After the implementation of DNS and DNSSEC (see the last posts) it is good to do some reconnaissance attacks against the own DNS servers. Especially to see the NSEC or NSEC3 differences, i.e., whether zone walking (enumeration) is feasible or not.
For many different kinds of DNS reconnaissance the tool dnsrecon can be used. In this post I will focus on the -z option which is used for DNSSEC zone walking, i.e., walk leaf by leaf of the whole DNS zone.
Installation
There are official installation instructions (great!) that work without any errors. On my Ubuntu 16.04.1 LTS it worked exactly like this:
|
1 2 3 4 5 6 |
sudo apt-get install libavahi-compat-libdnssd1 git-core python-setuptools sudo easy_install netaddr sudo easy_install dnspython git clone git://github.com/darkoperator/dnsrecon.git cd dnsrecon/ ./dnsrecon.py |
Note the helping page which gives a few hints how dnsrecon can be used to do dictionary or brute force attacks, or even how to use Google to search for subdomains and hosts.
DNSSEC Zone Walking
To walk a zone use the -z option. In the following example I am walking through my own domain weberdns.de which uses only NSEC (instead of NSEC3) and is therefore prone to zone walks. The enumeration starts at line 21:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 |
weberjoh@jw-nb12-lx:~/dnsrecon$ ./dnsrecon.py -d weberdns.de -z [*] Performing General Enumeration of Domain: weberdns.de [*] DNSSEC is configured for weberdns.de [*] DNSKEYs: [*] NSEC ZSK RSASHA256 03010001cd46f5d7c54812fefcdc5177 bffff3427c1f1f218d4c9a43ba1a255d 2d384ac4735f93a34046a7714e07b7d0 150e9d2481f37d10f860ed0aa098da1f 83fb7d63ba42cfb4e54e9d9dfd8118fc bdd66ff82c7a8cfba8f314c31fe7ae86 1f1b99601ffc3a429cc9153b212fafb9 bb582fc8d3ee1ab3aa0f975e941b0d19 5bb4d80f [*] NSEC KSk RSASHA256 03010001d41723e51faa719b1ddc09b4 1052b5fd0233c43c9d772b89a3b2b2ba 4610336433ffda994043d9831643783e 86d71aead9b37c324c3390f480e93977 821d126772c24707fb4ac62e33623443 c59d9529c1be97b180fe648fd612e4a5 a7e282115f2fc042eaed596d001ac54f ef51cf9084be8913c689f342bbe77dc9 551da1b03bb72096000bb05a890aa069 bc366f12bd99e9d49ea630e7142f413d 2e95f0f19237001812dcc3a7f96b4288 e40a3dbcc478f63828e9af4748423763 1852531c895cf5c6130078dd3c3b02f0 4a9fb391dc2f7aee53a71baa34e7fb92 e6e11757a4e59581e995bc81839d437e bfe4e66bf5a0b5093b537b1a8b3349dd ea42bf7b [*] SOA ns1.weberdns.de 80.154.108.230 [*] NS ns2.weberdns.de 213.61.29.182 [*] Bind Version for 213.61.29.182 9.9.5-3ubuntu0.8-Ubuntu [*] NS ns1.weberdns.de 80.154.108.230 [*] Bind Version for 80.154.108.230 9.9.5-3ubuntu0.8-Ubuntu [*] NS ns1.weberdns.de 2003:51:6012:110::a07:53 [*] Bind Version for 2003:51:6012:110::a07:53 9.9.5-3ubuntu0.8-Ubuntu [*] MX mail.weberdns.de 80.154.108.237 [*] MX mail.weberdns.de 2003:51:6012:110::15 [*] A weberdns.de 80.154.108.230 [*] AAAA weberdns.de 2003:51:6012:110::a07:53 [*] Enumerating SRV Records [-] No SRV Records Found for weberdns.de [+] 0 Records Found [*] Performing NSEC Zone Walk for weberdns.de [*] Getting SOA record for weberdns.de [*] Name Server 80.154.108.230 will be used [*] A weberdns.de 80.154.108.230 [*] AAAA weberdns.de 2003:51:6012:110::a07:53 [*] A fg.weberdns.de 80.154.108.233 [*] AAAA fg.weberdns.de 2003:51:6012::4 [*] AAAA host-dane.weberdns.de 2003:51:6012:110:e995:f904:c293:f36a [*] AAAA host-dane-self.weberdns.de 2003:51:6012:110:b1dc:bada:5bf5:ca54 [*] AAAA host-dnssec.weberdns.de 2003:51:6012:110:c2b6:ca25:284f:9033 [*] AAAA ip.weberdns.de 2003:51:6012:110::19 [*] A ip.weberdns.de 80.154.108.235 [*] A lx.weberdns.de 80.154.108.239 [*] AAAA lx.weberdns.de 2003:51:6012:110::9 [*] A mail.weberdns.de 80.154.108.237 [*] AAAA mail.weberdns.de 2003:51:6012:110::15 [*] A ns0.weberdns.de 80.154.108.226 [*] AAAA ns0.weberdns.de 2003:51:6012:120::a16:53 [*] A ns1.weberdns.de 80.154.108.230 [*] AAAA ns1.weberdns.de 2003:51:6012:110::a07:53 [*] A ns1-v4.weberdns.de 80.154.108.230 [*] AAAA ns1-v6.weberdns.de 2003:51:6012:110::a07:53 [*] A ns2.weberdns.de 213.61.29.182 [*] A ns3.weberdns.de 193.24.225.53 [*] A pa.weberdns.de 80.154.108.228 [*] AAAA pa.weberdns.de 2003:51:6012::2 [*] A sub.sub.weberdns.de 203.0.113.3 [*] A ttl-long.weberdns.de 198.51.100.255 [*] A ttl-short.weberdns.de 198.51.100.0 [*] A txt.weberdns.de no_ip [*] A viola.weberdns.de no_ip [*] AAAA webmail.weberdns.de 2003:51:6012:110::19 [*] A webmail.weberdns.de 80.154.108.235 [*] AAAA www.weberdns.de 2a01:488:42:1000:50ed:8588:8a:c570 [*] A www.weberdns.de 80.237.133.136 [+] 576 records found |

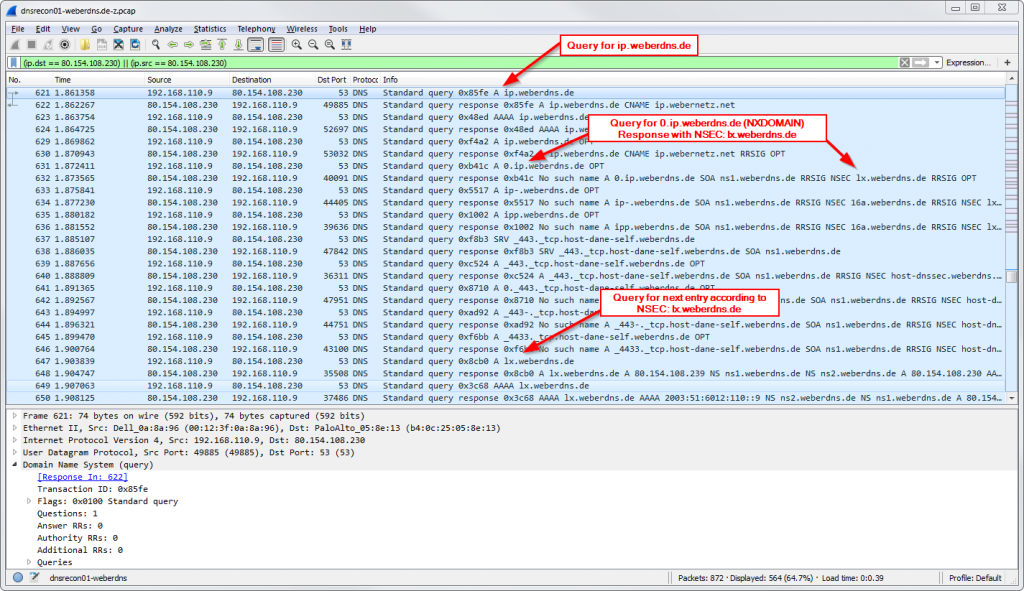
That is: All (!) FQDNs are exposed within a few seconds. No brute-force or dictionary attacks are needed. The NSEC records reveal the whole zone!
However, note that not all records are listed though, e.g., my TLSA (DANE) or SSHFP records. Furthermore, not all types are listed correctly, e.g., CNAMEs. But it’s just because the dnsrecon tool does not query all of them. It is not because it’s not possible.
Following is a Wireshark (tcpdump) capture that shows an example while dnsrecon was running:
Trying to walk NSEC3
Well, as per design (RFC 5155), this is not possible. NSEC3 uses hashes instead of plain text domain names. That is, zone walking is not feasible anymore. In the following example I am trying to walk through my domain sshfp.net which uses NSEC3. Starting with line 23, nothing happens:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
weberjoh@jw-nb12-lx:~/dnsrecon$ ./dnsrecon.py -d sshfp.net -z [*] Performing General Enumeration of Domain: sshfp.net [*] DNSSEC is configured for sshfp.net [*] DNSKEYs: [*] NSEC3 ZSK RSASHA512 030100019ffa1f794b286687079b7dd2 660b6e0ee56a471c070a90a8213eb6d4 5e058fbbd0eb57bdb62300c0be18a146 1f60747417661ae057bc17903b98cdf0 6ac5e885ceec04d06d72d791723f019d a2599ed6d1f814212a0f6842a5c276a5 3bdd0a7fad63bbac04a6af2dc5c684cb ac97479368076d44237ac4955bfa8e4a 3a5d38dca8c13b7d951b3caabfb65b14 2f1fdc7051654526b733db1c37cf54c4 4f7652619f619e35062a11dfd0ce71ee 60e61d8b1891db29e90f3ded4a8eb1a7 cbcb9456d0b35d176a7667381fc6b466 f1092a11741f1ec9ed5072324ab6af87 84e2cdc5963a11b4b008c8cd84616701 acb942feb5775d327b04a22ff8d45497 8e09361b [*] NSEC3 KSk RSASHA512 03010001cb77f7287ebe3f0f6a144f9f 3d427a84c15d99d1e0abd620d6e38637 9cc6c1dbd102e3d9c928e0228bd4d75b 6cfa7643647bbd678e69bebcfd3ca125 b1c1a37747268035da5e513e08b84bfd 5e9b11e15041b7d6d7908b9b6a69fb0f 5609d543acfb848a9eef4df897deef56 56eae7336c0f82347ecadc7884baa799 b7438c8c2a0435664a36e97f1d235a01 d4e4b574f072ba0308e47d9b8c65cad7 363e0062a8b050d36ad4c63e6f811f34 4b3f3dc6ab20da8f5c0758aa82e278d4 cb4f3d3978dc71600012a30d3afc9ad6 e9ca57ae8ea751ffafd11432171a7926 5ca6766696b0f8c836c77313c532cce8 c48fc69eb50293b01d8e72039130b612 b7d2bcf9 [*] SOA ns1.weberdns.de 80.154.108.230 [*] NS ns3.weberdns.de 193.24.225.53 [*] Bind Version for 193.24.225.53 9.9.5-3ubuntu0.8-Ubuntu [*] NS ns1.weberdns.de 80.154.108.230 [*] Bind Version for 80.154.108.230 9.9.5-3ubuntu0.8-Ubuntu [*] NS ns1.weberdns.de 2003:51:6012:110::a07:53 [*] Bind Version for 2003:51:6012:110::a07:53 9.9.5-3ubuntu0.8-Ubuntu [*] NS ns2.weberdns.de 213.61.29.182 [*] Bind Version for 213.61.29.182 9.9.5-3ubuntu0.8-Ubuntu [*] MX mail.weberdns.de 80.154.108.237 [*] MX mail.weberdns.de 2003:51:6012:110::15 [*] A sshfp.net 80.154.108.235 [*] AAAA sshfp.net 2003:51:6012:110::19 [*] Enumerating SRV Records [-] No SRV Records Found for sshfp.net [+] 0 Records Found [*] Performing NSEC Zone Walk for sshfp.net [*] Getting SOA record for sshfp.net [*] Name Server 80.154.108.230 will be used [*] A sshfp.net 80.154.108.235 [*] AAAA sshfp.net 2003:51:6012:110::19 [+] 2 records found |
That’s it. If you want to hide your DNS zones, use NSEC3. But as already noted many times, security by obscurity is not a good design at all. ;) If you want to understand your DNS replies easily, NSEC3 is not preferred.
Another Tool: dnssecwalk
Just after finishing this post I found another tool that perfectly fits for walking DNSSEC zones. It comes out of the great THC-IPv6 toolkit from van Hauser. (Google for installation guides. There are many out there.) The usage of the dnssecwalk tool is really easy and it reveals all (!) records incl. the TLSA ones:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 |
weberjoh@jw-vm09-nmap:~$ dnssecwalk dnssecwalk v1.2 (c) 2015 by Marc Heuse <mh@mh-sec.de> http://www.mh-sec.de Syntax: dnssecwalk [-e46] dns-server domain Options: -e ensure that the domain is present in found addresses, quit otherwise -4 resolve found entries to IPv4 addresses -6 resolve found entries to IPv6 addresses Perform DNSSEC NSEC walking. Example: dnssecwalk dns.test.com test.com weberjoh@jw-vm09-nmap:~$ weberjoh@jw-vm09-nmap:~$ weberjoh@jw-vm09-nmap:~$ dnssecwalk 8.8.8.8 weberdns.de Starting DNSSEC walking on server 8.8.8.8 about weberdns.de. Found: 16a.weberdns.de. Found: 16aaaa.weberdns.de. Found: 16dual.weberdns.de. Found: 32a.weberdns.de. Found: 32aaaa.weberdns.de. Found: 32aaaa-long.weberdns.de. Found: 32dual.weberdns.de. Found: 32dual-long.weberdns.de. Found: 64a.weberdns.de. Found: 64aaaa.weberdns.de. Found: 64dual.weberdns.de. Found: fg.weberdns.de. Found: host-dane.weberdns.de. Found: _443._tcp.host-dane.weberdns.de. Found: host-dane-self.weberdns.de. Found: _443._tcp.host-dane-self.weberdns.de. Found: host-dnssec.weberdns.de. Found: ip.weberdns.de. Found: lx.weberdns.de. Found: mail.weberdns.de. Found: _25._tcp.mail.weberdns.de. Found: ns0.weberdns.de. Found: ns1.weberdns.de. Found: ns1-v4.weberdns.de. Found: ns1-v6.weberdns.de. Found: ns2.weberdns.de. Found: ns3.weberdns.de. Found: pa.weberdns.de. Found: sub.sub.weberdns.de. Found: ttl-long.weberdns.de. Found: ttl-short.weberdns.de. Found: txt.weberdns.de. Found: viola.weberdns.de. Found: webmail.weberdns.de. Found: www.weberdns.de. Done, 35 entries found. |
Featured image: “Füße” by Robert Agthe is licensed under CC BY 2.0.



There is also ldns-walk from the ldns distribution.
https://www.nlnetlabs.nl/projects/ldns/
Greate tip! Works perfectly! Thanks!