I initially wanted to show how to use NTP authentication on a Pulse Connect Secure. Unfortunately, it does not support NTP over IPv6, which is mandatory for my lab. Ok, after I calmed down a bit, a configured it with legacy IP and got NTP authentication running. ;) Here’s how:
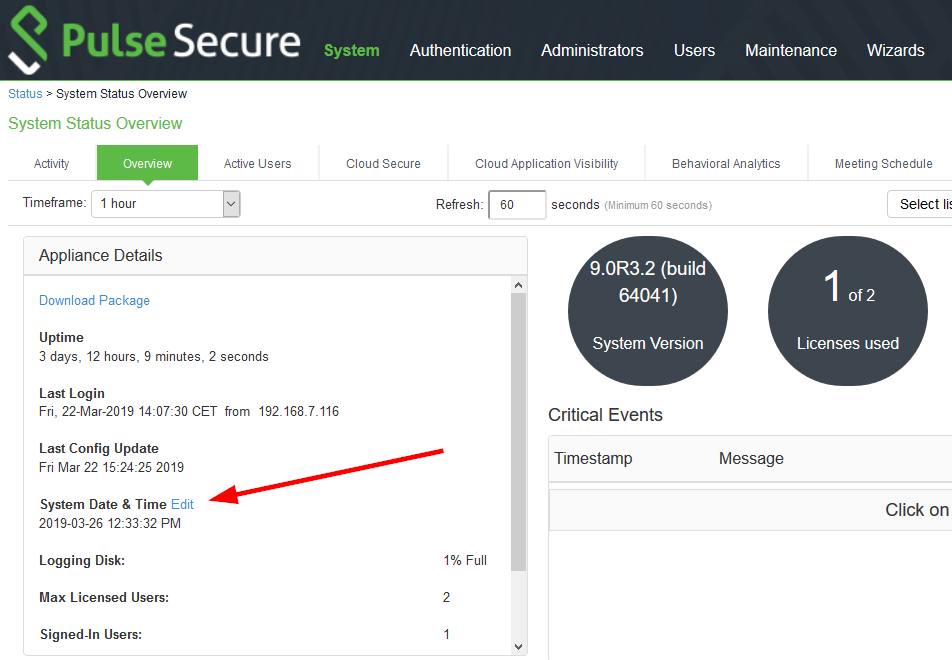
I am using a virtual Pulse Connect Secure with version 9.0R3.2 (build 64041). Finding the menu to change the NTP servers is not that easy, because it is *not* within the “System” tab at the top of the administration page, but behind the “Edit” link at the system status overview, section appliance details:
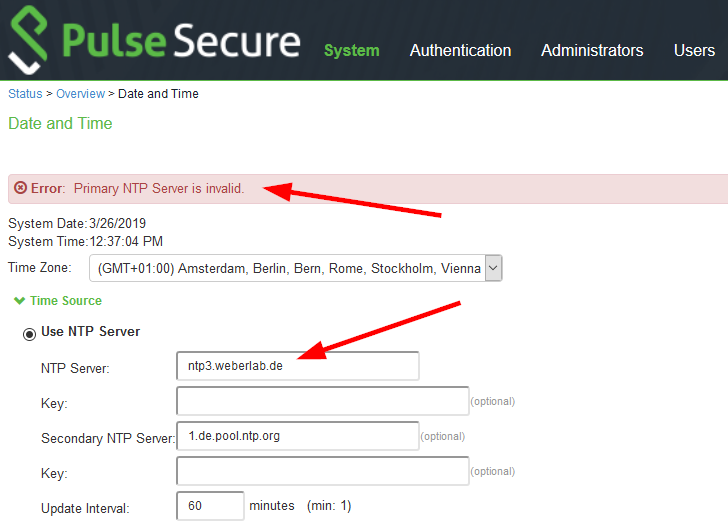
No IPv6 ;(
Trying to add an IPv6-only NTP server results in an error message “NTP Server is invalid”:
Astonishing since Pulse Secure does quite a good job when it comes to IPv6 coverage such as their clientless remote access VPN which works great with IPv6-only. My report on Twitter is here.
But only Legacy IP
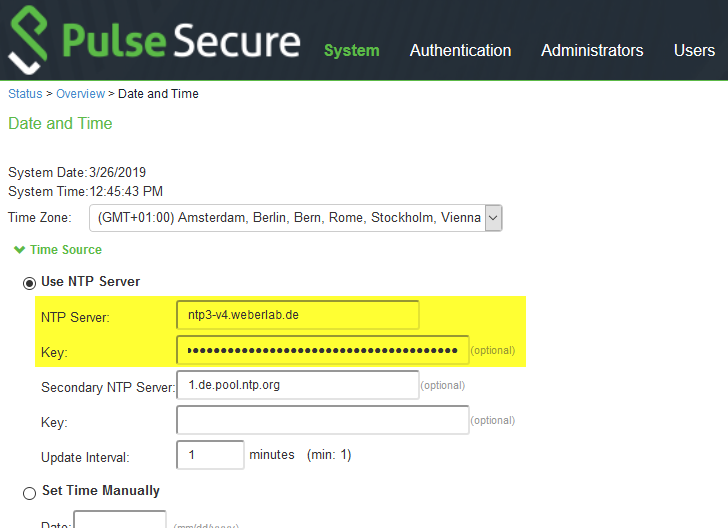
Using an FQDN which has an A record for legacy IP as well, you can configure NTP authentication with MD5/SHA-1, while the key must be in the form of “ID SHA1 key”, in my case 13 SHA1 01ff36b6b7bb0a9028e15cf1620b6308a901d3d2:
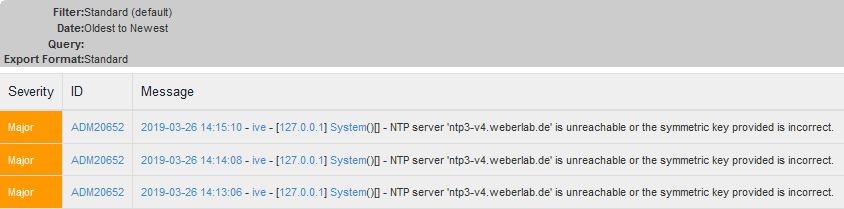
What I really like is the immediate check whether the key is working or not. If you don’t get an error, everything is correct. (Though I would prefer a log entry stating authentication success.) Using a wrong key you’re getting this:
as well as a log entries:
FIN. ;D
Featured image “connected” by rauter25 is licensed under CC BY-NC 2.0.



Hi, Thanks for your post about Pulse Connect Secure NTP settings.
I was looking for the NTP settings where I expected them to be, rather than in the weird place they actually are.
Cheers!
Kev