While preparing for some Palo Alto Networks certifications I read something about the antivirus capabilities of blocking viruses via email by sending an SMTP response code of 541 to the sender (link). This was new for me since I thought the Palo Alto would only block IP connections (TCP RST) but not send layer 7 messages (SMTP codes). But actually, it does so by spoofing the IP address of the destination SMTP host. Cool stuff. Of course, I needed to test this. Here we go. ;)
Basically, I sent an email with a virus through the firewall in order to see if it blocks it.
What is Code 541?
At a first glance, I was wondering about the “541” response code. I have not heard about it until now. I have not found any good resources about that on Google. There is nothing in RFC 3463 (Enhanced Mail System Status Codes). Hm. At least, here is a german site that lists this code with a description as “Recipient Address Rejected – Blacklist, Anti-Spam, Mailfilter/Firewall Block”.
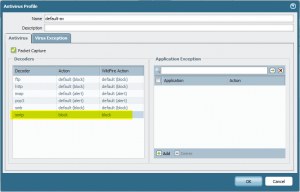
Antivirus Profile with Block
The default antivirus profile has an action for smtp of “alert”. In order to block viruses, “block” must be specified:
Of course, this antivirus profile must be used in the appropriate security policy rules for the SMTP mail transfer.
EICAR Testfile sent through PA
I sent a virus (EICAR testfile) from my mail server (Postfix) to an external email address. This SMTP connection goes through the Palo Alto to my MTA (Cisco ESA). Due to the antivirus profile on the PA, this email is blocked. Following are a few listing of this behaviour:
This is the mail.log on the Postfix installation. Note line 6, the longest line, which says “status=bounced […] 541 5.4.1 Content blocked by Palo Alto Networks Firewall”:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
Aug 27 11:26:46 jw-vm10 postfix/smtpd[23809]: connect from unknown[192.168.125.10] Aug 27 11:26:47 jw-vm10 postfix/smtpd[23809]: 022F115F9BA: client=unknown[192.168.125.10] Aug 27 11:26:47 jw-vm10 postfix/cleanup[23812]: 022F115F9BA: message-id=<53FDA44D.8010902@webertest.net> Aug 27 11:26:47 jw-vm10 postfix/qmgr[25919]: 022F115F9BA: from=<johannes@webertest.net>, size=1146, nrcpt=1 (queue active) Aug 27 11:26:47 jw-vm10 postfix/smtpd[23809]: disconnect from unknown[192.168.125.10] Aug 27 11:26:48 jw-vm10 postfix/smtp[23813]: 022F115F9BA: to=<johannes@webernetz.net>, relay=2003:51:6012:124::15[2003:51:6012:124::15]:25, delay=0.83, delays=0.2/0.05/0.57/0, dsn=5.4.1, status=bounced (host 2003:51:6012:124::15[2003:51:6012:124::15] said: 541 5.4.1 Content blocked by Palo Alto Networks Firewall (in reply to end of DATA command)) Aug 27 11:26:48 jw-vm10 postfix/cleanup[23812]: 1766B16092F: message-id=<20140827092648.1766B16092F@webertest.net> Aug 27 11:26:48 jw-vm10 postfix/qmgr[25919]: 1766B16092F: from=<>, size=3117, nrcpt=1 (queue active) Aug 27 11:26:48 jw-vm10 postfix/bounce[23814]: 022F115F9BA: sender non-delivery notification: 1766B16092F Aug 27 11:26:48 jw-vm10 postfix/qmgr[25919]: 022F115F9BA: removed Aug 27 11:26:48 jw-vm10 postfix/local[23816]: 1766B16092F: to=<johannes@webertest.net>, relay=local, delay=0.37, delays=0.16/0.01/0/0.21, dsn=2.0.0, status=sent (delivered to maildir) Aug 27 11:26:48 jw-vm10 postfix/qmgr[25919]: 1766B16092F: removed |
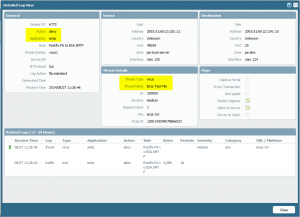
The PA threat log reveals the deny for this connection:
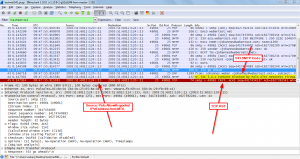
A packet capture on the Postfix servers also shows the SMTP 541 message as well as the TCP RST packet sent from the Palo Alto with an IP address of the real MTA:
Note that the real MTA (in my case a Cisco ESA) sees the incoming connection until it is lost due to the disruption from the Palo Alto:
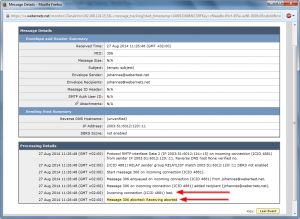
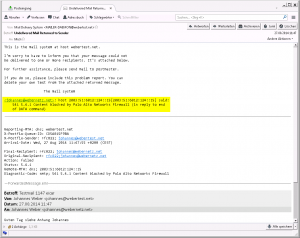
The sender of the email will get a “Mail Delivery System” email with the subject of “Undelivered Mail Returned to Sender” (or the like). In my test case, this looks like that:
Links
- Palo Alto: CNSE Study Guide
- Palo Alto: Threat Prevention Deployment Tech Note
Featured image “stopp” by Silvision is licensed under CC BY-ND 2.0.



Great information. Thanks!
Hi,
We plan to use this feature. But do you know how email clients (outlook, thuinderbird, …) react to 541 response. Do they correctly inform the user of the kind of error (virus/spam)?
Thank you
Yes, thats exactly what is shown on my last screenshot. The sending user gets an email with this “Undelivered Mail ….” text.
(But I can’t tell you if any “normal” user is able to interpret this text correctly. ;))
Hi! We are using PANOS 7.08 and choose the response action reset-both, the mail can be block. However the sender’s mail server retry until timeout and no undelivered mail returned to sender. Do you have any advice? Thank you!
Hello Cliff,
sorry, I have not tested it within the last months.
Was it working with an older PAN-OS version?
Have you captured the traffic? That is, is PAN answering with an SMTP error code (which is not accepted by the sending MTA), or is PAN not answering?
Have you another sending MTA to test it? (The EICAR “virus” can be used without any fear.)
Hi Johannes,
Thanks for your promptly reply. This is new setup that not test in older PAN-OS version. The new PAN-OS AV response action had been removed “block” and introduce new option ” reset-both “, “drop” etc.
Since the PA was locate at center, so it have difficulty to capture the ingress and egress traffic of the PA and MTA sever. Maybe need some time to get back you later. Thanks! : )