A few weeks ago I constructed an MRTG/Routers2 template for the Fortinet FortiGate firewalls. I am using it for monitoring the FortiGate from my MRTG/Routers2 server. With the basic MRTG tool “cfgmaker” all graphs for the interfaces are generated automatically. My template is an add-on that appends graphs for CPU, memory, and disk usage, as well as connections and VPN statistics. Furthermore, it implements the ping statistics graph and a “short summary”, which only shows the system relevant graphs.
Similar to all my other MRTG/Routers2 templates I constructed the configuration lines after investigating the MIBs from Fortinet via the MIB Browser. The MIBs can be downloaded directly from the FortiGate GUI under System -> Config -> SNMP. Great.
Note that this template is built upon a single vdom environment. I was running a FortiWiFi 90D with FortiOS v5.2.4, build688. Depending on the number of vdoms or processors, some of the OIDs in the template must be adjusted, e.g. the CPU usage or the VPN statistics.
cfgmaker Configuration
The first step is the generation of the basic *.cfg file for MRTG/Routers2. It adds all currently known interfaces from the FortiGate with their names. (Even the “zone” interfaces as well as the VPN IPsec tunnel interfaces, which is great!) Note that I am using a few more options such as the “show-op-down” or other global options. Please use Google if you don’t know their meaning. ;)
|
1 |
sudo cfgmaker --snmp-options=:::::2 --show-op-down --zero-speed=100000000 --global "routers.cgi*Icon: firewall3-sm.gif" --global "routers.cgi*GraphStyle[_]: mirror" --output=NAMEOFTHEFIREWALL.cfg COMMUNITY@IPADDRESS |
You can delete all global options (expect the ones just created with the cfgmaker command) within the cfg file because they are not needed if running Routers2.
Template
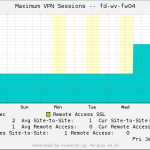
The following template adds the OIDs/graphs for the usage of the CPU, memory, and disk. It also shows the connections (All and IPv6) as well as the VPN stats. (Note that the MIB allows for even more stats such as byte counts for each policy or counts for AV/IPS/whatever features. However, I have not implemented them here.) I am using the same coloring style as in all my other MRTG/Routers2 templates.
You can download my *.cfg template and follow the first comments inside the file which give hints about what to change (search and replace) in order to make the configuration usable for your environment:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 |
################################################################################################################ #Fortinet FortiGate Firewall MRTG/Routers2 Template #Author: Johannes Weber (johannes@webernetz.net) #Homepage: https://weberblog.net #Last Modified: 2016-01-08 ################################################################################################################ ### TO DO #Repace the following values with your own: #COMMUNITYSTRING : SNMP read community #IPADDRESS : IP address of the ScreenOS device #NAMEOFTHEFIREWALL : name of the firewall ### #Change the MaxBytes values of the following targets: #-Disk Capacity #(The CPU and Memory graphs need not to be adjusted because they display percentage usage and not absolute usage.) ### END ################################################################################################################ ##################################################### CPU ###################################################### ################################################################################################################ Target[IPADDRESS_cpu]: 1.3.6.1.4.1.12356.101.4.1.3.0&PseudoZero:COMMUNITYSTRING@IPADDRESS:::::2 Title[IPADDRESS_cpu]: CPU Usage -- NAMEOFTHEFIREWALL MaxBytes[IPADDRESS_cpu]: 100 Options[IPADDRESS_cpu]: gauge Colours[IPADDRESS_cpu]: LIGHT YELLOW#FEED01, BLUE#0000FF, ORANGE#FF6307, VIOLET#FF00FF UnScaled[IPADDRESS_cpu]: dwmy LegendI[IPADDRESS_cpu]: CPU: routers.cgi*Mode[IPADDRESS_cpu]: cpu routers.cgi*ShortDesc[IPADDRESS_cpu]: CPU routers.cgi*InSummary[IPADDRESS_cpu]: yes routers.cgi*Summary[IPADDRESS_cpu]: IPADDRESS_shortsummary ################################################################################################################ ################################################### Memory ##################################################### ################################################################################################################ Target[IPADDRESS_mem]: 1.3.6.1.4.1.12356.101.4.1.4.0&PseudoZero:COMMUNITYSTRING@IPADDRESS:::::2 Title[IPADDRESS_mem]: Memory Usage -- NAMEOFTHEFIREWALL MaxBytes[IPADDRESS_mem]: 100 Options[IPADDRESS_mem]: gauge Colours[IPADDRESS_mem]: ORANGE#FC7C01, GREEN#00CC00, DARK RED#660000, DARK GREEN#006600 UnScaled[IPADDRESS_mem]: dwmy LegendI[IPADDRESS_mem]: RAM: YLegend[IPADDRESS_mem]: Percentage use ShortLegend[IPADDRESS_mem]: % routers.cgi*Options[IPADDRESS_mem]: noo nopercent routers.cgi*GraphStyle[IPADDRESS_mem]: normal routers.cgi*ShortDesc[IPADDRESS_mem]: Memory routers.cgi*InSummary[IPADDRESS_mem]: yes routers.cgi*Summary[IPADDRESS_mem]: IPADDRESS_shortsummary ################################################################################################################ ################################################# Log & Disk ################################################### ################################################################################################################ #Disk Capacity: 1.3.6.1.4.1.12356.101.4.1.7.0 Target[IPADDRESS_logdisk]: 1.3.6.1.4.1.12356.101.4.1.6.0&PseudoZero:COMMUNITYSTRING@IPADDRESS:::::2 Title[IPADDRESS_logdisk]: Disk Usage -- NAMEOFTHEFIREWALL MaxBytes[IPADDRESS_logdisk]: 30050 Options[IPADDRESS_logdisk]: gauge UnScaled[IPADDRESS_logdisk]: dwmy Legend1[IPADDRESS_logdisk]: Log Usage Legend3[IPADDRESS_logdisk]: Peak Log Usage YLegend[IPADDRESS_logdisk]: Usage LegendI[IPADDRESS_logdisk]: Log: ShortLegend[IPADDRESS_logdisk]: b routers.cgi*Options[IPADDRESS_logdisk]: noo nopercent nototal routers.cgi*GraphStyle[IPADDRESS_logdisk]: normal routers.cgi*ShortDesc[IPADDRESS_logdisk]: Disk ################################################################################################################ ################################################## Connections ################################################# ################################################################################################################ Target[IPADDRESS_connections]: 1.3.6.1.4.1.12356.101.4.1.8.0&1.3.6.1.4.1.12356.101.4.1.15.0:COMMUNITYSTRING@IPADDRESS:::::2 Title[IPADDRESS_connections]: Connections -- NAMEOFTHEFIREWALL #MaxBytes is set to an unrealistic high value. This has no effect because there is no percent calculation. MaxBytes[IPADDRESS_connections]: 10000000 Options[IPADDRESS_connections]: gauge Colours[IPADDRESS_connections]: PURPLE#FF00AA, YELLOW#FFD600, DARK PURPLE#7608AA, ORANGE#FC7C01 YLegend[IPADDRESS_connections]: Number of Connections Legend1[IPADDRESS_connections]: Connections Legend2[IPADDRESS_connections]: IPv6 Connections Legend3[IPADDRESS_connections]: Peak Connections Legend4[IPADDRESS_connections]: Peak IPv6 Connections LegendI[IPADDRESS_connections]: Connections: LegendO[IPADDRESS_connections]: IPv6 Connections: ShortLegend[IPADDRESS_connections]: routers.cgi*Options[IPADDRESS_connections]: fixunit integer nomax nototal routers.cgi*GraphStyle[IPADDRESS_connections]: normal routers.cgi*Icon[IPADDRESS_connections]: firewall-sm.gif routers.cgi*ShortDesc[IPADDRESS_connections]: Connections routers.cgi*InSummary[IPADDRESS_connections]: yes routers.cgi*Summary[IPADDRESS_connections]: IPADDRESS_shortsummary ################################################################################################################ ################################################# VPN Sessions ################################################# ################################################################################################################ #Site-to-Site: The number of IPsec VPN tunnels with at least one SA #Remote Access: The current number of users logged in through SSL-VPN tunnels in the virtual domain Target[IPADDRESS_vpn]: 1.3.6.1.4.1.12356.101.12.1.1.0&1.3.6.1.4.1.12356.101.12.2.3.1.2.1:COMMUNITYSTRING@IPADDRESS:::::2 Title[IPADDRESS_vpn]: Maximum VPN Sessions -- NAMEOFTHEFIREWALL MaxBytes[IPADDRESS_vpn]: 1000 Options[IPADDRESS_vpn]: gauge Colours[IPADDRESS_vpn]: TURQUOISE#00CCCC, DARK YELLOW#CCCC00, DARK TURQUOISE#377D77, ORANGE#E97F02 YLegend[IPADDRESS_vpn]: Number of Sessions Legend1[IPADDRESS_vpn]: Site-to-Site IPsec Legend2[IPADDRESS_vpn]: Remote Access SSL Legend3[IPADDRESS_vpn]: Peak Site-to-Site IPsec Legend4[IPADDRESS_vpn]: Peak Remote Access SSL LegendI[IPADDRESS_vpn]: Site-to-Site: LegendO[IPADDRESS_vpn]: Remote Access: ShortLegend[IPADDRESS_vpn]: #This graph shows the MAXIMUM value and not the Average! routers.cgi*Options[IPADDRESS_vpn]: fixunit integer maximum nomax nototal routers.cgi*GraphStyle[IPADDRESS_vpn]: stack routers.cgi*Icon[IPADDRESS_vpn]: padlock-sm.gif routers.cgi*ShortDesc[IPADDRESS_vpn]: VPN routers.cgi*InSummary[IPADDRESS_vpn]: yes routers.cgi*Summary[IPADDRESS_vpn]: IPADDRESS_shortsummary ################################################################################################################ ################################################### Ping ####################################################### ################################################################################################################ #Since mrtg-ping-probe outputs integers, the values are multiplied to have milliseconds reported #i.e., instead of "5" the answer is now "5324" which is interpreted by "Factor[]: 0.001" as 5.324 ms Target[IPADDRESS_ping]: `mrtg-ping-probe -p '1000*max/1000*min' -s IPADDRESS` Title[IPADDRESS_ping]: Ping Times to IPADDRESS #MaxBytes: 10 seconds = 10 * 1000 * 1000 (due to mrtg-ping-probe * 1000 and milliseconds * 1000) MaxBytes[IPADDRESS_ping]: 10000000 Options[IPADDRESS_ping]: gauge Factor[IPADDRESS_ping]: 0.001 Colours[IPADDRESS_ping]: RED#FF0000, WHATEVER#123456, DARKRED#800000, WHATEVER2#654321 routers.cgi*ShortDesc[IPADDRESS_ping]: Ping IPADDRESS routers.cgi*Options[IPADDRESS_ping]: fixunit nomax nopercentile nototal routers.cgi*GraphStyle[IPADDRESS_ping]: range routers.cgi*Icon[IPADDRESS_ping]: clock-sm.gif routers.cgi*Summary[IPADDRESS_ping]: IPADDRESS_shortsummary ################################################################################################################ ################################################ Short Summary ################################################# ################################################################################################################ #Shows no interfaces, except the Wan interface, and: CPU, Memory, Connections, VPN Sessions, Ping Outside routers.cgi*ShortDesc[IPADDRESS_shortsummary]: Short Summary |
Sample Graphs
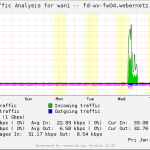
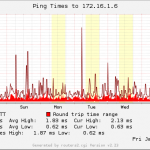
After all, these graphs are generated:
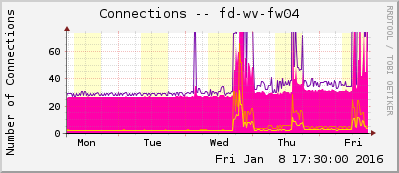
Especially, I am loving the connections graphs, which show the count for all (=IPv4 and IPv6) and IPv6-only connections. Great for a comparison of both protocols.





Versuch mal PRTG.
https://www.de.paessler.com/prtg
Bis 100 Sensoren komplett Free.
Und dann per SNMP MIB die Fortigate abfragen.
ODer die “normalen” SNMP-Abfragen wie z.B.SNMP Datenverkehr
hi
Could you please show me how to add wan traffic to mtrg.cfg?
I test many OIDs but can get the in/out value of bytes.
and always return
$target->[2]{$mode} ‘ did not eval into defined data
thanks a lot
You should use a snmpwalk or the like in order to find the OIDs for different kind of interfaces. If you want to use a GUI, I recommend the free MIB browser: http://www.ireasoning.com/mibbrowser.shtml