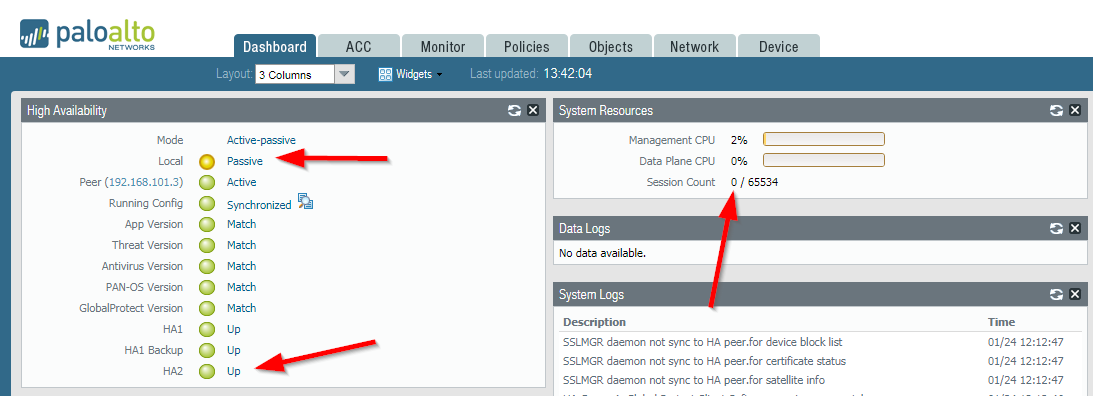
Just a quick note concerning the session sync on a Palo Alto Networks firewall cluster: Don’t trust the green HA2 bubble on the HA widget since it is always “Up” as long as the HA interface is up. It does NOT indicate whether the session sync is working or not. You MUST verify the session count on the passive unit to be sure. Here are some details:
I was changing the VLANs on a few switches to which a Palo Alto cluster was plugged in (PA-500, PAN-OS 7.1.14). Though the VLANs I used for the HA2 interfaces on the switches did NOT match the HA2 link was displayed as “Up”. And indeed, the session sync did not work as indicated by a session count of 0 on the passive device:
Note that this is not the case for the HA1 bubble which immediately turns red if no communication takes place. Also note that this behaviour for HA2 is independent of the transport mode for this data link which can be ethernet, ip, or udp.
Lessons learned: You MUST verify whether the session sync works or not. You can either look at the session count on the system resources widget on the passive device which should be greater than 0, or you can use the following command (on the passive device again) a couple of times to verify that the “received” packets increase:
|
1 |
show high-availability state-synchronization |
Example:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 |
admin@ThisIsTheSecondFirewall(passive)> show high-availability state-synchronization -------------------------------------------------------------------------------- State Synchronization Status: Complete -------------------------------------------------------------------------------- state synchronization to peer device enabled: no (device not in active state) -------------------------------------------------------------------------------- state synchronization messages processed since system up message enable version sent received -------------------------------------------------------------------------------- session setup yes 9 0 1429 session teardown yes 9 0 1719 session update yes 9 0 13495 predict session add yes 9 0 187 predict session delete yes 9 0 157 predict session update yes 9 0 4 ARP update yes 1 0 36 ARP delete yes 1 0 0 MAC update yes 1 0 0 MAC delete yes 1 0 0 IPSec sequence number update yes 3 0 0 ND update yes 1 0 0 ND delete yes 1 0 0 DoS Aggregate entry update yes 1 0 0 DoS Class Tbl IP update yes 1 0 0 DoS Class Tbl IP delete yes 1 0 0 DoS Block Tbl IP update yes 1 0 0 DoS Block Tbl IP delete yes 1 0 0 A/A session setup no 9 0 0 A/A session statistics no 9 0 0 A/A packet forward using HA2 no 9 0 0 Return MAC Update yes 1 0 0 Return MAC Delete yes 1 0 0 V6 Return MAC Update yes 1 0 0 V6 Return MAC Delete yes 1 0 0 HA2 monitor message yes 1 0 0 predict session modify yes 9 0 0 -------------------------------------------------------------------------------- |
And of course you should test some failover scenarios before going live. ;)
Featured image “Sync” by John Graham is licensed under CC BY-NC-ND 2.0.


Enable “HA2 Keep alive” to avoid this. :)
Uh, you’re absolutely correct. Hm. I wonder why I haven’t seen it back then… Shame on me.