Uh, I wasn’t aware of so many different printing protocols. Do you? While I was trying to solve a little printing problem I took a packet capture of three different printing variants over TCP/IP: Raw via TCP port 9100, LPD/LPR via TCP port 515, and Apple’s AirPrint which uses the Internet Printing Protocol IPP. As always, you can download this pcap and have a look at it by yourself.
In all three cases, I printed a simple demo page on my “HP LaserJet 200 colorMFP M276n” printer. Two times from a Windows 10 PC (from a different IPv4 subnet, hence routed and some SNMP packets) and one time from an iPhone (AirPrint, same layer 2 network, some kind of auto-discovery via IPv6). Download the pcap (7zipped, 125 KB):
Open it with Wireshark and browser through it. The “list of printing protocols” on Wikipedia indeed shows those three variants:
Raw 9100
Raw printing is done via TCP port 9100. It is also called HP Jetdirect, or the like. Wireshark has no protocol dissector for this raw printing (little discussion here). You’ll find it via “tcp.port eq 9100”:
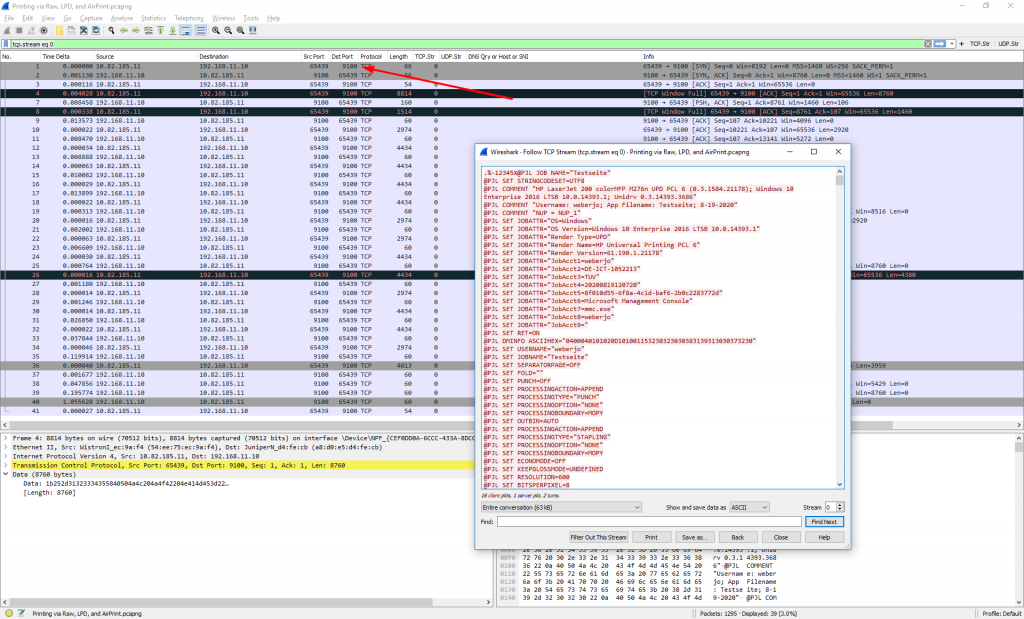
LPD/LPR
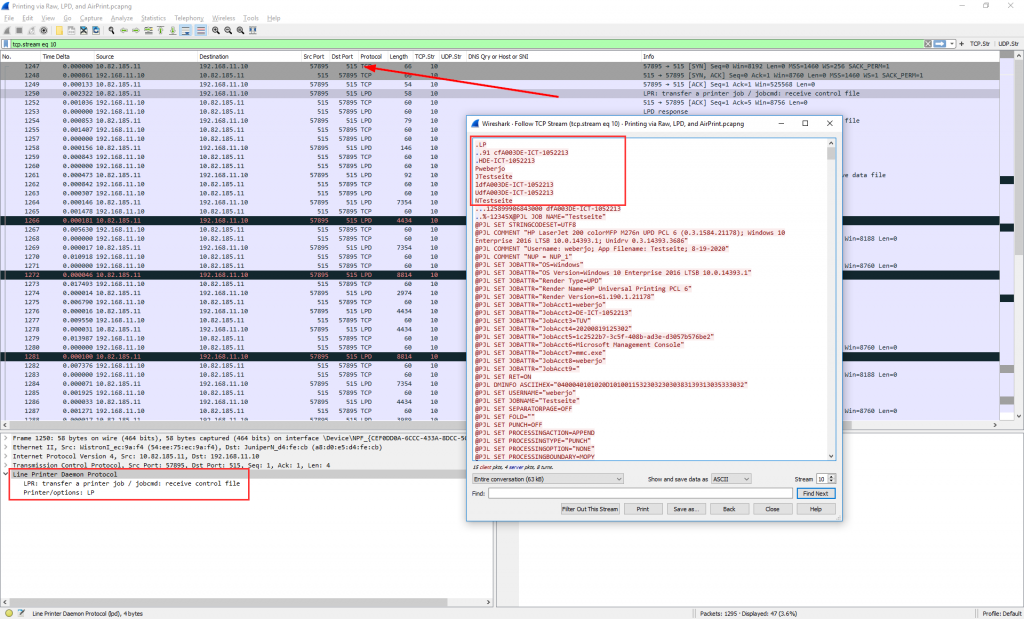
The Line Printer Daemon protocol/Line Printer Remote protocol (or LPD, LPR) uses TCP port 515. Wireshark’s display filter is “lpd” while you can find the whole stream with “tcp.port eq 515” or the like. It seems like the mere print data is encoded in the same way as the Raw variant:
AirPrint
Apple’s AirPrint uses the Internet Printing Protocol IPP on TCP port 631 (I have never heard of it). In my case, the iPhone found the printer via some MDNS discoveries that are shown in the trace as well. My printing of a single page took about 10 TCP/UDP streams and roughly 1200 packets. Uh. Hard to troubleshoot, but working without any configuration. ;) Filter for the iPhone’s MAC address in the trace to find all appropriate packets: “eth.addr == d4:a3:3d:97:60:6d”:

Filtering for “ipp” shows only some HTTP-like lines, while there are much more packets involved in the “tcp.port eq 631” flows:

Challenge
Can you manage to extract the printed pages out of this trace? ;D
Challenge Solved
Fortunately, a reader of the blog, Gerard Fuguet, did a great tutorial video on how to extract all those printed pages. Thanks a lot, man! Have a look at it:
Photo by Museums Victoria on Unsplash.



Hi Johannes, there also exists pure IPP. AirPrint uses IPP with a Baby-PDF format if I remember correct.
IPP is what most Linux systems use for printing.
Hi Johannes, would like to learn more from you on extracting the printed pages from the trace. I was only able to retrieve a printer logo from tcp.port 9100, and was unable to make sense on how to proceed with the following data portion.
To be honest, I’ve no idea as well. 😂
But luckily, Gerard Fuguet left a comment some weeks ago explaining how to do it. 👇🏻
Challenge completed!!! :)
SOLUTION:
2 test print pages from Windows, in Germany language. First, under 9100 PCL at 12:07:21 time
Second test from LPD/LPR page at: 12:53:03
3rd page from AirPrint is from the website https://ip.webernetz.net/ about IP public information of client who do the request. Interesting things shows like browser agent, request time (that in that example is 19.08.2020 12:36:33)
HOW I SOLVED?
For PCL, follow TCP stream and put the client direction against server. RAW content and save. Then you can use software from GhostScript, exactly the GhostPCL component ( from official website here https://ghostscript.com/releases/gpcldnld.html ). The trick is convert it to PDF. This is the command I use for that task:
gpcl6win64 -dNOPAUSE -sDEVICE=pdfwrite -sOutputFile=test1.pdf test1.pcl
The -dNOPAUSE is for not to ask for every page you convert, in that case is not necessary.
For LPD/LPR, is almost the same like PCL 9100, but you need delete the first LPD/LPR part, that is (in that case):
.LP
.91 cfA003DE-ICT-1052213
HDE-ICT-1052213
Pweberjo
JTestseite
ldfA003DE-ICT-1052213
UdfA003DE-ICT-1052213
NTestseite
..125899906843000 dfA003DE-ICT-1052213
Last, for AirPrint, you need look at the IPP packet, specifically looking for IPP Request (Send-Document). The wireshark filter is:
ipp.operation_id == 0x0006
Then, look at the data (expand the subtree of Internet Printing Protocol) and save it, export byte packets and name the file to .pdf extension and… magic occurs!!! (in your pcap, the packet is the number 1097)
Thanks for that, I learn a lot!
Wow! Thanks for your solution. Great read! Kudos!
(Fun fact: I didn’t really know how to do it myself. Luckily you left a cool tutorial here. 😂)
Hey, you did a great job! I tried to repeat your actions but my attempts were not successful, can you tell me more about getting PCL from TCP stream?
Hey! Don’t worry, thanks to you, I decided to do a video on YouTube, so hope things are better clearer now! :)
https://youtu.be/gy1GXOP9iTc
Be Good, Be Hackers!!!
Great, Gerard, thanks a lot for your tutorial video. I just linked to it in the blog post above.
Currently attempting to profile a statically addressed printer using ClearPass (RADIUS server with device profiling enabled). The goal is to classify the endpoint correctly as a printer, but the profiling attempt is failing due to insufficient data received.
Setup:
Device Type: Printer (static IP, no DHCP)
Ports open on firewall: 80, 515, 631
Observations from Wireshark PCAP (Nmap-based scan):
Port 80 (HTTP): Printer responds to HTTP requests, but the HTTP header does not contain a User-Agent field.
Port 515 (Line Printer Daemon Protocol):
Data is returned (e.g., 40-byte payload), but no device-specific attributes are identifiable.
Port 631 (IPP):
Printer responds with HTTP 405 Method Not Allowed, indicating the method used (likely GET or POST) is not supported by the device.
Question:
1. What do these responses suggest about the printer’s capabilities and why the profiling is failing?
2. Are these behaviors typical for statically addressed printers?
3. Does the lack of a User-Agent or method support limit fingerprinting?
Interesting questions. Unfortunately, I cannot really help you in detail. Just a few thoughts from my side:
– Have you tried to use SNMP to query some values for your profiling? E.g. a serial number or the like?
– Using Port 515 (LPD) won’t succeed, in my opinion.
– Concerning Port 80: Can you try to get some other information, maybe a serial number again, through the HTTP admin/status site?
Thank you for your input, Johannes.
1. Unfortunately, SNMP is disabled in our environment due to security policies, so we’re unable to query profiling attributes through that protocol.
2. Will further research on this
3. Just to clarify—are you referring to the embedded EWS page when you mention the HTTP admin/status site?
You’re welcome. ;)
1) SNMPv3 (with authentication/encryption) is secure to use. Maybe you should give it a try? I’m talking about convincing the CIO. 😂
3) I don’t know what an “EWS” page is. :( I’m talking about the admin HTTPS page. My printer shows its serial number after logging in as an admin.
I wish I could.
1. We have over 4L endpoints (desktops, printers, scanners, projectors, etc.) so little bitscep>\tical of implementing snmp due to it being a threat to performance. SNMP will solve everything though
3. We are using many different models, one of them is HP LaserJet MFP 329 DW. can I login into device through interface or by logging in via URL