When implementing new firewalls at the customers’ site it is always interesting to verify that the anti-virus scanners etc. are running as expected. For simple virus-engines, a sample virus such as the EICAR anti-malware test file can be used. If this “virus” traverses through the firewall inside various protocols such as http, ftp, or smtp, the firewall must block this connection.
However, next-generation firewalls or any other APT (Advanced Persistent Threat) solutions are able to send unknown executables to its own cloud in order to test it. If a malware is found, these products can block future connections with these files, e.g., by updating the anti-virus patterns or their URL categories.
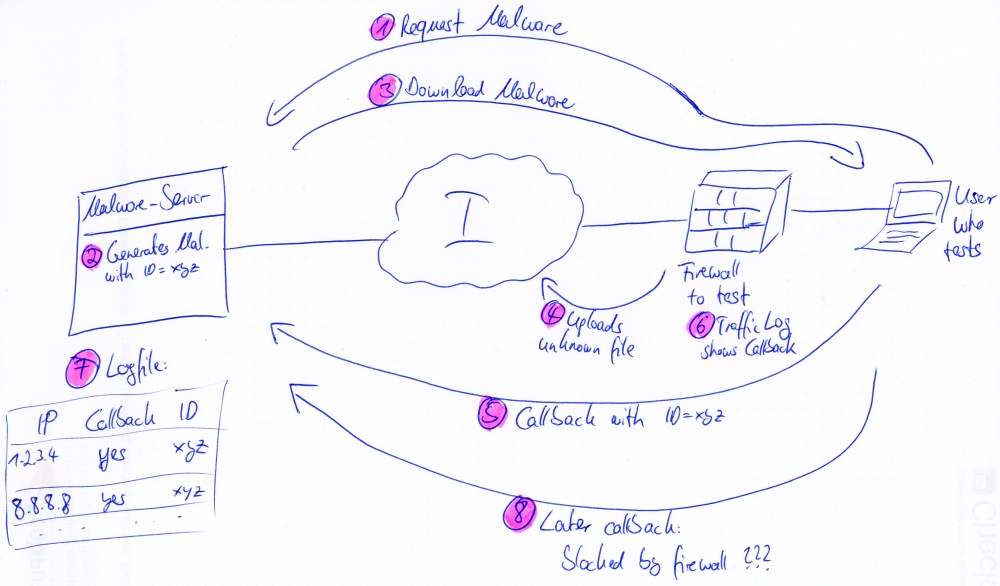
The problem is: How to test whether the “upload unknown files” function works properly? -> My idea is to have a server that generates “dynamic” viruses. When downloading such a “fresh generated” virus, the antivirus engine does not have a pattern for it. That is, the file must be uploaded to an APT solution. The logs on the firewall should list this upload process.
Dynamic Malware
This could be the process:
- A user requests a “new” virus from a known and trusted server that runs this application. The virus should not harm the test system, but should behave as a virus.
- The server must modify the source code of the virus each time in order to pass common antivirus patterns.
- The user downloads the virus through a common protocol such as http, ftp, or gets the virus by mail (smtp).
- The NGFW should detect an unknown file (= no antivirus pattern) and upload it to its own cloud based APT engine.
Here is a quick-and-dirty sketch:
To my mind, it is not easy to generate “fresh malware”. But since the bad guys are doing it all the time, it should be feasible.
I do not know whether such a system is already present on the Internet. Maybe? If someone knows something about such systems, please write a comment. Or this might be a good topic for a project thesis for students. ;)
Even with Callbacks?
An even more interesting test case would be a “malware server” that generates dynamic malwares with a callback to itself. A logfile on the server would reveal whether the test malware really called back. That is, a user could test whether an APT solution a) recognizes and b) prevents callbacks. The scenario could be similar to the above one:
- The user requests a new malware from the server.
- The server generates a fresh malware with a random callback ID.
- The user downloads the malware.
- The APT solution gathers information about this malware.
- The test PC calls back to the “malware server”.
- Any firewalls should see the connection to the server. After pattern updates of the antivirus engines, these callbacks should be blocked.
- A logfile on the server, which shows the callback ID from step 2 as a reference, reveals which machines successfully called back.
- A callback from another PC that is initiated later on should be blocked by the firewall/APT solution.
And a sketch for this process, too:
Okay, maybe this idea is a bit oversized. However, I think a method to show the customer that his machines are working as expected would be great.
Featured image “365 – 263” by Dave Edens is licensed under CC BY-NC 2.0.




I like the idea but I guess that this isn’t a useful way. As a customer I need to see that the system is able to identify “real-world”-malware. And there are already some ressources where you can download your fresh malware :)
And additionally. If you have some kind of callback-mechanism for testing your server would be added to a blacklist very fast and hence you wouldn’t be able to test anything more with this server.
Very interesting idea!
I’ll discuss that with our IT security auditor – maybe these guys do have some ideas of implementig such a usefull service.