This blog post shows how to configure a site-to-site IPsec VPN between a FortiGate firewall and a Cisco router. The FortiGate is configured via the GUI – the router via the CLI. I am showing the screenshots/listings as well as a few troubleshooting commands.
The VPN tunnel shown here is a route-based tunnel. That is, I do NOT use proxy-ids in phase 2 for the routing decision (which would be policy-based), but tunnel-interfaces and static routes. This applies to both devices.
The FortiGate firewall in my lab is a FortiWiFi 90D (v5.2.2), the Cisco router an 2811 with software version 12.4(24)T8.
Lab
The following figure shows the lab for this VPN:
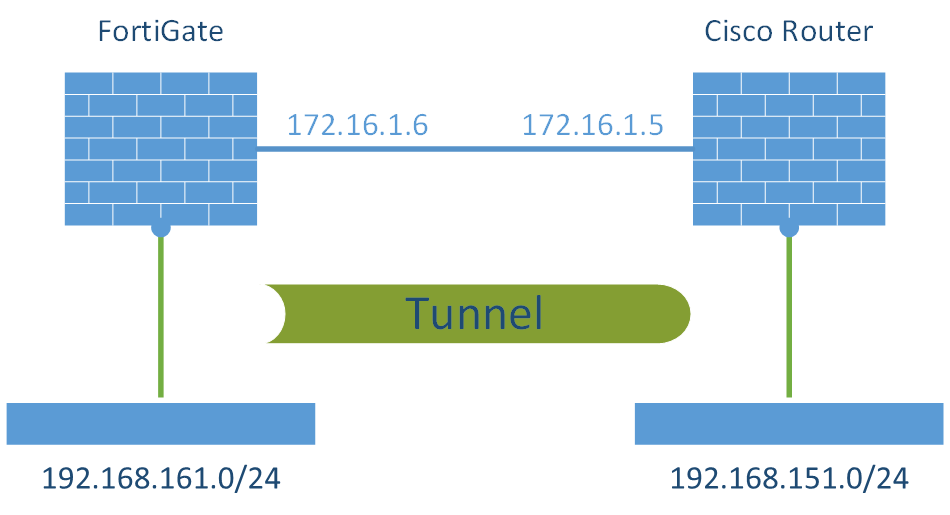
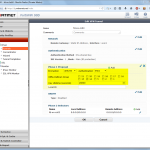
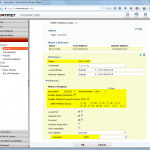
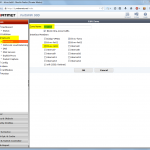
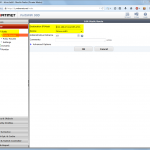
FortiGate
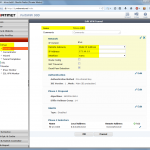
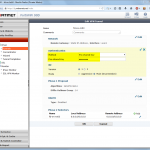
These are the steps for the FortiGate firewall. Refer to the descriptions under the screenshots for further details:
Cisco Router
The Cisco router ist configured with the following commands:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
crypto isakmp policy 10 encr aes 256 authentication pre-share group 14 lifetime 28800 crypto isakmp key ZByLKnMxmohpNLBPAgwckJhY address 172.16.1.6 crypto isakmp keepalive 10 5 ! crypto ipsec transform-set aes256-sha esp-aes 256 esp-sha-hmac ! crypto ipsec profile FG set transform-set aes256-sha set pfs group14 ! interface Tunnel161 ip unnumbered FastEthernet0/1.151 tunnel source 172.16.1.5 tunnel destination 172.16.1.6 tunnel mode ipsec ipv4 tunnel protection ipsec profile FG ! ip route 192.168.161.0 255.255.255.0 Tunnel161 |
Monitoring
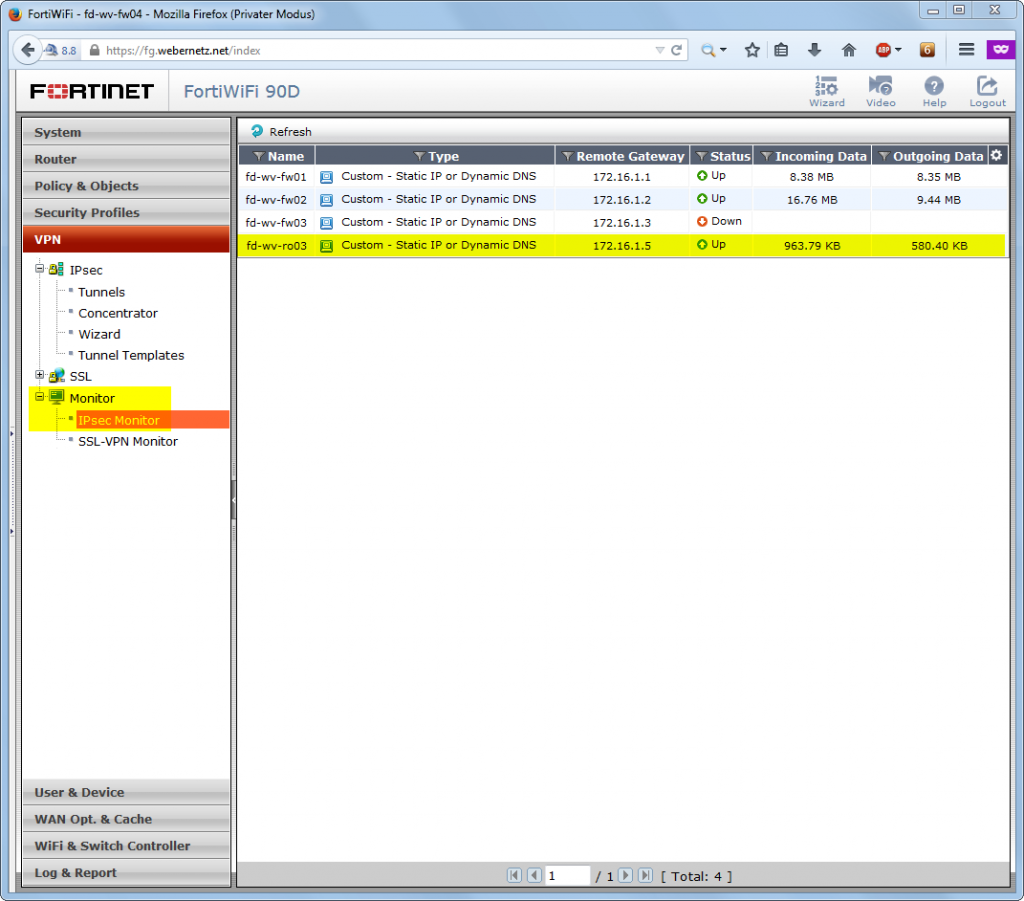
The FortiGate has an IPsec Monitor status of “Up”,
and can be queried via the CLI, too:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 |
fd-wv-fw04 # get vpn ike gateway fd-wv-ro03 vd: root/0 name: fd-wv-ro03 version: 1 interface: wan1 6 addr: 172.16.1.6:500 -> 172.16.1.5:500 created: 1789239s ago IKE SA created: 1/63 established: 1/63 time: 380/461/2480 ms IPsec SA created: 1/514 established: 1/514 time: 360/382/590 ms id/spi: 20213 7369fa8ea50b4193/15f1b4d8a7818977 direction: initiator status: established 22210-22210s ago = 380ms proposal: aes-256-sha1 key: 2a0a6784e29fbe70-ade0d6d6a368bdca-5e81890d77f7ca7a-db7e9f75c746aa94 lifetime/rekey: 28800/6289 DPD sent/recv: 000d1c3e/4f447f71 fd-wv-fw04 # fd-wv-fw04 # fd-wv-fw04 # get vpn ipsec tunnel name fd-wv-ro03 gateway name: 'fd-wv-ro03' type: route-based local-gateway: 172.16.1.6:0 (static) remote-gateway: 172.16.1.5:0 (static) mode: ike-v1 interface: 'wan1' (6) rx packets: 1584 bytes: 199840 errors: 0 tx packets: 1595 bytes: 135078 errors: 0 dpd: enabled/negotiated idle: 5000ms retry: 3 count: 0 selectors name: 'fd-wv-ro03' auto-negotiate: disable mode: tunnel src: 0:0.0.0.0/0.0.0.0:0 dst: 0:0.0.0.0/0.0.0.0:0 SA lifetime/rekey: 3600/923 mtu: 1438 tx-esp-seq: 600 replay: enabled inbound spi: c97b0d54 enc: aes 43821ea396d91c75a865fa39ceb11dbae01761965f5c259c8ff08288034a2951 auth: sha1 e3b74f75ee315f3a6bb6c08f820fd7326e6efa1e outbound spi: 5ffae69c enc: aes 8b4721951aa7878a50c865f1853fd55944dfc514e7f12fee8288d458f3aa8b64 auth: sha1 f8905c11627d73bd643bda374f8a6214dbc12281 NPU acceleration: encryption(outbound) decryption(inbound) |
The Cisco router show commands are the following:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 |
fd-wv-ro03#show crypto isakmp sa detail Codes: C - IKE configuration mode, D - Dead Peer Detection K - Keepalives, N - NAT-traversal T - cTCP encapsulation, X - IKE Extended Authentication psk - Preshared key, rsig - RSA signature renc - RSA encryption IPv4 Crypto ISAKMP SA C-id Local Remote I-VRF Status Encr Hash Auth DH Lifetime Cap. 1195 172.16.1.5 172.16.1.6 ACTIVE aes sha psk 14 01:46:56 D Engine-id:Conn-id = SW:195 IPv6 Crypto ISAKMP SA fd-wv-ro03# fd-wv-ro03# fd-wv-ro03#show crypto ipsec sa peer 172.16.1.6 interface: Tunnel161 Crypto map tag: Tunnel161-head-0, local addr 172.16.1.5 protected vrf: (none) local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) current_peer 172.16.1.6 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 1856, #pkts encrypt: 1856, #pkts digest: 1856 #pkts decaps: 1855, #pkts decrypt: 1855, #pkts verify: 1855 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 1 local crypto endpt.: 172.16.1.5, remote crypto endpt.: 172.16.1.6 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: 0xC97B0D54(3380284756) PFS (Y/N): Y, DH group: group14 inbound esp sas: spi: 0x5FFAE69C(1610278556) transform: esp-256-aes esp-sha-hmac , in use settings ={Tunnel, } conn id: 2737, flow_id: NETGX:737, sibling_flags 80000046, crypto map: Tunnel161-head-0 sa timing: remaining key lifetime (k/sec): (4506750/791) IV size: 16 bytes replay detection support: Y Status: ACTIVE inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0xC97B0D54(3380284756) transform: esp-256-aes esp-sha-hmac , in use settings ={Tunnel, } conn id: 2738, flow_id: NETGX:738, sibling_flags 80000046, crypto map: Tunnel161-head-0 sa timing: remaining key lifetime (k/sec): (4506750/791) IV size: 16 bytes replay detection support: Y Status: ACTIVE outbound ah sas: outbound pcp sas: fd-wv-ro03# fd-wv-ro03# fd-wv-ro03#show ip route static S 192.168.161.0/24 is directly connected, Tunnel161 |
Ciao.


very nice :)
I’m waiting for a blog post that represent the internet speed limits of cisco / fortigate / Juniper firewalls . :-)
what is the different between tunnel to peer?
and what if i want to set this configuration on dialer interface?
thanks,
Michael
This article seems to be the reference for IPsec Site-to-Site (route-based) VPN between FortiGate and Cisco Router.
This helped me greatly to get a VPN tunnel up between my 2 devices (Fortigate 60C and Cisco 881W).
I can ping from the Fortigate LAN to the Cisco LAN however I cannot ping from the Cisco to the Fortigate. I guess I am missing some configuration on the Cisco side.
!##########################################
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
lifetime 28800
crypto isakmp key MyPresharedKey address 10.10.10.106
crypto isakmp keepalive 10 5
!
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
crypto ipsec profile 3DESMD5
set transform-set TS
set pfs group2
interface Tunnel161
ip unnumbered FastEthernet4
tunnel source 10.10.11.71
tunnel mode ipsec ipv4
tunnel destination 10.10.10.106
tunnel protection ipsec profile 3DESMD5
interface FastEthernet4
description OUTSIDE
ip address 10.10.11.71 255.255.255.240
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
interface Vlan1
description INTERNAL
ip address 192.168.51.97 255.255.255.248
ip nat inside
no ip virtual-reassembly in
ip nat inside source list 1 interface FastEthernet4 overload
ip route 0.0.0.0 0.0.0.0 10.10.11.65
ip route 192.168.46.0 255.255.255.0 Tunnel161
access-list 1 permit 192.168.51.96 0.0.0.7
!#########################################
Any help would be greatly appreciated.
Well, if the ping in one direction works (inclusive the echo-reply), your VPN is woring. Good.
Have you reviewed all policies? Please verify the policies on the Forti for both directions!
Hi Johannes,
Thanks for your reply. You were right there was a policy issue on the FG side. All fixed now.
Thanks again.
Hi Johannes,
great post ipsec is up and running.
However i am facing the same issue unable to reach the remote LAN gw from cisco\cisco’s LAN pc’s.
policy is on both direction, also tried VPN-ANY-ACCEPT
If your outside interface is public IP – be sure you exclude the VPN tunnel traffic from being NAT’ed, otherwise your Cisco -> Fortigate traffic will work, but the return traffic will go out to the Internet and not back via the tunnel….
After configuring the cisco router for fotigate100c based on above example the protocol goes down every couple of mins.
Does anyone has an idea on this ?
Good article
Great post. I only had one issue. Everytime I rebooted the Cisco (Cisco 2911), my tunnels would drop. I would have to do a “no ip route 192.168.161.0 255.255.255.0 Tunnel161” then “ip route 192.168.161.0 255.255.255.0 Tunnel161”
and it worked.
I fixed it by removing the ip unumbered portion and giving it an ip and now it works on reboot. So my Cisco CLI commands looked like this:
interface Tunnel161
ip address 172.30.0.1 255.255.255.252
tunnel source 172.16.1.5
tunnel destination 172.16.1.6
tunnel mode ipsec ipv4
tunnel protection ipsec profile FG
Help Please urgent
how to convert this config from cisco to frtigate
crypto isakmp policy 1
encr aes
authentication pre-share
group 2
crypto isakmp key Keeeeeeeey address 213.34.208.190
crypto isakmp keepalive 10 periodic
!
!
crypto ipsec transform-set esp-aes-sha esp-aes esp-sha-hmac
!
crypto map Keeeeeeeey 10 ipsec-isakmp
set peer 213.34.208.190
set transform-set esp-aes-sha
interface Tunnel0
ip address 10.10.10.2 255.255.255.0
tunnel source 195.112.209.210
tunnel destination 213.34.197.241
For the benefit of others:
ISAKMP Policy refers to ‘Phase 1’, this is the same when using a VTI (As per this tutorial) or using a Crypto Map as per your post – which is an example of GRE over IPSec.
Transform Set refers to ‘Phase 2 encryption / Hashing’
Your ‘Tunnel’ interface on the fortigate will be similar to below:
config system gre-tunnel
edit “GRE-Tunnel-Underlay”
set interface “WAN1”
set remote-gw 195.112.209.210
set local-gw 213.34.197.241
end
config system interface
edit “GRE-Overlay”
set vdom “root”
set ip 10.10.10.1/24
set allowaccess ping
set type tunnel
set remote-ip 10.10.10.2/24
set interface “WAN1”
end
It’s not clear from your example as to what traffic you’re matching using the crypto map and whether the Crypto map has been applied to a physical interface either. It may that you’ve only provided the required output.
I am trying to bring up an IPSec VPN between a fortigate (5.2) and a Cisco Router (IOS 15) using VTIs as per your tutorial.
Out of interest what Cisco router and version was your tutorial based on?
The issue I’m having is that although Phase 1 (ISAKM establishes, Phase 2 does not come up.
The cisco reports this error:
*Nov 30 14:50:17.364: IPSEC(ipsec_process_proposal): invalid local address 22.22.22.1
*Nov 30 14:50:17.364: ISAKMP:(1005): IPSec policy invalidated proposal with error 8
*Nov 30 14:50:17.368: ISAKMP:(1005): phase 2 SA policy not acceptable! (local 22.22.22.1 remote 1.1.1.1)
The fortigate reports this issue:
2017-11-30 06:43:06 ike 0:VPN-to-R1:34: notify msg received: NO-PROPOSAL-CHOSEN
2017-11-30 06:43:06 ike 0:VPN-to-R1:34:R1-P2:693: IPsec SPI 0fad1c1d match
2017-11-30 06:43:06 ike 0:VPN-to-R1:34:R1-P2:693: delete phase2 SPI 0fad1c1d
Any suggestions at all would be appreciated.
Resolved Now, the provided output was with a config error not previously present and not accurate of the actual issue I was having – IPSec VPNs and interactions with VRF Lite.
kindly any one can help me for static ip to dynamic ip vpn
FortiGate on HQ i has static IP address but remote side i has cisco 1841 router with dynamic IP address .
Anyone face IPSec Configuration issue with Cisco 2901(F: version 15.1(2)TS and Fortigate (F: Version 6.06)
Please share details for this issse