… the whole Internet breaks down. So happened on a Palo Alto with a DNS proxy and a (slightly misconfigured) anti-spyware profile.
All network clients had a single DNS server configured, namely the DNS proxy of the Palo Alto. And as a single network client requested an URL that was classified as “spyware”, the Palo correctly (!) blocked the DNS session from its DNS proxy to the Internet. Unluckily, this session stayed active for a long time (with drop-all-packets) since many DNS requests were traversing through it. But since it stayed blocked, the Internet was “unavailable” for all end-users.
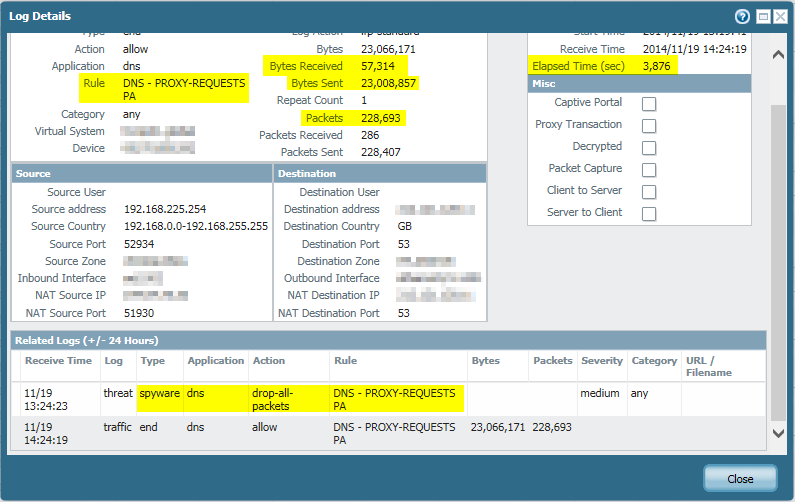
Here is a screenshot of that session. Note the duration of it (more than 1 h) and the threat that was recognized as spyware due to the malicious DNS request. The bytes received (57,341) were much smaller than the bytes sent (23,008,857) which shows that many DNS requests were initiated but never answered. The packets sent counter had a value of more than 200.000 while the packets received had only 286. ;)
The quick solution is to manually clear this session. Either via the GUI (Monitor -> Session Browser) or via the CLI ( clear session id <id>). However, as long as the end-user manually types in the same malicious URL, this problem arises again and again.
A long-term solution is to have a unique Anti-Spyware Profile with a DNS signatures action of “alert” for the outgoing DNS requests (= DNS proxy to Internet DNS servers), while the profile for the incoming DNS requests (= user to DNS proxy) has a profile with “block”. That is, malicious requests from a user only block the DNS session from that particular user while the main DNS proxy session stays active and functional.
Featured image “Wasserschlange” by Benny is licensed under CC BY-NC 2.0.


Hi Johannes,
what about blocking malicious DNS queries before they can reach a firewall?
Cheers, Andreas