 2018-03-02. All times are noted as UTC.
19:33: Shit, my KSK for dyn.weberdns.de is compromised!
I was informed that the DNSKEY type 257 (KSK) for my very own zone was compromised. I immediately decided to do an emergency KSK rollover!
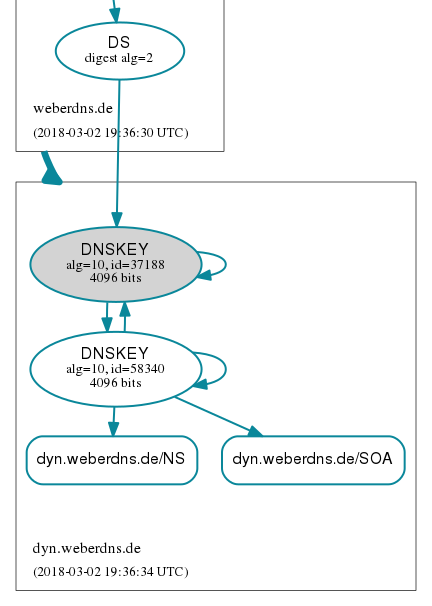
At this point DNSViz shows the single DS, a single KSK (grey, 37188) and a single ZSK (white, 58340) for the zone:
19:38: Generating a new KSK
I generated a new KSK for the zone (and corrected the ownership to be readable by BIND, as always):
|
1 2 3 |
cd /etc/bind/keys/ sudo dnssec-keygen -a RSASHA512 -b 4096 -3 -f KSK -r /dev/urandom dyn.weberdns.de sudo chown bind:bind * |
Here you can see the new KSK with ID 45918, along with its dates in UTC+1:
|
1 2 3 4 5 6 |
weberjoh@vm16-ns0:/etc/bind/keys$ cat Kdyn.weberdns.de.+010+45918.key ; This is a key-signing key, keyid 45918, for dyn.weberdns.de. ; Created: 20180302193814 (Fri Mar 2 20:38:14 2018) ; Publish: 20180302193814 (Fri Mar 2 20:38:14 2018) ; Activate: 20180302193814 (Fri Mar 2 20:38:14 2018) dyn.weberdns.de. IN DNSKEY 257 3 10 AwEAAcD4vC7bqZKvApZIOXkuH++bXUBVf5XJj1oQvYn7i3XjLmoCtOs7 JyxElo4PeDnGIa4coAxBTHj4B+iVSa4nTJ5MK2lvEQVtwr8Pr+ZKOlYK mRs+SeRI1ZGN0OyBpQv/TxPqZBN8V9RegsJ/adM9Rn5B96Be/hrMFzmk zd0iK2L9I2TTAPl3YDfZ5vCQzdAMEZG9G56dfZK0GRgebCu3LHQvD7Wx +/P4CfUknOydZqmu0geww4VRUyveGUY+PLamJGieG6QopoTtuu5V+DJb jSA+mDPAfIW993iAw2TqMuD4tBhaQ6HSmAA7FHydrq4fcqtuC+QxZaqA hQIEp93L6JM9xcl0dY5m+OvqjCVBk/X7xRvpW1Xni3pEWs0wMcYfoeVe gXXXw42123kEypd/78h0H7Y9AD5WVNnVnG2M/J0M1eVmsiyB7xGvyLeF MBGPiuj0YN2bESnsR9A0tGUqgwHKtWcZwcLJYqO/r6Ahp0wYqwcqJ2uw volEjzGUrBOSY7fe4blauqnTsECWeHDpuOd3Hs+IupSYTIsyFnuI6oFN aSjiD5a2z7KN25TjpNzYRbcbjnN1J4NabLvziGFwF+ZfSSI1TavipCg2 1MczJ8FJVZPeHIdIFMyt0d5JSL4a/iyHiaRtLw0N8GjCLDQvS57hJ0J/ uQFFo0lPCIUy/iFH |
After the creation I signed the zone again, which immediately uses the new key as well:
|
1 |
sudo rndc sign dyn.weberdns.de |
That is, querying the nameserver directly (and not a caching nameserver) revealed three DNSKEYs (2x KSK, 1x ZSK) along with its three RRSIGs over the DNSKEY resource record set:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 |
weberjoh@nb15-lx:~$ dig dyn.weberdns.de dnskey +multi +dnssec @ns1.weberdns.de ; <<>> DiG 9.10.3-P4-Ubuntu <<>> dyn.weberdns.de dnskey +multi +dnssec @ns1.weberdns.de ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 41271 ;; flags: qr aa rd; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;dyn.weberdns.de. IN DNSKEY ;; ANSWER SECTION: dyn.weberdns.de. 60 IN DNSKEY 256 3 10 ( AwEAAbiC3omZWzDtVx/nlwIEEgY1wrAQktqggJXNq50U +Xapj2+RQE4s7dNLU7AtJ+jvr/nplax61coz/2Na9YEc RE1LGpcZdrFH3iDZez+UcOY1GPll5xPGgpSPtSaL1j8M fUQgAw85ZmFQ6rUptYOpa3/w40n3MrgiOFyu8IoXhP7O QKICmHFAVcB6nurPZK6m52Vny/5R7CtHBmxGyU/Xcm6D oimWZPj56+QeQbthiPdSLNYNB8QoLWTPEuzjLdFaz7Jv Bp1n0tdqPS27OErcWV4eja6as1OyTODreo0b0pkM6Ulp 4xkY/7A/VbVFv9l/bHTIVFW/jXisk6Yr2/LwVy58/lGj oJ9SfpJnnelxYo0HMbp8zsQ2xGNzvH783NXsc0LeIATl WeBJrkW3hL4rJFc/5rT71RwHveukofFjXjk008Sgj1TD 6Gyx6I4XVi8AcbhTNajfh4K+elZMnJRnewQqk4g5KYBi ucyX0gR+JNSejqD4+mWuIyzKTh+cMrUsIBkXYQRzwlRf S8A0Zs9eVAQXVlKVgPEorj7fp1hnn6Ao8A2P7MeO5pdg ilFpSEIW3IbwtKqjPWY7wvVOo9Ms2TCdgePC34xxKGub gNQTBGU9MSlg16K2kvCavSYAgzQRUfzKtknPowr0ODz/ sBNRLH2swqvxU1rkkjZlS3RbW6+n ) ; ZSK; alg = RSASHA512; key id = 58340 dyn.weberdns.de. 60 IN DNSKEY 257 3 10 ( AwEAAeHRfPp41nJWSleIHZzNtM1il8wZQ4X5M/zLUb2h a3PoZoonfAQGRg2DOYHApp46kJY0VvPQee7OWNjSuKcG tJHCcgbm33LUJFGkNKRhTMsCufmLNt1xiwuKaukhQoLi Z8S2sYVgttpS4SSQW0gI8zaR13AaCD+VidIc5GzpFN4Y VniYjPDzk+e9zRai5ziEMMoWvj/BakgZ6oDwsHwkIDD3 vW4yGnO+Dz8A4AnU8hdXei3wNI5CObUqEoVlx45aiziE u8/RAEh2lZOZZnAtwkbSyjNH5dsGuLzwAcrzN/7W9fIp QIF7h42c1UQT6MmkuRs87+oQBRkhMpWNokKs9NjeiA6s dVDqvKmxsT/smrFqDFPqlcyu+KtnVbRV7VcerWcTlFzH Kw8RiTq6lnUWXqGTm9CKBvWwAZ/iMoE74kVFAo399jQI fId3sSV/Nf2YgsQezswh+N92LFG0pl31ZWqJrisjCFrm 2VA3KOWZ7i0eCpW2TbKJgy/ROeztMVx/+LNnVjs0DaJX NrH0oxqQjOANLwuIkoV+2zBZcY22kID1sWo7sLCZYR5u kkeHVosGvtm8Bo3Gaga4lYqr+BrUr41uIr8o1AwWTN5k TxJeilXRv3fx+Z/LdYlPuxp4Fatutvyy3kJjdJpGPr4A ovhAWOFClt2IEY5mxWnIiP68IIa3 ) ; KSK; alg = RSASHA512; key id = 37188 dyn.weberdns.de. 60 IN DNSKEY 257 3 10 ( AwEAAcD4vC7bqZKvApZIOXkuH++bXUBVf5XJj1oQvYn7 i3XjLmoCtOs7JyxElo4PeDnGIa4coAxBTHj4B+iVSa4n TJ5MK2lvEQVtwr8Pr+ZKOlYKmRs+SeRI1ZGN0OyBpQv/ TxPqZBN8V9RegsJ/adM9Rn5B96Be/hrMFzmkzd0iK2L9 I2TTAPl3YDfZ5vCQzdAMEZG9G56dfZK0GRgebCu3LHQv D7Wx+/P4CfUknOydZqmu0geww4VRUyveGUY+PLamJGie G6QopoTtuu5V+DJbjSA+mDPAfIW993iAw2TqMuD4tBha Q6HSmAA7FHydrq4fcqtuC+QxZaqAhQIEp93L6JM9xcl0 dY5m+OvqjCVBk/X7xRvpW1Xni3pEWs0wMcYfoeVegXXX w42123kEypd/78h0H7Y9AD5WVNnVnG2M/J0M1eVmsiyB 7xGvyLeFMBGPiuj0YN2bESnsR9A0tGUqgwHKtWcZwcLJ YqO/r6Ahp0wYqwcqJ2uwvolEjzGUrBOSY7fe4blauqnT sECWeHDpuOd3Hs+IupSYTIsyFnuI6oFNaSjiD5a2z7KN 25TjpNzYRbcbjnN1J4NabLvziGFwF+ZfSSI1TavipCg2 1MczJ8FJVZPeHIdIFMyt0d5JSL4a/iyHiaRtLw0N8GjC LDQvS57hJ0J/uQFFo0lPCIUy/iFH ) ; KSK; alg = RSASHA512; key id = 45918 dyn.weberdns.de. 60 IN RRSIG DNSKEY 10 3 60 ( 20180401194535 20180302184535 37188 dyn.weberdns.de. ebRRq3jKwDnFSPXoLB8dRodK2RjPvImRHeDnqLURJB3+ G6p5MDNB8GU0ktOOdONjzAo/A+7TKWJSQi3ty2mgyA1G oLxgXde+jAxejaDUD62dwMoLU/k8ylyOZ5VNYJ2keCCa qwgsonT8D+ehTybGR3FSzFgE8f7cklHA/RQQrwPjrDYQ rYaH4kPUP5Or9qGZyxu5yW09FZ3aqFFVIqpXKC0lh6ux M1DJ8TZwLh6pPU5S5uJm9VEIAstLqeQrlhEwKKi4sBeL NQnI2u+Ex6J+cMw3vzHV+tN/F+bqIpUxr/B9qEMuXWYV sYwtxZYZQzcHvOjboEbcKNqIN+CevFQie8kksm/Qfy// s2AmzLZpD2rnh39tg0KBQ3htiHVTYxKhRntEi/PIUTfy urY7sTkm1BR3lvtAAf9au3axWlzIUqGHIg9j1rRvcoxK fGAr6bFx61eU/rBoETfARpq1QTkfit+HZ4rz9vhKNjy8 PXwlRrIxPpvN9rGWx9SEiHF7fLZYUGH9/cednlkfVt91 Vi1Z0yDuAv/0BuR0uC+cXCBeF+AgdjP5JLnVN3MsJj9w sHngZUPJRw21q7MC10PHzUCbc9ViriLE0sWvkx/Fdum2 6/uXHkd4KU9rtKmxQzk0XLOdXLUN4Hmx/ZDH4oPpKqF7 JUgztAAgJbLPs5In93EBG2Q= ) dyn.weberdns.de. 60 IN RRSIG DNSKEY 10 3 60 ( 20180401194535 20180302184535 45918 dyn.weberdns.de. Qu2Cg7r0hzvIKQpBfVTHU1p4vf9XZPI+vmgd7iomdKef gGrpHOBUYNQnlworvwEwqUTgH+6cndcQJL0rnUGgGq0c 30PJf3TkPi/8szU/sj1efLvk7DEdihkSrQmqolqdq48k HIKLUeQYrTBvr/plhJg015jK3y6ln2tSkIcEd37qXveb tRG8v3cDjk+7SzbRw1+s8HceDS2klXosPZVI8CpYggCD wH5AtUZKFOLLAhDsxn5ZvPTTEmLvyT+hmky7REO/+4B6 ghELlOpya8E80jbrlpyxdEaW3Ohs3//32mtVyOUb7IS2 BRWcWMUV1DtEP99V8Ows67xd933bfIPBrElbIekH7Jen 2OaBoKKIct51b5ZRIHIVOf38Sg/mZvb2SUD1ynIuk/ee //EiB2hXuJ6ODwI3L09YCBtUSYha4dxiKz2RbCUE9UPA ozPu+nW0ToApYipUpEiX94njU9k4S5YEhD1CfWsSAw7J oPOsv0Nm2SRZW38Tqcve23fe6TQDQI3RReSRdlfBn6Id V1FaFQUEm94T1HyW+WylhWKO+sDk8QkMgUTPgAwcQFeA dIuV9LH/NoqA7K2j5JRUXf+PDF/DZP48Gu41YzxeE81Z 4iYStUQXRRXKkf6mj7cCDs5dJFs9ArLRLYsbEvJYKpAW 5E9hGrpa3RIaBgCZc+dZ1cU= ) dyn.weberdns.de. 60 IN RRSIG DNSKEY 10 3 60 ( 20180401194535 20180302184535 58340 dyn.weberdns.de. qCzOE7ntB7S7z7VqLpYtm9nzQnkCs688pA41kxInQD58 CDlKuuQgnFOpc9Z8Mt8ZM2XYdm/dOeKN7vwqcng62nH0 gKA9NyP83+1MKf6vdtbzkaaDD6APljYC7BtDN7InJRMN sMvE4B8deRGzdx2g3tcf0xhOLWVUwZ6vBW1VwL/g01VP QjCOA0jIm2DJld/O3AoLxEem5mFN81+3NxTqm7SQkthY UNp8tHQqGefNDxrDqIuvpjizcgUc/QAiCFDgw+DQqdhE az3fbyhK4IMJeraz97GvS7It9mMQtbkgApXIF6VKDGhT W9hnt0+2xI/ta5cka7504ZTIHwxu3IQdyi2x1P3uaiFL dzCFaI+3shDkLJSBx0BAFL37X8HqlagaUwk8LJp+UaWv WdC3ivedt/ekAPHyvXXU9f/+FF46IiFLxC6zMcdTqxs0 1qDV1KVR0DBVNYPNMu+GantY7Mzw30ZhxCa8HzGOuQdm VaaUKYHSTkkJQoJO61KE4Kd/jdSe39AGg18WgK95/E0w c8L9xLASNiN5CQ3xYu4X80/f4/0zmRD6E8FfXDwrjxDe RRyjBBlZpFUuEfNrA8XaYrHpuNQ1nhpLJrYO75a2wIa/ 0o/Y80cImm91p2M9UPOBrqdcVqx0tpzF9OnFXeTBn4j6 ajIp6c6NS9sGGDUKw7ANJzY= ) ;; Query time: 0 msec ;; SERVER: 2003:de:2016:110::a07:53#53(2003:de:2016:110::a07:53) ;; WHEN: Fri Mar 02 20:46:18 CET 2018 ;; MSG SIZE rcvd: 3317 weberjoh@nb15-lx:~$ |
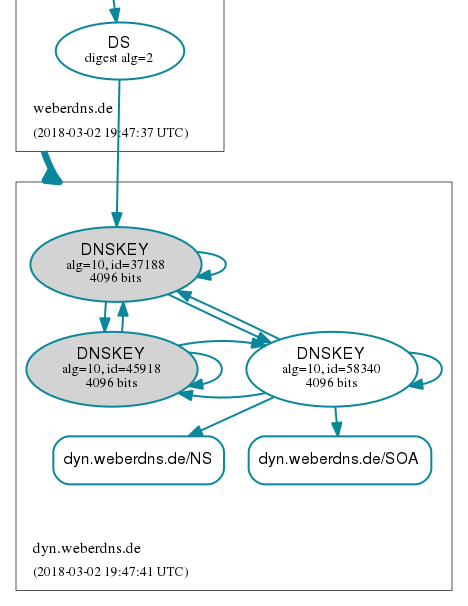
DNSViz shows the new KSK (45918), while the DS from the parent zone still points to the old KSK (37188):
19:48: Replaced (!) the DS at the parent zone and scheduled the delete date of the compromised KSK
At first I generated the new DS resource record:
|
1 2 |
weberjoh@vm16-ns0:/etc/bind/keys$ dnssec-dsfromkey -2 Kdyn.weberdns.de.+010+45918.key dyn.weberdns.de. IN DS 45918 10 2 29E4AE014492DEED9610422977D3AEC6CC8C42CBD08A4E5919E3FCCE75553B21 |
and replaced (!) it at the parent zone. Hence, querying the nameserver directly reveals only the new DS record:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
weberjoh@nb15-lx:~$ dig dyn.weberdns.de ds +multi +dnssec @ns1.weberdns.de ; <<>> DiG 9.10.3-P4-Ubuntu <<>> dyn.weberdns.de ds +multi +dnssec @ns1.weberdns.de ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 11770 ;; flags: qr aa rd; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;dyn.weberdns.de. IN DS ;; ANSWER SECTION: dyn.weberdns.de. 3600 IN DS 45918 10 2 ( 29E4AE014492DEED9610422977D3AEC6CC8C42CBD08A 4E5919E3FCCE75553B21 ) dyn.weberdns.de. 3600 IN RRSIG DS 8 3 3600 ( 20180401194940 20180302184940 37491 weberdns.de. UF5zdLI7JH7tsZ96jb8RXfVVz4TplBmm18KKJ0OGc5mr IB7+RcoKlJhNCTkb+U8gFG5fvpxzk+ixkZ6m6PIL9muh lKbKs/asWo+uTT3FS321HjwwOQOkJSJgiHJlZOqK02wL 2rsu1nDPgpuIkw5nfeGUua3J5ojtOqrODVYscmM= ) ;; Query time: 0 msec ;; SERVER: 2003:de:2016:110::a07:53#53(2003:de:2016:110::a07:53) ;; WHEN: Fri Mar 02 20:50:27 CET 2018 ;; MSG SIZE rcvd: 263 weberjoh@nb15-lx:~$ |
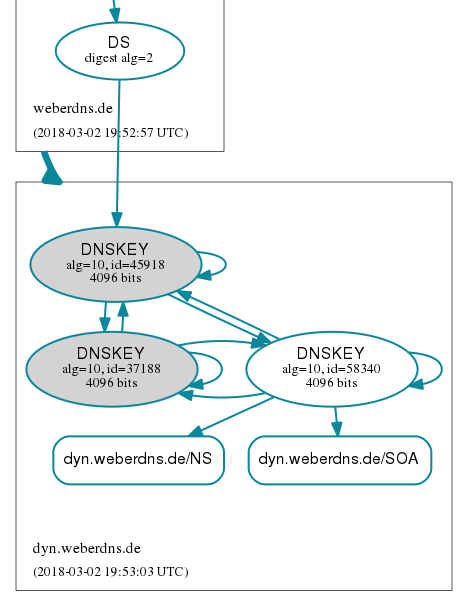
DNSViz shows this single DS record pointing to the new KSK (45918) while the old and compromised KSK (37188) is still present at the zone:
At this point all new/initial DNS queries will get the new chain of trust, while cached entries all around the world will still use the old (cached) DS record. This is why you MUST NOT delete the compromised KSK until this cached DS record times out!
Now I set the “delete” date of the compromised key to be in one hour, which is the TTL of the DS resource record.
|
1 2 3 |
weberjoh@vm16-ns0:/etc/bind/keys$ sudo dnssec-settime -D +1h Kdyn.weberdns.de.+010+37188 ./Kdyn.weberdns.de.+010+37188.key ./Kdyn.weberdns.de.+010+37188.private |
|
1 2 3 4 5 6 7 |
weberjoh@vm16-ns0:/etc/bind/keys$ cat Kdyn.weberdns.de.+010+37188.key ; This is a key-signing key, keyid 37188, for dyn.weberdns.de. ; Created: 20180301200135 (Thu Mar 1 21:01:35 2018) ; Publish: 20180301200135 (Thu Mar 1 21:01:35 2018) ; Activate: 20180301200135 (Thu Mar 1 21:01:35 2018) ; Delete: 20180302204947 (Fri Mar 2 21:49:47 2018) dyn.weberdns.de. IN DNSKEY 257 3 10 AwEAAeHRfPp41nJWSleIHZzNtM1il8wZQ4X5M/zLUb2ha3PoZoonfAQG Rg2DOYHApp46kJY0VvPQee7OWNjSuKcGtJHCcgbm33LUJFGkNKRhTMsC ufmLNt1xiwuKaukhQoLiZ8S2sYVgttpS4SSQW0gI8zaR13AaCD+VidIc 5GzpFN4YVniYjPDzk+e9zRai5ziEMMoWvj/BakgZ6oDwsHwkIDD3vW4y GnO+Dz8A4AnU8hdXei3wNI5CObUqEoVlx45aiziEu8/RAEh2lZOZZnAt wkbSyjNH5dsGuLzwAcrzN/7W9fIpQIF7h42c1UQT6MmkuRs87+oQBRkh MpWNokKs9NjeiA6sdVDqvKmxsT/smrFqDFPqlcyu+KtnVbRV7VcerWcT lFzHKw8RiTq6lnUWXqGTm9CKBvWwAZ/iMoE74kVFAo399jQIfId3sSV/ Nf2YgsQezswh+N92LFG0pl31ZWqJrisjCFrm2VA3KOWZ7i0eCpW2TbKJ gy/ROeztMVx/+LNnVjs0DaJXNrH0oxqQjOANLwuIkoV+2zBZcY22kID1 sWo7sLCZYR5ukkeHVosGvtm8Bo3Gaga4lYqr+BrUr41uIr8o1AwWTN5k TxJeilXRv3fx+Z/LdYlPuxp4Fatutvyy3kJjdJpGPr4AovhAWOFClt2I EY5mxWnIiP68IIa3 |
|
1 |
sudo rndc loadkeys dyn.weberdns.de |
20:50: BIND has deleted the compromised KSK
After this one hour of waiting, BIND successfully deleted the old (compromised) KSK out of the DNSKEY set. Hence, only one KSK and one ZSK, along with their two RRSIGs are present:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 |
weberjoh@nb15-lx:~$ dig dyn.weberdns.de dnskey +multi +dnssec ; <<>> DiG 9.10.3-P4-Ubuntu <<>> dyn.weberdns.de dnskey +multi +dnssec ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 20637 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;dyn.weberdns.de. IN DNSKEY ;; ANSWER SECTION: dyn.weberdns.de. 28 IN DNSKEY 256 3 10 ( AwEAAbiC3omZWzDtVx/nlwIEEgY1wrAQktqggJXNq50U +Xapj2+RQE4s7dNLU7AtJ+jvr/nplax61coz/2Na9YEc RE1LGpcZdrFH3iDZez+UcOY1GPll5xPGgpSPtSaL1j8M fUQgAw85ZmFQ6rUptYOpa3/w40n3MrgiOFyu8IoXhP7O QKICmHFAVcB6nurPZK6m52Vny/5R7CtHBmxGyU/Xcm6D oimWZPj56+QeQbthiPdSLNYNB8QoLWTPEuzjLdFaz7Jv Bp1n0tdqPS27OErcWV4eja6as1OyTODreo0b0pkM6Ulp 4xkY/7A/VbVFv9l/bHTIVFW/jXisk6Yr2/LwVy58/lGj oJ9SfpJnnelxYo0HMbp8zsQ2xGNzvH783NXsc0LeIATl WeBJrkW3hL4rJFc/5rT71RwHveukofFjXjk008Sgj1TD 6Gyx6I4XVi8AcbhTNajfh4K+elZMnJRnewQqk4g5KYBi ucyX0gR+JNSejqD4+mWuIyzKTh+cMrUsIBkXYQRzwlRf S8A0Zs9eVAQXVlKVgPEorj7fp1hnn6Ao8A2P7MeO5pdg ilFpSEIW3IbwtKqjPWY7wvVOo9Ms2TCdgePC34xxKGub gNQTBGU9MSlg16K2kvCavSYAgzQRUfzKtknPowr0ODz/ sBNRLH2swqvxU1rkkjZlS3RbW6+n ) ; ZSK; alg = RSASHA512; key id = 58340 dyn.weberdns.de. 28 IN DNSKEY 257 3 10 ( AwEAAcD4vC7bqZKvApZIOXkuH++bXUBVf5XJj1oQvYn7 i3XjLmoCtOs7JyxElo4PeDnGIa4coAxBTHj4B+iVSa4n TJ5MK2lvEQVtwr8Pr+ZKOlYKmRs+SeRI1ZGN0OyBpQv/ TxPqZBN8V9RegsJ/adM9Rn5B96Be/hrMFzmkzd0iK2L9 I2TTAPl3YDfZ5vCQzdAMEZG9G56dfZK0GRgebCu3LHQv D7Wx+/P4CfUknOydZqmu0geww4VRUyveGUY+PLamJGie G6QopoTtuu5V+DJbjSA+mDPAfIW993iAw2TqMuD4tBha Q6HSmAA7FHydrq4fcqtuC+QxZaqAhQIEp93L6JM9xcl0 dY5m+OvqjCVBk/X7xRvpW1Xni3pEWs0wMcYfoeVegXXX w42123kEypd/78h0H7Y9AD5WVNnVnG2M/J0M1eVmsiyB 7xGvyLeFMBGPiuj0YN2bESnsR9A0tGUqgwHKtWcZwcLJ YqO/r6Ahp0wYqwcqJ2uwvolEjzGUrBOSY7fe4blauqnT sECWeHDpuOd3Hs+IupSYTIsyFnuI6oFNaSjiD5a2z7KN 25TjpNzYRbcbjnN1J4NabLvziGFwF+ZfSSI1TavipCg2 1MczJ8FJVZPeHIdIFMyt0d5JSL4a/iyHiaRtLw0N8GjC LDQvS57hJ0J/uQFFo0lPCIUy/iFH ) ; KSK; alg = RSASHA512; key id = 45918 dyn.weberdns.de. 28 IN RRSIG DNSKEY 10 3 60 ( 20180401204947 20180302194947 45918 dyn.weberdns.de. XRjJhJV4/XpZpF6Il+x6hl3mextsfIbHcmCcubNtzELZ 1p+PUx5quS+TmzbUE0MbvHrgJw2EBkAOi5Y+h1ZmDkl5 hu0WaANaxpm4v8NPR7P4A7fVxMYwxgbZ4DO8BVFMb/4s R0sRYlzr3kAzEEbvIuzetM2kWMt9aNvpW0ZJ2NoubgPY eSnmy1EoZJC5ZGTvGcoiU5nJfl+jC+qWIo4TnTZ2gyiO my9qEFiXEDogKWHmbiloQR3u3OLiGUY5WBj8J6FDuBxu YYSXiEEgusLi2xwxK9tCZoeCSyBOV2mB3KvVwNrLDlgl yepC1c0iXtgdTjtxBJyUhNS7jnfl75aJ7cZezhGgaC3h +4CuiSvYsbdIVjDtDGHst0UrDYVvXOe3XWdbMrLY6ueV +cpxyT5cmXRusFskZjv4GgxwcaTTktDjaZX2umxWrNt+ 6CVcoL+wWTY6c3HaO1XZXnx7LQJyTu++G8/ICtVH1CAC AAxHJPsqCxQoBEdB5odehOPqw1nhaT5Syaz8q4O8NOIi e9ov0Xn6xtfiyXgjXfc++5SeynRm8MItEqccBzJbN3wp 3u0rDrBanSRxU5rF0T3nWW0bom7+p8KGUZuoremuimXS uM5kc72OXblvRkRqwWKjduKEmAY9fG6v7IH6sNJc7ugO Lz39HEeCmODSUsaQpiS5O/Y= ) dyn.weberdns.de. 28 IN RRSIG DNSKEY 10 3 60 ( 20180401204947 20180302194947 58340 dyn.weberdns.de. E4V4ymcuMUb+G5zVTozlgO0l1bRKc1Yw01+IQ671IjB/ j/3m8b8W9yCMr7jWY5NKOSRNP6mzMR30ILseiULVd88W +hayVNR6ya5jV7BOeVJOrVsiB8O0YrcYTFqBcCuwtZ59 xiiDXRYjWxm1ynxQF3RUgHuDmIeLnzZUh+Q1gVb4TRnZ ihZCbJMrdKtx8w8dLbtWNrYS5HeWFK6UvWRDiNNmJwI7 fKBOoF3mkaxlyf47o0l+oE082gt2v7x6z8LOsgCVyfd7 EuyCtZNGyjVriEowTqy10ZWe425Xzmu5/dIso/A9jpXd zplaWQlLmWTUZpdBiRphR3wpmPcdrpeMPZ90L6sPXuQv yzUzi7whrxpGc4BKVGmRl7Q+xqdxIdqKJ5/O0GBPzhiZ YKmOQ4vPnyFOysdJtP80pKVU8UQPvfqadnPiX+vI/wKU 2ktPpYkE8vE3AoZZiU4UatMg667bJjMhutuRSfmCEz1N AmzfKunLOtoMGnhm1fUz0UtcnijIrKUTUP2V1MvmOJVO uoWXMI683NiNVTNtoYfNa7kjVhI3lJH7o/XwhTm/Kyem AuZudFRXboQhZqwOJfYgj+2BuENUXs+Fc3qqhtJx01ZL Jh2cJ353ZWjkIHKk9P9FBE5oWfQl6039hmxB3yxcyM+u 65OxvWXXjdEDbmL2fN2Roi0= ) ;; Query time: 2 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Fri Mar 02 21:56:05 CET 2018 ;; MSG SIZE rcvd: 2226 weberjoh@nb15-lx:~$ |
And of course DNSViz greatly shows that the single DS record points to the single KSK:
Conclusion
Since I was able to immediately replace the old DS record at my parents zone with the new DS record, I could delete the compromised KSK just a few moments after the TTL of the old DS timed out, which was about 1 hour in my example. The chain of trust was completely intact during this one hour period.
It is a best practice to train a KSK rollover *before* you must do it in a case of emergency. Write down the commands you need and schedule a KSK rollover on a regular basis to be prepared.
Featured image “Zusammenstoß mit Rettungswagen Mainz 10.11.17” by Wiesbaden112.de is licensed under CC BY-NC-ND 2.0.





Your article helped me to master moving my domain to new provider and system, which inevitably included a new DNSSEC keys. Thank you so much. I have learned a lot.