If you are already familiar with DNSSEC this is quite easy: How to sign a delegated subdomain zone. For the sake of completeness, I am showing how to generate and use the appropriate DS record in order to preserve the chain of trust for DNSSEC.
Scenario
You already have a DNSSEC signed zone, in my example: weberdns.de. Beside hostnames within this domain you have a delegated zone with its own nameservers (= NS records). Now you must not only sign this new zone, in my example: dyn.weberdns.de, but you must also preserve the chain of trust. This is done by the delegation signer DS record which is placed in the parent zone. I assume that you already have the delegated zone working, i.e., NS records for it, zone file (SOA), etc.
Signing the Subdomain Itself
(Just a recap from my previous blogposts.) That is: Generating the KSK and ZSK, adjusting its ownership to be readable by BIND, and inserting the NSEC3 parameters in order to use NSEC3 rather than NSEC:
|
1 2 3 4 5 |
cd /etc/bind/keys/ sudo dnssec-keygen -a RSASHA512 -b 4096 -3 -f KSK -r /dev/urandom dyn.weberdns.de sudo dnssec-keygen -a RSASHA512 -b 4096 -3 -r /dev/urandom dyn.weberdns.de sudo chown bind:bind Kdyn.weberdns.de.+010+* sudo rndc signing -nsec3param 1 0 20 0832d537abd450eb07316484eeeae871 dyn.weberdns.de |
Using the DS Record
Note that this process is exactly the same as for your primary domain. For your domain you already have sent the DS record to your parent zone (such as .de or .com). Now it’s much easier since you’re owning both, the domain (in my case: weberdns.de) AND the subdomain (dyn.weberdns.de). That is:
1) Generate the DS record from the KSK you created for your subdomain. Use the small dnssec-dsfromkey program with the -2 option to have only the SHA-256 output (refer to IANA: Delegation Signer (DS) Resource Record (RR) Type Digest Algorithms):
|
1 2 |
weberjoh@vm16-ns0:/etc/bind/keys$ dnssec-dsfromkey -2 Kdyn.weberdns.de.+010+17463.key dyn.weberdns.de. IN DS 17463 10 2 670228E75B1F114E688BB11BC61D9816D9EB3B0170598FC8DE2FF66F9F34192C |
This resource record has an owner name of the delegated subdomain (dyn.weberdns.de) and the following four fields (refer to RFC 4034 “Resource Records for the DNS Security Extensions” section 5: The DS Resource Record):
- the key tag 17463 which identifies the KSK,
- the algorithm used for the KSK 10 = RSASHA512 as used while creating the KSK above,
- the digest type 2 = SHA-256 and
- the digest of the KSK (and some more fields) itself.
2) Place this single DS record into your parent zone. After a reload you’re done. ;)
Tests
Note the “ad” flag for all of those queries. (Only when resolved by a DNSSEC validating resolver.) You can now query the NS records for your subdomain:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
weberjoh@nb15-lx:~$ dig dyn.weberdns.de ns +noadditional ; <<>> DiG 9.10.3-P4-Ubuntu <<>> dyn.weberdns.de ns +noadditional ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 28959 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 5 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;dyn.weberdns.de. IN NS ;; ANSWER SECTION: dyn.weberdns.de. 40 IN NS ns2.weberdns.de. dyn.weberdns.de. 40 IN NS ns1.weberdns.de. dyn.weberdns.de. 40 IN NS ns3.weberdns.de. ;; Query time: 2 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Thu Feb 01 15:48:25 CET 2018 ;; MSG SIZE rcvd: 174 |
its DNSKEYs (KSK and ZSK):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 |
weberjoh@nb15-lx:~$ dig dyn.weberdns.de dnskey +multi ; <<>> DiG 9.10.3-P4-Ubuntu <<>> dyn.weberdns.de dnskey +multi ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 32005 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;dyn.weberdns.de. IN DNSKEY ;; ANSWER SECTION: dyn.weberdns.de. 52 IN DNSKEY 257 3 10 ( AwEAAe3LK5bOygeJFQJ+hxItyeYB5Xfx2pwZnWl8JyRK yddHtn3XMZ8hxzbh268KW4IKG3R18dChOlbtevaiSRBg TUyEAj2/IJoOAdBCWu6Xc7d7v8A888zWhT+qrYk4k1sb 7vW/r2CaAZnp1A8OHUomfPTCpoy9D8rx4+GDcLf1j/a0 aHdpQ4Y0NUZ6bmnsz/f3YvsId1K/U9eVbPXliU8srahc TP3RRubXNi7VKt8sadSxzHqlYURYeGIyFaILpJ7N/rIO 7ob9psO1VOhHDqhPv1e1gVx8LW8d4+4MJ6uozIueop5s jthAtaU8w3GUJguAfUAg/1tedDrFtsXEPUdtVNqxSv1H FpfZc6/t7HkMsabp2escSiaLD3RrSsCYlWGkkL1bc9Ye +8OzMTyzaphqxBh83SLFPfzBae9tsRY2XIZBpMHO1HMn apjK03nt22fm6VxuY9sI9wCxJ8eTuICm2K6W3k/s8OEC fl5Q+3j8phUqk5A1/PYbC+92y56kxpwrqJ8kTkJ3rSUE gIV5efUMBEh9YA2vL8xruOLoO9GG56BSLof/rbABNYXY l+PNvgalibYDVRFlhBdgbhtvHg6GCGHTriN5JvSkjkHP 9mw8XQ8upjE/E0CkV2Xdj71Dk8eR8thkRYuOBvQFi7wb hnmYh4uYXPUkOvWgin0l4RqDPq7b ) ; KSK; alg = RSASHA512; key id = 17463 dyn.weberdns.de. 52 IN DNSKEY 256 3 10 ( AwEAAbiC3omZWzDtVx/nlwIEEgY1wrAQktqggJXNq50U +Xapj2+RQE4s7dNLU7AtJ+jvr/nplax61coz/2Na9YEc RE1LGpcZdrFH3iDZez+UcOY1GPll5xPGgpSPtSaL1j8M fUQgAw85ZmFQ6rUptYOpa3/w40n3MrgiOFyu8IoXhP7O QKICmHFAVcB6nurPZK6m52Vny/5R7CtHBmxGyU/Xcm6D oimWZPj56+QeQbthiPdSLNYNB8QoLWTPEuzjLdFaz7Jv Bp1n0tdqPS27OErcWV4eja6as1OyTODreo0b0pkM6Ulp 4xkY/7A/VbVFv9l/bHTIVFW/jXisk6Yr2/LwVy58/lGj oJ9SfpJnnelxYo0HMbp8zsQ2xGNzvH783NXsc0LeIATl WeBJrkW3hL4rJFc/5rT71RwHveukofFjXjk008Sgj1TD 6Gyx6I4XVi8AcbhTNajfh4K+elZMnJRnewQqk4g5KYBi ucyX0gR+JNSejqD4+mWuIyzKTh+cMrUsIBkXYQRzwlRf S8A0Zs9eVAQXVlKVgPEorj7fp1hnn6Ao8A2P7MeO5pdg ilFpSEIW3IbwtKqjPWY7wvVOo9Ms2TCdgePC34xxKGub gNQTBGU9MSlg16K2kvCavSYAgzQRUfzKtknPowr0ODz/ sBNRLH2swqvxU1rkkjZlS3RbW6+n ) ; ZSK; alg = RSASHA512; key id = 58340 ;; Query time: 2 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Thu Feb 01 16:00:09 CET 2018 ;; MSG SIZE rcvd: 1108 |
as well as the DS record in the parent zone:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
weberjoh@nb15-lx:~$ dig dyn.weberdns.de ds +noadditional ; <<>> DiG 9.10.3-P4-Ubuntu <<>> dyn.weberdns.de ds +noadditional ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 63311 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;dyn.weberdns.de. IN DS ;; ANSWER SECTION: dyn.weberdns.de. 3574 IN DS 17463 10 2 670228E75B1F114E688BB11BC61D9816D9EB3B0170598FC8DE2FF66F 9F34192C ;; Query time: 1 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Thu Feb 01 15:48:31 CET 2018 ;; MSG SIZE rcvd: 92 |
Querying a hostname within the delegated subdomain shows the “ad” flag as well (line 7), which proves its authenticity:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
weberjoh@nb15-lx:~$ dig test.dyn.weberdns.de aaaa +noadditional +noauthority ; <<>> DiG 9.10.3-P4-Ubuntu <<>> test.dyn.weberdns.de aaaa +noadditional +noauthority ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14053 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 3, ADDITIONAL: 5 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;test.dyn.weberdns.de. IN AAAA ;; ANSWER SECTION: test.dyn.weberdns.de. 31 IN AAAA 2001:db8::cafe ;; Query time: 2 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Thu Feb 01 15:51:15 CET 2018 ;; MSG SIZE rcvd: 207 |
Testing NSEC3 with a unvalid name to show up the NSEC3 records works as well:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
weberjoh@nb15-lx:~$ dig foo.dyn.weberdns.de +dnssec ; <<>> DiG 9.10.3-P4-Ubuntu <<>> foo.dyn.weberdns.de +dnssec ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 5641 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 0, AUTHORITY: 6, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;foo.dyn.weberdns.de. IN A ;; AUTHORITY SECTION: dyn.weberdns.de. 43 IN SOA ns1.weberdns.de. webmaster.webernetz.net. 2018020103 3600 900 2419200 180 dyn.weberdns.de. 43 IN RRSIG SOA 10 3 60 20180303135653 20180201125653 58340 dyn.weberdns.de. TB7oUhD8TsINmVPLquJs9x3Yh3jxFVOZ6QgYgo/XrKCt00PofMozlrpv SiFS+JGxIkFakode5sO9Y19I5SCufTdQNqoersphb+MKwQfJbxrPLvsc uQ29TS6tDJQftJK1RVUIt/OsYSGrEfnDy2Lfmk3LJ5YlGMNit0PtcN+E PPa2gJw/CTQ9XFakT5AhCjln31LxtgZ5f2aUxneRJGmQBfVTWZn2lt7t Jz5l2ndcNpgn/SETG86wAeiYURa+pR8vXoeac7roApjp0egaczCAdaM2 LtvEIKhHgKyTuvwn9qzCwk1oNBPdXmSPaN968taPE6kMxZmAtaK2k67n m8tpbs/PAgSe6lr77fsigwFWeWpw6gjp5tqWKnxgllXzlS+JjJxb+H4v LWYQN3jN4z+otN7f6JMFXexgDQPUpHdCYWS1ycOJcUdCqFDV76DlfQ6h l/mNM0wJ5suyHN33IWWURS20oKEeeyFmg6Bdkm1CxTEo8vBQ79rQ7X/H UKk+A77eynC/7s/G0+JA4xxOFbjOGr5/alUXl7fg+c3gBc4bvmKCpPCQ SfwEIVsmvy9eQjj6UwV6bY7akh5ATKQXz3nj/Xs/BW2Un2ZHjTdwUucn lKEzf4QtR4os1bjwEBv+dJI5HssgMoTASrIuAb4iBS/tUrBljR4DWAXC 2IyEUPNpXZs= H6SC3HM4FG03MFD0QRUBDV77V1FIVQ4F.dyn.weberdns.de. 43 IN RRSIG NSEC3 10 4 180 20180223093045 20180124091717 58340 dyn.weberdns.de. jgssNdglYqo+AQT7VajEmnvZfqH7WccNMRnMBJrygrkiq7hUULmCq+KB t7/ArkLRz8MZUteZi0BWS/tX9mi6YqyCElVYmyqklx6EGwAjCy9fnZWr EAt0NPaJpqtoS1dmH9zRBlrZdXbnSp+6hvtCfewp6z4UrsMNVAr6w3Se kR74N+S3Fyh0pQLKwwYsu2YNliyj2hE4LCGYLnIRz9qJm8umTZ1PJhZa +lLx+1VDyAFfw4rjvp8ecZesCjAPhQzLfJJrqody6MKe6BOGUbjmpXAn XGD4Ri9Bfa/kRN0YmlZWl0O1fA1QvHe6vgGn2mS1ABMA7gKhZY7XharU A7XmY8jQgqUDBRiDdPmlNJOXxSlkwdtOT4I1XI2hUCPW1nYekLAe7Eqe ooJrxkBh9gbq9ot4OOaKnClcPZVkqiyGnDEkDq2DPEPt5XrGL0WDU3Zx zfIgQP9yhjprw6Iv6BPpL4ArKjEkUatQI0r+1HDDuUkqpU8lFmYI1jRW TJtjhxLB9Tqc4Ccpb+L62gnkHWLEM5s9c8LXszF7+jGylJn1+OgtL7K3 ZTfhNknW9NYsr7m2HitITqnXMJN9ymwIhHyYmLCyLB+PFP9zCfBUerSU 5Cdj7TToJK1d9PmZ8j4JcOHuT9uAr6hq3FKGHQ5sGsJxEYc5jVy1smBO QJQ8+3zkXns= H6SC3HM4FG03MFD0QRUBDV77V1FIVQ4F.dyn.weberdns.de. 43 IN NSEC3 1 0 20 0832D537ABD450EB07316484EEEAE871 IM0M1N63G2L933N9HGBGORO4ENCVDA17 CNAME RRSIG V0D0EQKT3FBKC6KH6EGEPEGV8UIKMGU6.dyn.weberdns.de. 43 IN RRSIG NSEC3 10 4 180 20180303134247 20180201124247 58340 dyn.weberdns.de. kpm6kPZE7fBxk+8d9FXnaFW0gJn8NxAU0zhtJIQUE2CZAn2TGwaH+PMv 0m6Vi37WXFR2Kh5KAo6sRPEKO72zyTkNlm20bybxSPzWXwUNThCNjjJw BDbK6j/QxaslbarwU5gKoCBhnJ2RWpYZQGLuBEwyS+MmPA0QBAIZ7Kk5 av8UkEVPld0U9UYbDHrg6JKOSd8YnnVpXwIvA4DDBhknAkbZj7adRK0m /LrMqNeLF6jLyi73v/lBBAvHq8i94bFGKutFMA0S/0pzZzrHtNJnnXb6 S58RwaO0Hv44tHhKVeF8RfmOOeFK7U8ZO+8PANmB3pLmtKOBTdoUW8Dn ReDAw7d2TvGHZgidOF5YE3POhlP8st2AplPgv8Nl+yhg0xKIry65ujAn //3X7vucm3g+QXgbDSoP/obbKEvGvPV2/ssroqFYTma06/U6Z9AWqHLd v2eAWgrxmy4Y8/yFUF+AQYwsyv2YLAmmRN5vd51jKnbRIeK11rSX5ruq HUu+agzqOAxSpmwHgTYZbH7dN/jvEstOnVC++/DkgcbUp0MkqsJSymwc 523lLHuVoe7bn4oIz7GMJRBT4DSGN+8mbBUhPHcie92v0cKZlCdVjCNP UKSx3/GodNekFHp8Z75ShaGwQB0WIsGCt6y6IRSVpvK8p65lWyHvpN1B +KXVHFGj0Ag= V0D0EQKT3FBKC6KH6EGEPEGV8UIKMGU6.dyn.weberdns.de. 43 IN NSEC3 1 0 20 0832D537ABD450EB07316484EEEAE871 3O9A3PFM37R703AH1C1GNO6K2R5BE36F NS SOA RRSIG DNSKEY NSEC3PARAM TYPE65534 ;; Query time: 2 msec ;; SERVER: 2003:de:2016:120::a08:53#53(2003:de:2016:120::a08:53) ;; WHEN: Thu Feb 01 16:14:13 CET 2018 ;; MSG SIZE rcvd: 2013 |
That’s it! Congrats.
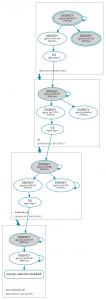
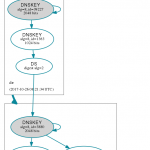
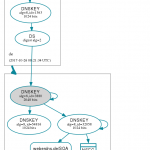
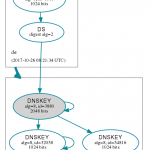
Some more DNSViz
Of course you can use DNSViz again to graph the chain of trust. For my test hostname this looks like that: http://dnsviz.net/d/test.dyn.weberdns.de/dnssec/
During my implementation of this delegated subdomain I queried DNSViz after each step about the SOA record for the the subdomain which showed these graphs:
- Delegated zone was neither signed nor did the DS record exist
- Delegated zone was signed but the DS record did not exist
- Completely signed and secure
Featured image “Vorhängeschlösser mit Zahlenschloss” by Marco Verch is licensed under CC BY 2.0.


Hello,
thank you for this great post.
I’m owning a domain name and I’m hosting the dns server. It’s configured with DNSSEC. I’m intending to use a delegated subdomain on Google Cloud Plateform with Cloud DNS. I’ve created the subdomain DNS, and I’ve configured the delegation on the parent, as well as taking the DS record from the public key. But now the configuration is stalled to this step ‘Delegated zone was signed but the DS record did not exist’. I’ve written down the DS record myself in the parent record, so it should be there, but any request to my dns server (the parent) just returns the SOA.
Any idea?
Hello y0m,
that sounds like your DNS server does not have the DS record. For whatever reason. Maybe you have a syntax error?
It’s hard for me to troubleshoot you issue, since I don’t have any more information about your servers, used versions, and so on.
Cheers
Johannes
Here are informations anonymized.
I’m using BIND 9.14 on FreeBSD, with DNSSEC for the parent zone.
And for the child zone, I’m using Google Cloud DNS with DNSSEC.
Do you need more informations?
parent.zone$ORIGIN .
$TTL 180
parent.zone IN SOA ns.parent.zone. hostmaster.parent.zone. (
2019 ; serial
21600 ; refresh (6 hours)
1800 ; retry (30 minutes)
1209600 ; expire (2 week)
180 ; minimum (3 minutes)
)
parent.zone. IN NS ns.parent.zone.
parent.zone. IN NS ns1.registrar.zone.
parent.zone. IN A 1.2.3.4
parent.zone. IN AAAA dead::beef
ns.parent.zone. IN A 1.2.3.4
ns.parent.zone. IN AAAA dead::beef
$include /usr/local/etc/namedb/keys/Kparent.zone.+008+12345.key
$include /usr/local/etc/namedb/keys/Kparent.zone.+008+54321.key
gcp.parent.zone. IN DS 56789 8 2 sha256token
gcp.parent.zone. IN NS ns-cloud-a1.googledomains.com.
gcp.parent.zone. IN NS ns-cloud-a2.googledomains.com.
gcp.parent.zone. IN NS ns-cloud-a3.googledomains.com.
gcp.parent.zone. IN NS ns-cloud-a4.googledomains.com.
child.zone(Google Cloud DNS with DNSSEC)gcp.parent.zone. 21600 IN SOA ns-cloud-a1.googledomains.com. cloud-dns-hostmaster.google.com. 3 21600 3600 259200 300
gcp.parent.zone. 21600 IN NS ns-cloud-a1.googledomains.com.
gcp.parent.zone. 21600 IN NS ns-cloud-a2.googledomains.com.
gcp.parent.zone. 21600 IN NS ns-cloud-a3.googledomains.com.
gcp.parent.zone. 21600 IN NS ns-cloud-a4.googledomains.com.
personal.gcp.parent.zone. 300 IN A 34.35.36.37
*Google Cloud DNS informations for registrar setup, in this case: the parent zone*
Type Data
NS
ns-cloud-a1.googledomains.com.
ns-cloud-a2.googledomains.com.
ns-cloud-a3.googledomains.com.
ns-cloud-a4.googledomains.com.
DS
56789 8 2 sha256token
Well, this looks good at a first glance. Especially this line:
“gcp.parent.zone. IN DS 56789 8 2 sha256token”
When you’re on the FreeBSD machine, what’s the output of something like:
“dig gcp.parent.zone. ds @localhost”
Is it returning the DS record? It should.
(Just to be sure: You have incremented the serial number and reloaded the zone, did you?)
I’m getting this:
$ dig gcp.parent.zone. ds @localhost
; <> DiG 9.14.1 <> gcp.parent.zone. ds @localhost
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 33018
;; flags: qr aa rd; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
; COOKIE: dafd459e746736d3204b73eb5cd2cbf60645fda2e545ddfc (good)
;; QUESTION SECTION:
;gcp.parent.zone. IN DS
;; AUTHORITY SECTION:
parent.zone. 180 IN SOA ns.parent.zone. root.parent.zone. 2019 21600 1800 1209600 180
;; Query time: 0 msec
;; SERVER: ::1#53(::1)
;; WHEN: mer. mai 08 14:30:46 CEST 2019
;; MSG SIZE rcvd: 114
I've always incremented the serial in the SOA, I've hidden this a bit, but right now with all the tests I've made, it's 2019050714, which is the date + a 2 digits number. I've never had to reconfig 99 times a day.
As you can see, that's just like I would have not written the DS record in the parent zone.
Hm, that’s strange. Maybe there is a typo in the DS record in your zone? Or any other typo? Is “named-checkconf -z” okay? Is it showing your most current serial number?
This is what is looks like on my DNS server, when asking for the DS of the child zone:
###
weberjoh@vm24-ns0:~$ dig dyn.weberdns.de. ds @localhost
; <<>> DiG 9.11.3-1ubuntu1.7-Ubuntu <<>> dyn.weberdns.de. ds @localhost
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 28558 ;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ; COOKIE: be250f559c800ce6ec34c9775cd2d8b563a1099a7d76ac04 (good) ;; QUESTION SECTION: ;dyn.weberdns.de. IN DS ;; ANSWER SECTION: dyn.weberdns.de. 3600 IN DS 45918 10 2 29E4AE014492DEED9610422977D3AEC6CC8C42CBD08A4E5919E3FCCE 75553B21 ;; Query time: 0 msec ;; SERVER: ::1#53(::1) ;; WHEN: Wed May 08 13:25:09 UTC 2019 ;; MSG SIZE rcvd: 120 ### My DS record in the zone file is: "dyn.weberdns.de. IN DS 45918 10 2 29E4AE014492DEED9610422977D3AEC6CC8C42CBD08A4E5919E3FCCE75553B21" Sorry, I don't have any more ideas right now...
I’ve generated the DS record from the DNSKEY record this way:
$ dig gcp.parent.zone. dnskey @ns-cloud-c1.googledomains.com | dnssec-dsfromkey -f – gcp.parent.zone
gcp.parent.zone. IN DS 56789 8 1 40-DIGIT-HASH
gcp.parent.zone. IN DS 56789 8 2 SHA256-TOKEN
The named-checkconf -z does not report any error, and the line for the parent.zone shows:
zone parent.zone/IN: loaded serial 2019050714 (DNSSEC signed)
I clearly don’t understand :)
Just to let you and readers know, I’ve found the origin of my problem. I’m using DNSSEC since 2015 or so, and at the time I had set up snippets to help me sign zone every time I’m making changes. A specific option in the
dnssec-signzonecommand was removing DS records from the signed zone.-g
Generate DS records for child zones from dsset- or keyset- file.
Existing DS records will be removed.
That was a terrible idea, I don’t even remember why I first added this options, even though I remember clearly to have taken some time to read options and what they are doing.
My issue is fixed now. My Google Cloud DNS child zone (subzone, subdomain) is linked to my parent zone.
Is it possible create DNSSEC chain of trust for local root zone
Say if I have root domain domainX.loc and subdomains : subdomainY. domainX.loc and
subdomainZ. domainX.loc. How would I create chain of trust without using ROOT-SERVERS.net
Hey Mundile,
yes, it is. For your subdomains, you simply have to do the same steps as with any other subdomain. However, your local recursive DNS server (which is DNSSEC validating) needs to know the “root” DNSKEY for your local root zone. You’ll have to put this KSK of your zone as a trust anchor into it.
Note: This only applies if you have 1) an authoritative DNS server which you are using for DNSSEC signing AND 2) a separate recursive DNS server for DNSSEC validation. If you only have one single DNS server for both, you don’t need this setup, because your authoritative DNS server won’t validate DNSSEC, as he already has the zone file itself.
Cheers
Johannes
Thanks Johannes. However, what will be dnssec-validation ( yes | auto | no) at the local root DNS server as Chain of Trust starts from there.
Also in this scenerio (local root zone) should I use managed keys or trusted keys or any like in the case of public root zone.
Hi Mundile,
please have a look at this tutorial from Carsten Strotmann. It will probably answer all your questions: https://dnsworkshop.de/local-augmented-root-zone.html
Thank you for the link.
I have just moved our domain over to DNSSEC and had an unexpected result.
We are using WHM with Powerdns got everything working except to a subdomain that’s in it own zone: sapphire.cfts.co.
Test results here: https://dnssec-analyzer.verisignlabs.com/sapphire.cfts.co
Possible to advise because I do not have a clue.
Hey Peter,
ok, it’s probably a little too late to reply. ;) Have you solved your issue? I just looked up your “zone” but it seems that “sapphire.cfts.co” is just an A record?
https://dnsviz.net/d/sapphire.cfts.co/dnssec/
Ciao
Johannes
Hi Johannes,
I like your posts. They do help me to understand DNSSEC. But I have a stupid question. I have 2 servers hosting the same subdomain. May I sign the subdomain with different ZSK and KSK, and then upload Both DS keys to the parent zone server?
Hi William,
thanks for your feedback.
When you’re talking about “two servers hosting the same subdomain”, are they typically in the primary/secondary role, or do you really have two different zone files on both servers? In the first case, you only need a single KSK and ZSK, since the (signed) zone files are transferred from the primary to the secondary.
If you really have two independent primary servers with their own zone files for the *same* zone (which is kind of weird, but maybe you do split-DNS that way), uh, then I don’t know right off the box. AFAIK, technically it would work if you have two DS records at the parent zone. As long as one correct path exists, the zone is signed correctly. But I am not quite sure, to be honest.
Cheers
Johannes
Ok, I asked a few people at Twitter about this question. Here are their answers: https://twitter.com/jpmens/status/1281150376859836416
That is:
“I believe that is possible by inserting the DS of both independent KSK into the parent zone. I think this corresponds to “Model 2” of https://tools.ietf.org/html/draft-ietf-dnsop-multi-provider-dnssec-05#page-5”
and
“Correct — but you also have to cross import ZSKs. This is described in Model 2 also.”