Probably the most crucial part in a DNSSEC environment is the maintenance of the key-signing key, the KSK. You should rollover this key on a regular basis, though not that often as the zone signing keys, the ZSKs. I am doing a KSK rollover every 2 years.
In the following I will describe the two existing methods for a KSK rollover along with a step-by-step guide how I performed such a rollover for my zone “weberdns.de”. Of course again with many graphics from DNSViz (with “redundant edges”) that easily reveal the keys and signatures at a glance.
Generally keep in mind that as long as a single chain-of-trust is authentic, you won’t have any problems. Hence: Unless you’re deleting a DNSKEY or a DS record, you must not be afraid. You can add KSKs (DNSKEY 257) and DS records without the fear of loosing your secured zone. However, be carefully in talking to your registrars since at some point they must replace/delete the correct DS record pointing to your KSK. For official details about key rollovers in general, or especially for key signing key rollovers, refer to RFC 6781, section 4.1.2, Key Signing Key Rollovers.
Again: It’s all about Timing!
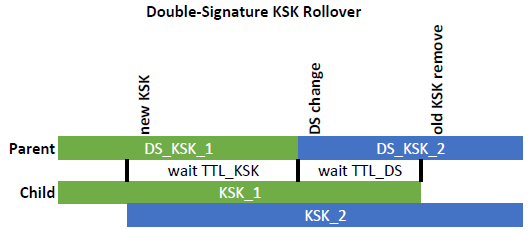
The RFC mentiones two approaches for the KSK rollover. The first one is called “Double-Signature KSK Rollover“. While the child domain has the new KSK along with the old KSK present in the zone in parallel (hence the name: double-signature since both KSKs sign the ZSK), the parent zone replaces the old DS with the new DS record at a time. The old KSK must not be deleted before the TTL of the old DS record times out:
The other approach is called “Double-DS KSK Rollover“. Here the parent zone has both DS records in parallel (hence the name) while the child replaces the old KSK with the new one at a time, just after the new DS record is propageted in the global DNS. The old DS record can be removed after the TTL of the old KSK times out:
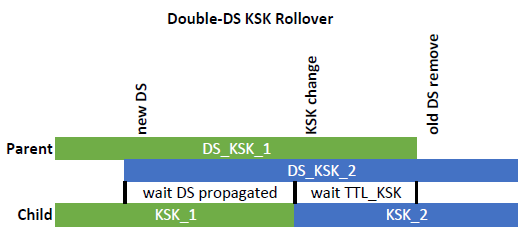
While the ZSK rollover, refer to this blogpost, relies on the four different dates a DNSKEY stores (publish, activate, inactive, delete), a KSK rollover only needs active and delete. That is: publish/activate can be at the same time, while inactive/delete can be at the same time as well.

For my KSK rollover I decided to use the first variant (double-signature) in which I have two KSKs in my zone while replacing the DS record at the parent zone. However, I did not fully follow “Figure 4” within this RFC section 4.1.2 since during a short period both DS records were present at my parents zone. That is: two DS records pointing to two KSKs. However, though not needed this was no problem for a valid chain-of-trust.
0) Initial
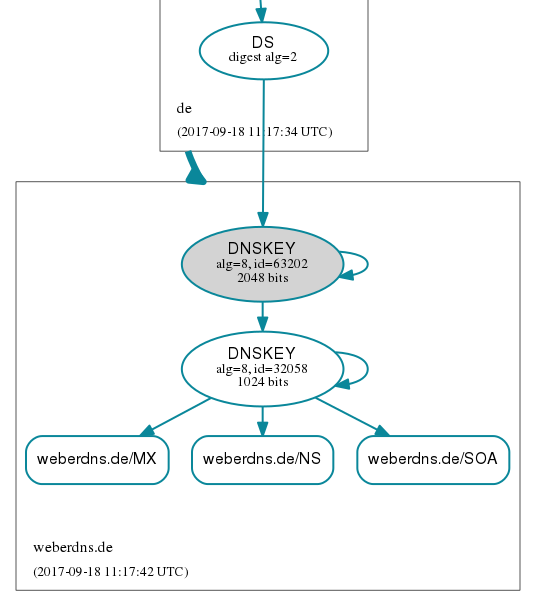
My initial situation: only one DS RR and one KSK (id: 63202). Querying the “dnskey” for my weberdns.de zone revealed exactly this single KSK (DNSKEY type 257) and a single ZSK (DNSKEY type 256) as well:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
weberjoh@jw-nb12-lxold:~$ dig weberdns.de dnskey +multi ; <<>> DiG 9.10.3-P4-Ubuntu <<>> weberdns.de dnskey +multi ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 43722 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;weberdns.de. IN DNSKEY ;; ANSWER SECTION: weberdns.de. 3260 IN DNSKEY 256 3 8 ( AwEAAdx+50fsj7Sxy2DvKiSIdo5YKl/REUJxgson+6O2 aXba9Kaj8Eowwmc/9gOacvCrQyzr3TY2b1wdP0Gg0VeH Yoa0A1LxWa9dy2Ts14yixcZ5KFYzubkz+doteFa3BFeJ oanQLLaDvB1Tx1GNz2XuuNvznZ4/ptQuqCQUPcvSYENn ) ; ZSK; alg = RSASHA256; key id = 32058 weberdns.de. 3260 IN DNSKEY 257 3 8 ( AwEAAdQXI+UfqnGbHdwJtBBStf0CM8Q8nXcriaOysrpG EDNkM//amUBD2YMWQ3g+htca6tmzfDJMM5D0gOk5d4Id EmdywkcH+0rGLjNiNEPFnZUpwb6XsYD+ZI/WEuSlp+KC EV8vwELq7VltABrFT+9Rz5CEvokTxonzQrvnfclVHaGw O7cglgALsFqJCqBpvDZvEr2Z6dSepjDnFC9BPS6V8PGS NwAYEtzDp/lrQojkCj28xHj2OCjpr0dIQjdjGFJTHIlc 9cYTAHjdPDsC8Eqfs5HcL3ruU6cbqjTn+5Lm4RdXpOWV gemVvIGDnUN+v+Tma/WgtQk7U3saizNJ3epCv3s= ) ; KSK; alg = RSASHA256; key id = 63202 ;; Query time: 1 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Mon Sep 18 13:26:12 CEST 2017 ;; MSG SIZE rcvd: 464 |
Same for the DS record (only a single one) at the parent zone:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
weberjoh@jw-nb12-lxold:~$ dig weberdns.de ds +multi ; <<>> DiG 9.10.3-P4-Ubuntu <<>> weberdns.de ds +multi ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 37644 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;weberdns.de. IN DS ;; ANSWER SECTION: weberdns.de. 81323 IN DS 63202 8 2 ( 2F9112FF344BCDF9C6F9A7548F04184AAE73458C7150 DE8FFFA3B7D9893C5EEE ) ;; Query time: 1 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Mon Sep 18 13:26:53 CEST 2017 ;; MSG SIZE rcvd: 88 |
DNSViz:
1) Generating a new KSK
I generated a new KSK as always, corrected the ownership to be readable by BIND, and did a reload:
|
1 2 3 4 |
cd /etc/bind/keys/ sudo dnssec-keygen -r /dev/urandom -a RSASHA256 -b 2048 -K /etc/bind/keys/ -f KSK -n ZONE weberdns.de sudo chown bind:bind * sudo rndc reload |
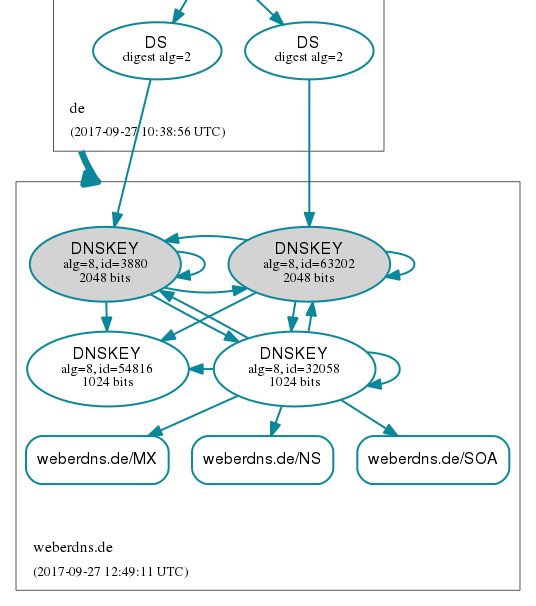
Immediately after that both KSKs were present in my zone. The new KSK had id 3880:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 |
weberjoh@jw-nb12-lxold:~$ dig weberdns.de dnskey @ns1.weberdns.de +multi ; <<>> DiG 9.10.3-P4-Ubuntu <<>> weberdns.de dnskey @ns1.weberdns.de +multi ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 47286 ;; flags: qr aa rd; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;weberdns.de. IN DNSKEY ;; ANSWER SECTION: weberdns.de. 3600 IN DNSKEY 257 3 8 ( AwEAAdQXI+UfqnGbHdwJtBBStf0CM8Q8nXcriaOysrpG EDNkM//amUBD2YMWQ3g+htca6tmzfDJMM5D0gOk5d4Id EmdywkcH+0rGLjNiNEPFnZUpwb6XsYD+ZI/WEuSlp+KC EV8vwELq7VltABrFT+9Rz5CEvokTxonzQrvnfclVHaGw O7cglgALsFqJCqBpvDZvEr2Z6dSepjDnFC9BPS6V8PGS NwAYEtzDp/lrQojkCj28xHj2OCjpr0dIQjdjGFJTHIlc 9cYTAHjdPDsC8Eqfs5HcL3ruU6cbqjTn+5Lm4RdXpOWV gemVvIGDnUN+v+Tma/WgtQk7U3saizNJ3epCv3s= ) ; KSK; alg = RSASHA256; key id = 63202 weberdns.de. 3600 IN DNSKEY 257 3 8 ( AwEAAbBpiuX423e8HACUAvARMzUH+stqMAFq0jmthfA7 FQc8d5sqMfZcK0vcg4QFIotAVIh8AfATggHP7tIy6rVu KqCnvF4LFan4ONNZ7c3WhLMiHB80F4M85NmRMMh/ssb3 2X10Th+iN3g2vPJtvP+rxoeRVT5XyNwbDB+AUCZgsElw wRmgB+UPQPLU1pZg9bOKW07ejdtayplItPqiuLQ5eRp8 OWeb92AtSpAORp8g4phc+ctvoH9a79lLCszTXiiJgaW3 8iLwD5rZHvqmKL6mSq/qEgxaQHkphinyfYJ7YzH+kbmO n7WXCgfbjSrVYhiCXeK+NKGgbUwJlwbHVfdYLVM= ) ; KSK; alg = RSASHA256; key id = 3880 weberdns.de. 3600 IN DNSKEY 256 3 8 ( AwEAAdx+50fsj7Sxy2DvKiSIdo5YKl/REUJxgson+6O2 aXba9Kaj8Eowwmc/9gOacvCrQyzr3TY2b1wdP0Gg0VeH Yoa0A1LxWa9dy2Ts14yixcZ5KFYzubkz+doteFa3BFeJ oanQLLaDvB1Tx1GNz2XuuNvznZ4/ptQuqCQUPcvSYENn ) ; ZSK; alg = RSASHA256; key id = 32058 ;; Query time: 0 msec ;; SERVER: 2003:de:2016:110::a07:53#53(2003:de:2016:110::a07:53) ;; WHEN: Mon Sep 18 13:39:08 CEST 2017 ;; MSG SIZE rcvd: 740 |
Note that at this time the three DNSKEY RRs are signed by all of the three keys (2x KSK, 1x ZSK) which might look a bit strange:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 |
weberjoh@jw-nb12-lxold:~$ dig weberdns.de dnskey @ns1.weberdns.de +multi +dnssec ; <<>> DiG 9.10.3-P4-Ubuntu <<>> weberdns.de dnskey @ns1.weberdns.de +multi +dnssec ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 52211 ;; flags: qr aa rd; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;weberdns.de. IN DNSKEY ;; ANSWER SECTION: weberdns.de. 3600 IN DNSKEY 257 3 8 ( AwEAAbBpiuX423e8HACUAvARMzUH+stqMAFq0jmthfA7 FQc8d5sqMfZcK0vcg4QFIotAVIh8AfATggHP7tIy6rVu KqCnvF4LFan4ONNZ7c3WhLMiHB80F4M85NmRMMh/ssb3 2X10Th+iN3g2vPJtvP+rxoeRVT5XyNwbDB+AUCZgsElw wRmgB+UPQPLU1pZg9bOKW07ejdtayplItPqiuLQ5eRp8 OWeb92AtSpAORp8g4phc+ctvoH9a79lLCszTXiiJgaW3 8iLwD5rZHvqmKL6mSq/qEgxaQHkphinyfYJ7YzH+kbmO n7WXCgfbjSrVYhiCXeK+NKGgbUwJlwbHVfdYLVM= ) ; KSK; alg = RSASHA256; key id = 3880 weberdns.de. 3600 IN DNSKEY 256 3 8 ( AwEAAdx+50fsj7Sxy2DvKiSIdo5YKl/REUJxgson+6O2 aXba9Kaj8Eowwmc/9gOacvCrQyzr3TY2b1wdP0Gg0VeH Yoa0A1LxWa9dy2Ts14yixcZ5KFYzubkz+doteFa3BFeJ oanQLLaDvB1Tx1GNz2XuuNvznZ4/ptQuqCQUPcvSYENn ) ; ZSK; alg = RSASHA256; key id = 32058 weberdns.de. 3600 IN DNSKEY 257 3 8 ( AwEAAdQXI+UfqnGbHdwJtBBStf0CM8Q8nXcriaOysrpG EDNkM//amUBD2YMWQ3g+htca6tmzfDJMM5D0gOk5d4Id EmdywkcH+0rGLjNiNEPFnZUpwb6XsYD+ZI/WEuSlp+KC EV8vwELq7VltABrFT+9Rz5CEvokTxonzQrvnfclVHaGw O7cglgALsFqJCqBpvDZvEr2Z6dSepjDnFC9BPS6V8PGS NwAYEtzDp/lrQojkCj28xHj2OCjpr0dIQjdjGFJTHIlc 9cYTAHjdPDsC8Eqfs5HcL3ruU6cbqjTn+5Lm4RdXpOWV gemVvIGDnUN+v+Tma/WgtQk7U3saizNJ3epCv3s= ) ; KSK; alg = RSASHA256; key id = 63202 weberdns.de. 3600 IN RRSIG DNSKEY 8 2 3600 ( 20171018113825 20170918103825 3880 weberdns.de. ML22wYIU9HMfKN/7/mC3bf0P/RmJ4DsMfj79OF2K3uw6 pqys3bIn7VUslkWK34uREAwOGnzOhZrZGMdPx2M/4XCS ANGaF0btMUFk4OSsv5CwXNh3dw92qV3qRb74IYvc16Pj 1VNt2uXCAs8tnzsDWK8XZ9CFJADDScU4je7ZNd1Q2Zkp BRwBNT5ZSH5tjemU4xVFNqh+i0VtA8Wah3MbRy7ulK50 a5LG9L1rOjQHPahwaEN/YeWBGl8IiDLfCy4KlBT783GH sevjyXd2XRVJeGTrJXOav2D5Zo90Q3qbAV4Gx59ykdBo 0yZ4o6zz4DRYxg9PnwVKBCpzpMT3fT/0Xw== ) weberdns.de. 3600 IN RRSIG DNSKEY 8 2 3600 ( 20171018113825 20170918103825 32058 weberdns.de. QEAJzdl1uLG4tE+NSIRFqrhnIsJxCi0CPUOLZeEzz1m3 YEHc4r5T1SHERyxh2uBbJRAnAS0mBoUwx9WI+Bosdgw6 iODTn7IRNXpVl5sOK8Z9NaH0rRrfmr0LgBQLvEUV7Ws0 IWNeMOThwdEIklT1jyZO0KWprDhNSlPHqXTJQsI= ) weberdns.de. 3600 IN RRSIG DNSKEY 8 2 3600 ( 20171018113825 20170918103825 63202 weberdns.de. UUJh+x+iNogEHHVl7j9Z9SCD24je1iRvmhXBb7khjA67 N+mTtCRP7wqsIxOevYbeBTNtaKzeHVttlyrQ89fPCFNX +tAfgyfeWp0UYzv+w4pKBkTeOR3Il6jigo3SgLwbyBOg iH5QbfWI3IbfRnctUFt/VnjQXl1fedh2aGddu32o1kdI /NXRVBlNVcSltMUH7WTEspLCo4TwBuZvhrA73F2iztWs RNWuM0kimHLEkEujeq0UTMeQ8WeJ6SYLUfiiQxw/8e0d iKoE6mbshczmY0SrDG6tSHC95zh9scQswRTMBQ72I2R/ ANzz7mhwfnHxoELWLyW3bodWGFoYjb3WJg== ) ;; Query time: 0 msec ;; SERVER: 2003:de:2016:110::a07:53#53(2003:de:2016:110::a07:53) ;; WHEN: Mon Sep 18 13:57:52 CEST 2017 ;; MSG SIZE rcvd: 1509 |
DNSViz (with many redundant edges at this time):
2) New DS in Parent Zone
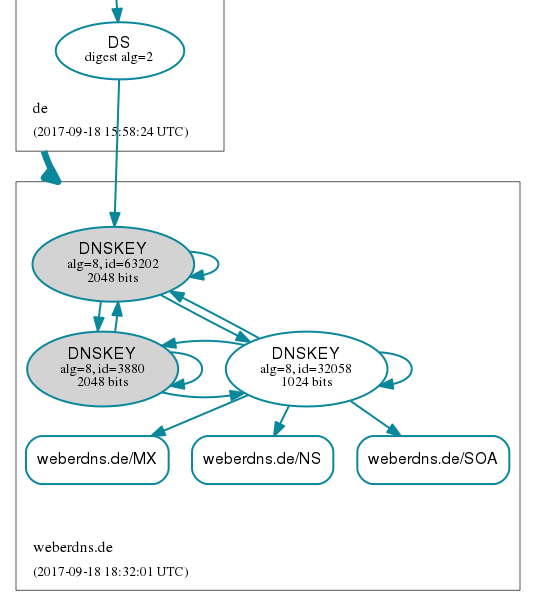
Now I sent my new DS record to my parent zone which did not replace the old DS but added it. Hence there were two DS records in the zone. Note that this step is NOT NEEDED and I just wanted to test it. You MUST NOT have both KSKs and both DS RR active while using one of the KSK rollover schemes.
A whois weberdns.de looked like that:
|
1 2 3 4 5 6 7 8 9 10 11 |
weberjoh@nb15-lx:~$ whois weberdns.de [...] Domain: weberdns.de Nserver: ns1.weberdns.de 2003:de:2016:110:0:0:a07:53 87.190.30.114 Nserver: ns2.weberdns.de 213.61.29.182 Nserver: ns3.weberdns.de 193.24.225.53 Dnskey: 257 3 8 AwEAAbBpiuX423e8HACUAvARMzUH+stqMAFq0jmthfA7FQc8d5sqMfZcK0vcg4QFIotAVIh8AfATggHP7tIy6rVuKqCnvF4LFan4ONNZ7c3WhLMiHB80F4M85NmRMMh/ssb32X10Th+iN3g2vPJtvP+rxoeRVT5XyNwbDB+AUCZgsElwwRmgB+UPQPLU1pZg9bOKW07ejdtayplItPqiuLQ5eRp8OWeb92AtSpAORp8g4phc+ctvoH9a79lLCszTXiiJgaW38iLwD5rZHvqmKL6mSq/qEgxaQHkphinyfYJ7YzH+kbmOn7WXCgfbjSrVYhiCXeK+NKGgbUwJlwbHVfdYLVM= Dnskey: 257 3 8 AwEAAdQXI+UfqnGbHdwJtBBStf0CM8Q8nXcriaOysrpGEDNkM//amUBD2YMWQ3g+htca6tmzfDJMM5D0gOk5d4IdEmdywkcH+0rGLjNiNEPFnZUpwb6XsYD+ZI/WEuSlp+KCEV8vwELq7VltABrFT+9Rz5CEvokTxonzQrvnfclVHaGwO7cglgALsFqJCqBpvDZvEr2Z6dSepjDnFC9BPS6V8PGSNwAYEtzDp/lrQojkCj28xHj2OCjpr0dIQjdjGFJTHIlc9cYTAHjdPDsC8Eqfs5HcL3ruU6cbqjTn+5Lm4RdXpOWVgemVvIGDnUN+v+Tma/WgtQk7U3saizNJ3epCv3s= Status: connect Changed: 2017-09-27T14:28:14+02:00 [...] |
And a query of the DS record(s) like that:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
weberjoh@nb15-lx:~$ dig weberdns.de ds +multi ; <<>> DiG 9.10.3-P4-Ubuntu <<>> weberdns.de ds +multi ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 6098 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;weberdns.de. IN DS ;; ANSWER SECTION: weberdns.de. 75274 IN DS 3880 8 2 ( E262B8D6CB3E818B114D03393E758DD60C663DF09A97 422D7C4E2436860741B5 ) weberdns.de. 75274 IN DS 63202 8 2 ( 2F9112FF344BCDF9C6F9A7548F04184AAE73458C7150 DE8FFFA3B7D9893C5EEE ) ;; Query time: 1 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Tue Oct 24 14:41:46 CEST 2017 ;; MSG SIZE rcvd: 136 |
DNSViz:
Haha, and just to mix up more keys: Since my scheduled ZSK (not KSK) rollover took place in the meantime, I had two ZSKs in the zone as well (ids: 32058, 54816), which gave 4x DNSKEYs along with 3x RRSIGs. You can see this in the DNSViz graph above as well. ;)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 |
weberjoh@nb15-lx:~$ dig weberdns.de dnskey +dnssec +multi ; <<>> DiG 9.10.3-P4-Ubuntu <<>> weberdns.de dnskey +dnssec +multi ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 24477 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 7, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;weberdns.de. IN DNSKEY ;; ANSWER SECTION: weberdns.de. 2992 IN DNSKEY 256 3 8 ( AwEAAdx+50fsj7Sxy2DvKiSIdo5YKl/REUJxgson+6O2 aXba9Kaj8Eowwmc/9gOacvCrQyzr3TY2b1wdP0Gg0VeH Yoa0A1LxWa9dy2Ts14yixcZ5KFYzubkz+doteFa3BFeJ oanQLLaDvB1Tx1GNz2XuuNvznZ4/ptQuqCQUPcvSYENn ) ; ZSK; alg = RSASHA256; key id = 32058 weberdns.de. 2992 IN DNSKEY 257 3 8 ( AwEAAdQXI+UfqnGbHdwJtBBStf0CM8Q8nXcriaOysrpG EDNkM//amUBD2YMWQ3g+htca6tmzfDJMM5D0gOk5d4Id EmdywkcH+0rGLjNiNEPFnZUpwb6XsYD+ZI/WEuSlp+KC EV8vwELq7VltABrFT+9Rz5CEvokTxonzQrvnfclVHaGw O7cglgALsFqJCqBpvDZvEr2Z6dSepjDnFC9BPS6V8PGS NwAYEtzDp/lrQojkCj28xHj2OCjpr0dIQjdjGFJTHIlc 9cYTAHjdPDsC8Eqfs5HcL3ruU6cbqjTn+5Lm4RdXpOWV gemVvIGDnUN+v+Tma/WgtQk7U3saizNJ3epCv3s= ) ; KSK; alg = RSASHA256; key id = 63202 weberdns.de. 2992 IN DNSKEY 257 3 8 ( AwEAAbBpiuX423e8HACUAvARMzUH+stqMAFq0jmthfA7 FQc8d5sqMfZcK0vcg4QFIotAVIh8AfATggHP7tIy6rVu KqCnvF4LFan4ONNZ7c3WhLMiHB80F4M85NmRMMh/ssb3 2X10Th+iN3g2vPJtvP+rxoeRVT5XyNwbDB+AUCZgsElw wRmgB+UPQPLU1pZg9bOKW07ejdtayplItPqiuLQ5eRp8 OWeb92AtSpAORp8g4phc+ctvoH9a79lLCszTXiiJgaW3 8iLwD5rZHvqmKL6mSq/qEgxaQHkphinyfYJ7YzH+kbmO n7WXCgfbjSrVYhiCXeK+NKGgbUwJlwbHVfdYLVM= ) ; KSK; alg = RSASHA256; key id = 3880 weberdns.de. 2992 IN DNSKEY 256 3 8 ( AwEAAdnRt6U7iD6mT8AOyKLX8nhKZSbE5lfQxkfrqcn6 XPGa96g1ywquKCU/XiMyGcjIx+98EcH2jiHHpAKnGkM4 ggP/iGW8q9CCskQAaKshrwCkp2wa6IpahSpgxgOrs6bM K5ZXJ+HKb2Xp5V98pJtSE+itUXUDXrauIVAPYY4i0935 ) ; ZSK; alg = RSASHA256; key id = 54816 weberdns.de. 2992 IN RRSIG DNSKEY 8 2 3600 ( 20171118011635 20171019010503 3880 weberdns.de. ndm9Q9p+t++Fd2QZUhNYrGTxpMuBYA8i3ObrkDtsuGjE zPtVO+Rs3ltkp56tpRHbJHwaUfoPz0iVM0KFk1t6M94I H8PiTUxNJ9hMbQidKQ5uapR1AShPBTUcu8Lw54ecpYyU l7pC7AggH3kvTVZ7kQvgmYehuXAfNFZGUzJuaBFimWt5 W/HbfkT+d1r2WDdim/BV/tugPonmcvdQaU7tGv6Wb6HI gXV9Q1eHMzduGvfjIQU00hvsoPvsr4BIeZwZurDmJ46/ O5xOPHHCntWR71djBI/k+ROPjTU8Rw+DIngGW/NKwhCQ E+xlsVAdDAT/O1fdz4Dt7Vv7SosP3aMn0A== ) weberdns.de. 2992 IN RRSIG DNSKEY 8 2 3600 ( 20171118011635 20171019010503 32058 weberdns.de. OaLfVLoOxWDwve5HN9M4oqrxCk+X61PXlVnvVFo9cb1Y PDLpr2aOQf+lXl/2DcShPHpsOEMtIgShXufZTvdnTMWp 0kqqxDNLf2HLa5PGnJUnxj7ofBsEoInH2nr+Y2xEdybK fTdtzI/V0U9od78+N7xUOr0reqK+MW+YzEId0Y0= ) weberdns.de. 2992 IN RRSIG DNSKEY 8 2 3600 ( 20171118011635 20171019010503 63202 weberdns.de. hku8McB9L7ZJMt/j8K9Y7A/vXXcz9S9ppDh5hdgjai8l iZ+Pg6Lcc5icc1ifvGzGY1jQPV92c52qJK6kusk/a2uP W9CUfKICFWGwkaLBh+CeQUgoLffe4PUPJK8zm2q6JBax w7FNI1HFI9J4Aws+j86PPoxNv3u7R/KVQ68hH2QhZyJ4 Kc2Evpd49GrPlk0ntxsrirEFExUQCOAi29/0L+yIFs31 aMDy/E9E50EhKnlqA6OGD9IwCkLT5r9tPTaClVz4u230 7oyq+rz/uUnHlIhYW5ZF5NFNY4IRVKDn0nMTXWK0iyZ+ /7E82bfYwSWhxhr1dYB+KMMKkJtu3qpQqQ== ) ;; Query time: 2 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Tue Oct 24 14:48:13 CEST 2017 ;; MSG SIZE rcvd: 1657 |
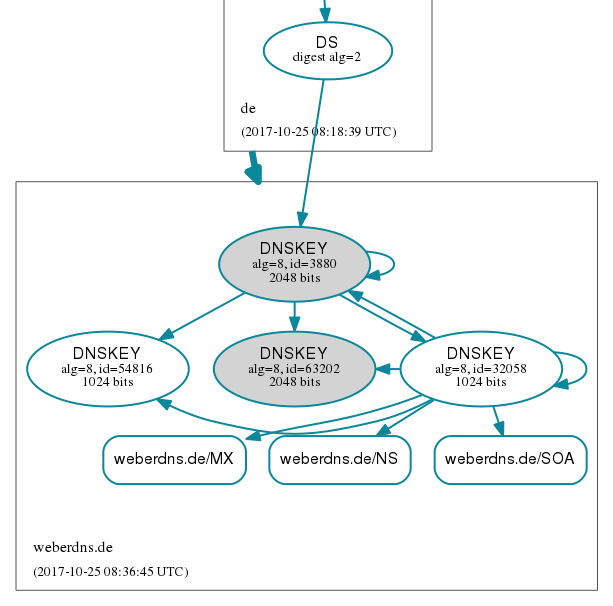
After some time I told my parent zone to remove the old DS record which is the actual “DS change” event. That is: The new and only DS record pointed to the new KSK, while the old KSK was still present in the zone. DNSViz:
3) Deleting the old KSK
Just for fun I did not only set the delete date but scheduled it after one day of inactivity. Note again that this is NOT NEEDED. You can simply set both dates at one time.
|
1 2 3 4 5 6 7 8 9 10 |
sudo dnssec-settime -I +5mi -D +1d Kweberdns.de.+008+63202 weberjoh@vm16-ns0:/etc/bind/keys$ cat Kweberdns.de.+008+63202.key ; This is a key-signing key, keyid 63202, for weberdns.de. ; Created: 20160205194002 (Fri Feb 5 20:40:02 2016) ; Publish: 20160205194002 (Fri Feb 5 20:40:02 2016) ; Activate: 20160205194002 (Fri Feb 5 20:40:02 2016) ; Inactive: 20171025071345 (Wed Oct 25 09:13:45 2017) ; Delete: 20171026070845 (Thu Oct 26 09:08:45 2017) weberdns.de. IN DNSKEY 257 3 8 AwEAAdQXI+UfqnGbHdwJtBBStf0CM8Q8nXcriaOysrpGEDNkM//amUBD 2YMWQ3g+htca6tmzfDJMM5D0gOk5d4IdEmdywkcH+0rGLjNiNEPFnZUp wb6XsYD+ZI/WEuSlp+KCEV8vwELq7VltABrFT+9Rz5CEvokTxonzQrvn fclVHaGwO7cglgALsFqJCqBpvDZvEr2Z6dSepjDnFC9BPS6V8PGSNwAY EtzDp/lrQojkCj28xHj2OCjpr0dIQjdjGFJTHIlc9cYTAHjdPDsC8Eqf s5HcL3ruU6cbqjTn+5Lm4RdXpOWVgemVvIGDnUN+v+Tma/WgtQk7U3sa izNJ3epCv3s= |
Followed by a sudo rndc loadkeys weberdns.de.
During this one day of “inactive” I had both KSKs in my zone, while only the new KSK (along with the ZSK) signed the RRSIG:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 |
weberjoh@nb15-lx:~$ dig weberdns.de dnskey +dnssec +multi @ns1.weberdns.de ; <<>> DiG 9.10.3-P4-Ubuntu <<>> weberdns.de dnskey +dnssec +multi @ns1.weberdns.de ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 59640 ;; flags: qr aa rd; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;weberdns.de. IN DNSKEY ;; ANSWER SECTION: weberdns.de. 3600 IN DNSKEY 256 3 8 ( AwEAAdx+50fsj7Sxy2DvKiSIdo5YKl/REUJxgson+6O2 aXba9Kaj8Eowwmc/9gOacvCrQyzr3TY2b1wdP0Gg0VeH Yoa0A1LxWa9dy2Ts14yixcZ5KFYzubkz+doteFa3BFeJ oanQLLaDvB1Tx1GNz2XuuNvznZ4/ptQuqCQUPcvSYENn ) ; ZSK; alg = RSASHA256; key id = 32058 weberdns.de. 3600 IN DNSKEY 257 3 8 ( AwEAAdQXI+UfqnGbHdwJtBBStf0CM8Q8nXcriaOysrpG EDNkM//amUBD2YMWQ3g+htca6tmzfDJMM5D0gOk5d4Id EmdywkcH+0rGLjNiNEPFnZUpwb6XsYD+ZI/WEuSlp+KC EV8vwELq7VltABrFT+9Rz5CEvokTxonzQrvnfclVHaGw O7cglgALsFqJCqBpvDZvEr2Z6dSepjDnFC9BPS6V8PGS NwAYEtzDp/lrQojkCj28xHj2OCjpr0dIQjdjGFJTHIlc 9cYTAHjdPDsC8Eqfs5HcL3ruU6cbqjTn+5Lm4RdXpOWV gemVvIGDnUN+v+Tma/WgtQk7U3saizNJ3epCv3s= ) ; KSK; alg = RSASHA256; key id = 63202 weberdns.de. 3600 IN DNSKEY 257 3 8 ( AwEAAbBpiuX423e8HACUAvARMzUH+stqMAFq0jmthfA7 FQc8d5sqMfZcK0vcg4QFIotAVIh8AfATggHP7tIy6rVu KqCnvF4LFan4ONNZ7c3WhLMiHB80F4M85NmRMMh/ssb3 2X10Th+iN3g2vPJtvP+rxoeRVT5XyNwbDB+AUCZgsElw wRmgB+UPQPLU1pZg9bOKW07ejdtayplItPqiuLQ5eRp8 OWeb92AtSpAORp8g4phc+ctvoH9a79lLCszTXiiJgaW3 8iLwD5rZHvqmKL6mSq/qEgxaQHkphinyfYJ7YzH+kbmO n7WXCgfbjSrVYhiCXeK+NKGgbUwJlwbHVfdYLVM= ) ; KSK; alg = RSASHA256; key id = 3880 weberdns.de. 3600 IN DNSKEY 256 3 8 ( AwEAAdnRt6U7iD6mT8AOyKLX8nhKZSbE5lfQxkfrqcn6 XPGa96g1ywquKCU/XiMyGcjIx+98EcH2jiHHpAKnGkM4 ggP/iGW8q9CCskQAaKshrwCkp2wa6IpahSpgxgOrs6bM K5ZXJ+HKb2Xp5V98pJtSE+itUXUDXrauIVAPYY4i0935 ) ; ZSK; alg = RSASHA256; key id = 54816 weberdns.de. 3600 IN RRSIG DNSKEY 8 2 3600 ( 20171124083525 20171025073525 3880 weberdns.de. g9Y9d3b4/4cjFW1hDNbq0aNCgS7Q4BDaiN7fwzc6WlUU 9QyQvmaAFoNEwC/EtKfZihAK5ZBY+GLyFj5rv7EIc53Q D9AM9vOpnvF4YkWV1A6/cZKf80j/Wng/fNma0+eFjx42 kMxY2cTy+MjyhBBOQmlg5vw7Uu45bpCqUjgdwjpSH5A6 Eeqw8i52EpS0SsxaIPYY43tf3dGYM/hHTgLSFiPGX8Dc ozqbQ3Nc/08tBHuDf2t3Lne9/SedHYzZx4zfxUTopO2q 5lV1aC9AEFJ3Ir2HPhA20p40eGbZ0OcHh5gVmCxWTu8a GTZE/d+qkzKKdc9O4LYbDi0yFGg/Oe22EA== ) weberdns.de. 3600 IN RRSIG DNSKEY 8 2 3600 ( 20171124083525 20171025073525 32058 weberdns.de. FnraKYsqfe6r4QbpqvO3bAwoiz4SJvu4/sWK2xDlibyi shfbft6fISgWa2ciE8/uio57DY0MyY65d2R035tOqaDb OwWygHPyt6UNzxSYa+UWaHfrrJdi95OH8OYHjUtdIUc/ uiMkePYWvdcZDHahAOaQUgPSAuf5gK1vl1MEyZQ= ) ;; Query time: 0 msec ;; SERVER: 2003:de:2016:110::a07:53#53(2003:de:2016:110::a07:53) ;; WHEN: Wed Oct 25 10:40:34 CEST 2017 ;; MSG SIZE rcvd: 1358 |
DNSViz:
And, as expected, after the “delete” date the old KSK was completely gone. That is: During several steps in the last days/weeks the chain of trust was always valid, while at the end a single and new DS record pointed to the single and new KSK at my zone. So for the last time today, the DNSViz graph:
Featured image “Roll” by Quinn Dombrowski is licensed under CC BY-SA 2.0.





Are there interactions with ZSK and KSK rollover that one should be aware of? For example, if one were to decide to roll each once a year, could it be done at the same time?
Hi Earl.
I am not aware of any specific problems if rolling over both keys at the same time. However, I would not recommend it though. Just a feeling. Keep it simple. (Since DNSSEC with its keys is already complicated enough.)
If you want to roll over both keys once a year at the same time (that is: if you do NOT rollover your ZSK more often), you can use a single (!) key for both. That is: your parent zone points to this single key which directly signs the zone rather than the ZSK. Google for it. There are some tutorials out there.
Otherwise I am recommending to rollover the ZSK more often (e.g., 3-4x a year) and the KSK less often (e.g., every 2-3 years).
Cheers.
I’m puzzled.
Can’t you let rfc5011 take care of updating the keys at your registry?
Hey MP.
No, RFC 5011 is about *resolvers* that must update their trust anchors for each DNS tree (“islands of signed name spaces”). This would be the case if you have different islands of DNS trusts on your network. For the Intenet we currently have only one trust point, the root “.”. And yes, there was a KSK rollover on the Internet happening during 2017/2018 but I am not quite sure whether this RFC was helping the resolvers to do this.
However, my blogpost here is about a KSK rollover of your *own zone* on an authoritative name server. In this case you must submit the new KSK/DS to your parent zone. I am not aware of any widely deployed mechanism that simplifies this quite manual process.
Cheers, Johannes
Hi,
In your double-signature drawing: https://weberblog.net/wp-content/uploads/2018/02/Grafik-Timeline-KSK-Key-Rollover-Double-Signature.png
You are stating that there is no wait needed, between the introduction of the new KSK and double signature and swapping the old DS for the new DS in the parent.
I think this is wrong as you do have to wait TTL KSK + propagation time before you may swap the DS in the parent. This to ensure all resolvers have the double signature in cache.
If you swap the DS in the parent too early, then it could happen that there are still resolvers only knowing about the old KSK RRSIG in cache, while having fetched the new DS RRSET and so breaking their chain of trust.
Hey SvenVD,
thanks for your comment. To be honest I am not 100 % sure at the moment. I am referring to https://tools.ietf.org/html/rfc6781#section-4.1.2 that states the following:
new DNSKEY: During the “new DNSKEY” phase, the zone administrator
generates a second KSK, DNSKEY_K_2. The key is provided to the
parent, and the child will have to wait until a new DS RR has been
generated that points to DNSKEY_K_2. After that DS RR has been
published on all servers authoritative for the parent’s zone, the
zone administrator has to wait at least TTL_DS to make sure that
the old DS RR has expired from caches.
My understanding is, that the only wait is *after* the new DS RR has been generated/published.
Your scenario, however, sounds valid. Ugh. It’s not that easy to test it explicitly. (I have tried to test some other wierd scenarios, but did not succeed as well: https://weberblog.net/signed-dns-zone-with-too-long-living-ttls/) At least I was able to test an emergency KSK rollover which did not make any problems: https://weberblog.net/dnssec-ksk-emergency-rollover/
Anyway, I would completely agree that you SHOULD wait for any TTLs to expire before doing the next step. This ensure that you’re not running into these kind of problems.
Cu,
Johannes
Hey SvenVD again,
I had a little discussion on Twitter (https://twitter.com/webernetz/status/1053677060324052992) and it turned out, that your concern is valid! You MUST wait TTL_KSK before you’re changing the DS record at the parent zone!
There is an errata to RFC 6781 that corrects exactly my quoted sentence: https://www.rfc-editor.org/errata/eid4844
And for an even more detailed timing overview you can have a look at RFC 7583: https://tools.ietf.org/html/rfc7583#section-3.3.1
I’ll update my graphic immediately. Thanks for your note!
Johannes
Hi, nice this has been cleared up.
Haha, it took me almost 8 month to update this single drawing. :D But now it’s corrected. Finally.