My lab rack of 2019 consists of multiple Cisco routers and switches, as well as Juniper ScreenOS firewalls for routing purposes, a Palo Alto Networks firewall, a Juniper SRX firewall, a server for virtualization and some Raspberry Pis. That is: This rack can be used for basic Cisco courses such as CCNA or CCNP, or for even bigger BGP/OSPF or IPsec VPN scenarios since those ScreenOS firewalls are perfect routers as well. Of course, everything is IPv6 capable. Having some PoE-powered Raspberry Pis you can simulate basic client-server connections. A Juniper SA-2500 (aka Pulse Connect Secure) for remote accessing the Lab rounds things up.
I am just writing down a few thoughts on why I have “designed” the rack in that way. It’s basically a reminder for myself. ;)
Let’s have a look at the rack first. I ordered one with wheels for easy transport. Previously the devices were mounted into several 19″ racks in the data center, which was not that movable. ;D Now the rack can be used by any of my colleagues for test purposes. I am using 24 rack units while some are left free for the cables. On the back side, I have two power strips. All power cables disappear in the rack space.
Initial Thoughts
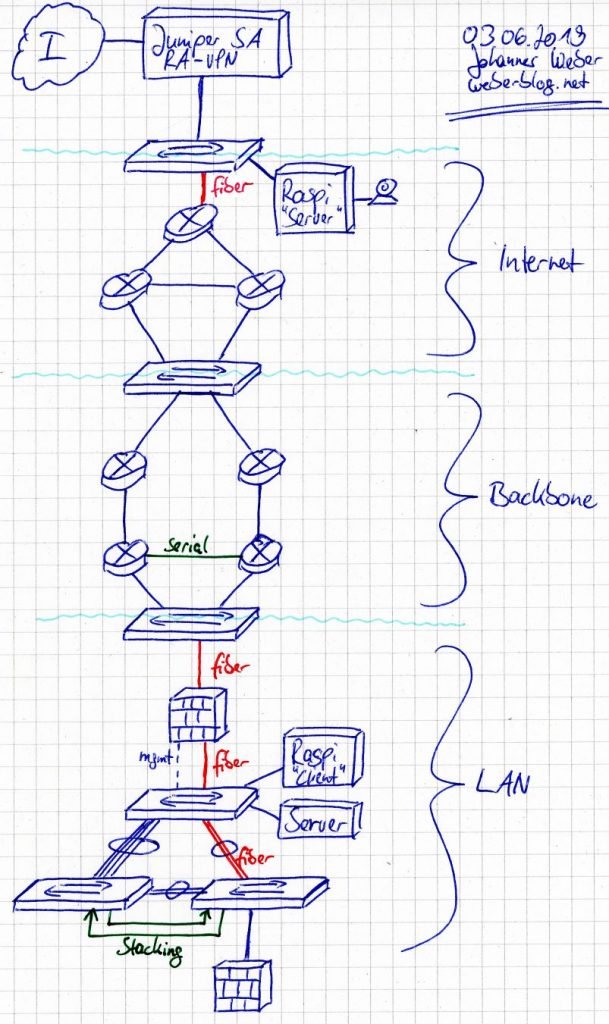
These are the basic ideas about how to use this lab rack. Of course, everything can be changed. Again, a picture is worth a thousand words:
- Remote access connection via a Juniper SA-2500 / Pulse Connect Secure VPN gateway.
- A simple server aka Raspberry Pi with a webcam in order to get some traffic through the lab. The Pi is PoE powered by a small PoE module (yellow cable from the upper switch, a Cisco C3750G-48PS).
- Simulation of an ISP with three routers aka Juniper ScreenOS SSG 140 firewalls capable of BGP. All of them with one 6-port SFP Gigabit PIM module in the back. Oh, they were that expensive those days… No need for them here, but, you know, because I can. ;)
- Simple Cisco switch (C3560-24PS-S) in between to be flexible about the port connections.
- Simulation of the own backbone routing with four Cisco routers (2x 2851, 2x 2811). Note the very short blue serial cable between the two 2811 routers.
- Again a simple Cisco switch (C2960-24TC-L) in between for being flexible.
- Palo Alto Networks PA-3050 firewall for separating the internal network from the “Internet”. This device is not licensed, hence I don’t have a current PAN-OS. However, it fits for basic policies and VPN setups. Of course, it is connected via fiber cables. ;)
- Internal LAN with three Cisco switches (2x C3750G-48TS, 1x C3750G-48PS with PoE), interconnected with a couple of network cables to play with STP. The last two switches are connected via stacking cables, too.
- Simple client aka Raspberry Pi with PoE power (laying above the three switches) used for accessing the upper Pi throughout the complete lab.
- A Juniper SRX firewall which can be used as a router-on-a-stick or the like.
- Finally an old IronPort M160 aka Dell PowerEdge R200, Intel Pentium Dual CPU E2200 @ 2.20GHz, 4 GiB DDR2 Memory. It can be used for VMware ESXi to use a couple of VMs, or just as a real server.
What’s missing?
- Serial console server for using all serial ports directly. Currently, you can only use SSH to access those appliances. This does not fit for an initial configuration. ;(
- Remotely controllable power switches for using the lab completely off-site.
Featured image “Colours and Casks” by Jens Comiotto-Mayer is licensed under CC BY 2.0.