In some situations, you want to manage your firewall only from a dedicated management network and not through any of the data interfaces. For example, when you’re running an internal data center with no Internet access at all but your firewalls must still be able to get updates from the Internet. In those situations, you need a real out-of-band (OoB) management interface from which all management traffic (DNS, NTP, Syslog, Updates, RADIUS, …) is sourced and to which the admins can connect to via SSH/HTTPS. Another example is a distinct separation of data and management traffic. For example, some customers want any kind of management traffic to traverse through some other routing/firewall devices than their production traffic.
Unfortunately, the Fortinet FortiGate firewalls don’t have a reasonable management port. Their so-called “MGMT” port is only able to limit the access of incoming traffic but is not able to source outgoing traffic by default. Furthermore, in an HA environment you need multiple ports to access the firewalls independently. What a mess. (Little exception: You can use the set ha-direct enable option in the HA setup which sources *some* but not all protocols from the Mgmt interface. But only when you’re using a HA scenario. Reference.)
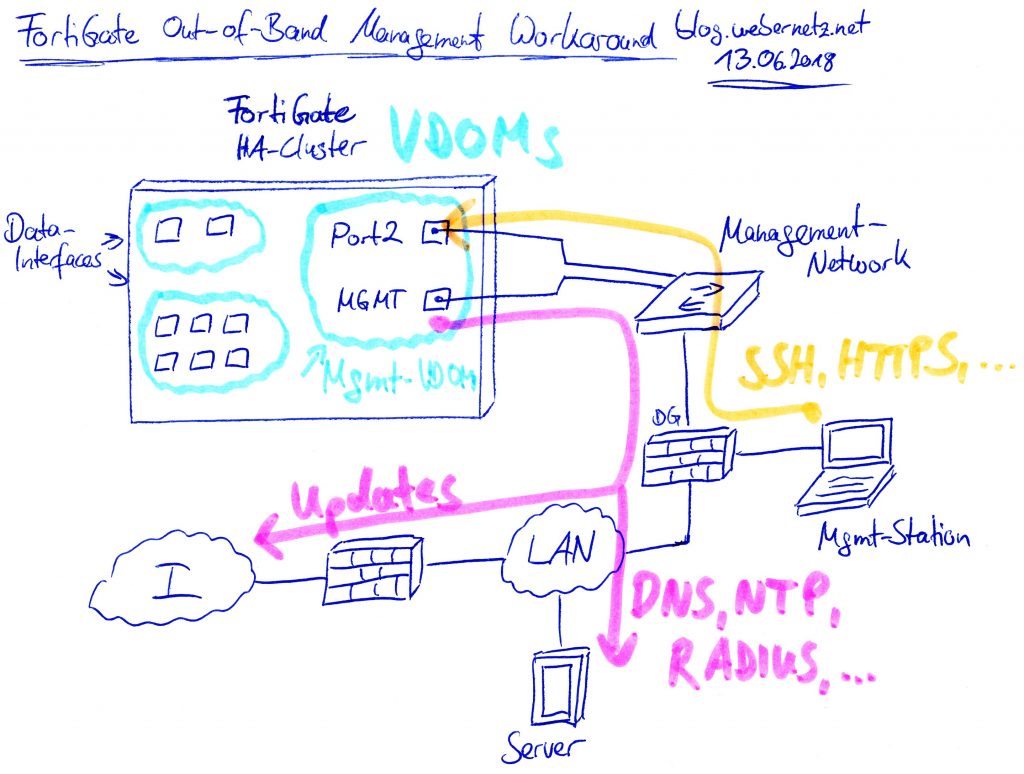
A functional workaround is to add another VDOM solely for management. From this VDOM, all management traffic is sourced. To have access to all firewalls in a high availability environment, a second (!) interface within this management VDOM is necessary. Here we go:
Note that there are other firewalls that implement that kind of OoB management such as the firewalls from Palo Alto Networks with their real dedicated management plane with its own interface and default route. This is a really good example of a clearly separated management and data plane. Don’t know why Fortinet isn’t able to do it the same way.
Workaround
The following workaround is for having a separated management VDOM that completely isolates all management traffic from the data interfaces. A picture is worth a thousand words:
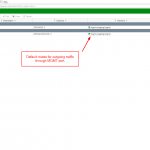
- Enable virtual domains and create another VDOM for your management. I called it “mgmt-vdom-x” just to have it distinguishable.
- Select this VDOM as your management VDOM, e.g., by clicking the “Switch Management” button in the GUI at Global -> System -> VDOM.
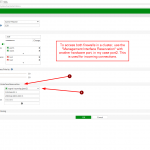
- Move the MGMT port to this management-VDOM and select “Dedicated Management Port” (just for fun, you don’t need it here). Configure static default routes for both Internet protocols. From now on, all outgoing connections from the FortiGate are sourced from this interface. Good so far.
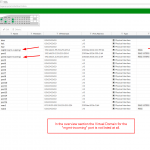
- If you want to access both firewalls in an HA environment independently you cannot use this MGMT port for incoming connections (SSH/HTTPS/…). What a shit. Hence:
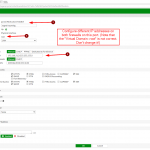
- Move a second port to this management-VDOM and within the HA section select it as “Management Interface Reservation” with appropriate route statements. I used “port2” for this.
- Configure different IP addresses (within the same prefix/subnet) on that second port on all involved firewalls.
To sum it up:
- The MGMT port is now used by the firewall for outgoing connections.
- The second port with different IP addresses on all firewalls is used by the admins to connect to those firewalls via SSH/HTTPS/SNMP.
Guide
To get an idea I have a couple of screenshots and listings for you. As always, it is crappy to configure FortiGate firewalls because the GUI does not show everything (such as IPv6 related configs) while the CLI is completely crowded with unused commands. I am using a FG-100D with FortiOS v5.6.4 build1575 (GA). My prefix/subnet for the management VDOM is 2003:de:2016:331::/64 and
192.168.31.0/24. The internal default router (not on the FortiGate but in the upstreaming data center) has the ::1 and .1 IP addresses.
And here are those code snippets from the CLI. Note that port2 has the set vdom "root" command shown, which seems to be the way FortiGate handles the port that is used for “Management Interface Reservation” in the HA section.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 |
config global config system interface edit "mgmt" set vdom "mgmt-vdom-x" set ip 192.168.31.99 255.255.255.0 set allowaccess ping set type physical set dedicated-to management set alias "mgmt-outgoing" set role lan set snmp-index 6 config ipv6 set ip6-address 2003:de:2016:331::99/64 set ip6-allowaccess ping end set trust-ip-1 192.168.0.0 255.255.0.0 set trust-ip6-1 2003:de:2016::/48 next edit "port2" set vdom "root" set ip 192.168.31.2 255.255.255.0 set allowaccess ping https ssh snmp set type physical set alias "mgmt-incoming" set role lan set snmp-index 24 config ipv6 set ip6-address 2003:de:2016:331::2/64 set ip6-allowaccess ping https ssh snmp end next end config system global set management-vdom "mgmt-vdom-x" end config system ha set group-name "asdf" set mode a-p set password ENC 8GWuqnIdx7kLSgMaTdRerkMzOy359WwZEPiPaf9U7yzpxi6P0eDStIfX+tNgeclE+Wf+X6mj4k7o/Mofi3Ta1B/j9TKRQ1rUCq7ABTYAnCpLK6LVzhQMXOH9EPPnKzuwYR9PrbMpyp2x25aqW3JQaFu2rm6GK/QVZzMzcV0acpgmTFAvsyWdazQcCrQM8FGBiSyuxA== set session-pickup enable set ha-mgmt-status enable config ha-mgmt-interfaces edit 1 set interface "port2" set gateway 192.168.31.1 set gateway6 2003:de:2016:331::1 next end set override disable set monitor "port1" "wan1" end end config vdom edit mgmt-vdom-x config router static edit 1 set gateway 192.168.31.1 set device "mgmt" next end config router static6 edit 1 set gateway 2003:de:2016:331::1 set device "mgmt" next end end |
That’s it. Working but ugly. Hopefully, Fortinet will move to real out-of-band management such as Palo Alto Networks one day…
Featured image “US-Prozess zu Abgas-Skandal: VW-Manager legt Geständnis ab” by Marco Verch is licensed under CC BY 2.0.


hello Johannes,
Your information is very helpful.
and you can use this option for HA enviroment.
ha-direct or standalone vdom as below
https://kb.fortinet.com/kb/documentLink.do?externalID=FD34744
I use them sometime depends on customer requirement.
but you may have new bugs with them haha…
Use the vdom root for management and use other vdom for traffic (data plane)
That’s a very interesting article. Fortigate is really pain when it comes to dedicated management. Also there is not much precise and/or understandable documentation. The best I could find was someone trying to explain what he found out in Fortinet forums: https://forum.fortinet.com/tm.aspx?m=157203
Hi, guys,
I am using the Forti600E with FortiOS v6.4.4, my configuration and problem is below:
https://forum.fortinet.com/tm.aspx?tree=true&m=193782&mpage=1
any advice and recommendation, many thanks
I’ve accomplished this in a data center by putting an extra firewall in the rack into which all FortiGate and FortiSwitch mgt ports are connected. VPN to that “side door” firewall and you’ve got direct access to all devices for out of band management.
Hello Johannes,
Thank you for the great article.
In the description you are pointing out the following: ‘Move the second port (port2) to this management-VDOM (mgmt-vdom-x)’. But in the Config the port2 is assigned to vdom root. I think correctly can stay the port2 in root vdom or it should be really moved to mgmt-vdom-x?
edit “port2”
set vdom “root”
Thanks :)
Hey paulzir. Yes, that looks weird. I don’t have this setup working right now anymore, so I can’t look it up. However, just before the CLI section above, I wrote the following sentence: “Note that port2 has the set vdom “root” command shown, which seems to be the way FortiGate handles the port that is used for “Management Interface Reservation” in the HA section.” –> Hence I believe that I was aware of this misleading configuration command.
Have you tried that configuration? Which with vdom config is it working?
What it is happening is that when you set a port as “dedicated-to-management” in HA configuration. This port is assigned to a hidden VDOM named “vsys_hamgmt”…
You can enter this VDOM with command: #execute enter vsys_hamgmt
Hi Johannes
I’m confused by your statements above that say:
“Their so-called “MGMT” port is …etc,etc…….but is not able to source outgoing traffic by default”
but then you say
“The MGMT port is now used by the firewall for outgoing connections.”
Also, has the situation you have described now been fixed? This article appears to suggest the dedicated MGMT interface can be used for inbound/outbound monitoring and connectivity to the Internet:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Using-dedicated-management-interface-for/ta-p/228972
Hi,
Greate explanation. i have two questions:
1. Can we use the MGMT Port as a HA-reserved management ?
2. If there is not VDOMS, can we use the MGMT Port for all the traffic and for the https and ssh access ?
Hey ashraf,
1) AFAIK this is NOT possible. I think this is exactly the point why I had to use two different ports on this proposed design here. (But maybe I’m wrong? Have you tried it by yourself in the meantime?) I’m talking to a Fortinet SE right now. He’s not sure either. Please give it a try. ;D
2) Yes. The MGMT port is independent of VDOMs. If you set the “dedicated management port”, you can’t use this port for data traffic anymore though (recommended). Does this answer your question? (I’m not quite sure whether I got it right.)