Since PAN-OS version 6.1 the Palo Alto Networks firewall supports LACP, the Link Aggregation Control Protocol which bundles physical links to a logical channel. Palo Alto calls it “Aggregate Interface Group” while Cisco calls it EtherChannel or Channel Group. I configured LACP for two ports connected from a Palo Alto firewall to a Cisco switch. Following are the configuration steps for both devices as well as some show commands.
Some pre-notes:
- I am using LACP in conjunction with LLDP to detect the physical neighbours. This is NOT mandatory for LACP to work. I am using it for practising and for seeing potential differences on the Palo and Cisco sides. (Refer to my last post in which I covered LLDP on the Palo in more detail.)
- To see how LACP looks on the wire, download my big pcap file here and filter for it.
- This lab consists of a Palo Alto PA-3020 cluster with PAN-OS 8.0.1 and two
- Cisco C3750 switches with IOS version Version 12.2(50)SE3.
- I configured the channel in the following way (fiber ports):
- Palo: ae1 = ethernet1/17 & ethernet1/18
- Cisco: po1 = Gi1/0/1 & Gi1/0/2
- Never forget that all physical interfaces MUST share the same parameters, such as speed & duplex, VLANs, etc.
Let’s go:
Configuration Palo & Cisco
The configuration for the Palo Alto firewall is done through the GUI as always. It consists of the following steps:
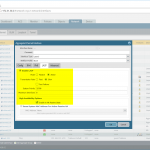
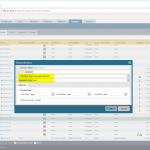
- Adding an Aggregate Group and enabling LACP. The mode decides whether to form a logical link in an active or passive way. (If both sides are passive, it won’t work. At least one side must be active.) The transmission rate must be slow in order to match the one from the Cisco switch. (Only the bigger Cisco switches such as Nexus support the fast rate.) Tick the checkmark for the “Enable in HA Passive State” to have a faster convergence time in cluster environments.
- [Optional] Configure subinterfaces within the aggregate group.
- Edit the physical Ethernet interfaces to be an “Aggregate Ethernet” interface type and select the appropriate group.
Here are the corresponding screenshots:
The configuration of the Cisco switch is quite simple. Just add the channel-group command on all relevant physical interfaces. However, don’t forget to have the same interface settings on all ports. Use the interface range <port-range> command to configure more than one interface at a time. These are the final settings I used for both physical ports as well as for the port-channel:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
interface GigabitEthernet1/0/1 switchport trunk encapsulation dot1q switchport trunk allowed vlan 123 switchport mode trunk channel-group 1 mode active ! interface GigabitEthernet1/0/2 switchport trunk encapsulation dot1q switchport trunk allowed vlan 123 switchport mode trunk channel-group 1 mode active ! interface Port-channel1 switchport trunk encapsulation dot1q switchport trunk allowed vlan 123 switchport mode trunk |
Let the Show begin
Following are the show commands from the Palo Alto firewall for LACP and LLDP. Note that for the latter the “ae1” interface simply lists both physical ports:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 |
admin@PA-1(active)> show lacp aggregate-ethernet ae1 LACP: ********************************************************************************** AE group: ae1 Members: Bndl Rx state Mux state Sel state ethernet1/17 yes Current Tx_Rx Selected ethernet1/18 yes Current Tx_Rx Selected Status: Enabled Mode: Active Rate: Slow Max-port: 8 Fast-failover: Disabled Pre-negotiation: Enabled Local: System Priority: 32768 System MAC: 58:49:3b:2f:f9:01 Key: 48 Partner: System Priority: 32768 System MAC: 08:17:35:08:17:35 Key: 1 Port State -------------------------------------------------------------------------------- Interface Port Number Priority Mode Rate Key State -------------------------------------------------------------------------------- ethernet1/17 32 32768 Active Slow 48 0x3D Partner 258 32768 Active Slow 1 0x3D ethernet1/18 33 32768 Active Slow 48 0x3D Partner 259 32768 Active Slow 1 0x3D Port Counters -------------------------------------------------------------------------------- Interface LACPDUs Marker Marker Response Error Sent Recv Sent Recv Sent Recv Unknown Illegal -------------------------------------------------------------------------------- ethernet1/17 779 840 0 0 0 0 0 0 ethernet1/18 779 840 0 0 0 0 0 0 admin@PA-1(active)> admin@PA-1(active)> admin@PA-1(active)> admin@PA-1(active)> show lldp neighbors ae1 Local information: Index 32 Local interface: ethernet1/17 Local Port ID: 17 Neighbor information: Chassis type: MAC address Chassis ID: 08:17:35:08:17:35 Port type: Interface name Port ID: Gi1/0/1 Port description: GigabitEthernet1/0/1 TTL: 90 System name: PA-TESTSW01.pa-lab.local System description: Cisco IOS Software, C3750 Software (C3750-IPBASEK9-M), Version 12.2(50)SE3, RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2009 by Cisco Systems, Inc. Compiled Wed 22-Jul-09 06:19 by prod_rel_team System capabilities: Supported: B, R, Enabled: B, Management address type: ipv4 Management address: 172.31.10.5 Interface number: 10 Interface type: Ifindex oid: Local information: Index 33 Local interface: ethernet1/18 Local Port ID: 18 Neighbor information: Chassis type: MAC address Chassis ID: 08:17:35:08:17:35 Port type: Interface name Port ID: Gi1/0/2 Port description: GigabitEthernet1/0/2 TTL: 98 System name: PA-TESTSW01.pa-lab.local System description: Cisco IOS Software, C3750 Software (C3750-IPBASEK9-M), Version 12.2(50)SE3, RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2009 by Cisco Systems, Inc. Compiled Wed 22-Jul-09 06:19 by prod_rel_team System capabilities: Supported: B, R, Enabled: B, Management address type: ipv4 Management address: 172.31.10.5 Interface number: 10 Interface type: Ifindex oid: admin@PA-1(active)> |
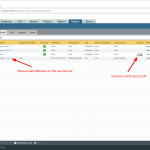
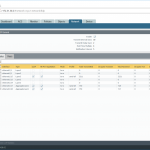
The status and peers of LLDP can also be viewed from the GUI. Note that I have three ports connected to the same switch, hence it appears three times as well:
And here are the show commands from the Cisco switch, LACP and LLDP as well:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 |
PA-TESTSW01#show etherchannel summary Flags: D - down P - bundled in port-channel I - stand-alone s - suspended H - Hot-standby (LACP only) R - Layer3 S - Layer2 U - in use f - failed to allocate aggregator M - not in use, minimum links not met u - unsuitable for bundling w - waiting to be aggregated d - default port Number of channel-groups in use: 1 Number of aggregators: 1 Group Port-channel Protocol Ports ------+-------------+-----------+----------------------------------------------- 1 Po1(SU) LACP Gi1/0/1(P) Gi1/0/2(P) PA-TESTSW01# PA-TESTSW01# PA-TESTSW01#show etherchannel 1 detail Group state = L2 Ports: 2 Maxports = 16 Port-channels: 1 Max Port-channels = 16 Protocol: LACP Minimum Links: 0 Ports in the group: ------------------- Port: Gi1/0/1 ------------ Port state = Up Mstr Assoc In-Bndl Channel group = 1 Mode = Active Gcchange = - Port-channel = Po1 GC = - Pseudo port-channel = Po1 Port index = 0 Load = 0x00 Protocol = LACP Flags: S - Device is sending Slow LACPDUs F - Device is sending fast LACPDUs. A - Device is in active mode. P - Device is in passive mode. Local information: LACP port Admin Oper Port Port Port Flags State Priority Key Key Number State Gi1/0/1 SA bndl 32768 0x1 0x1 0x102 0x3D Partner's information: LACP port Admin Oper Port Port Port Flags Priority Dev ID Age key Key Number State Gi1/0/1 SA 32768 5849.3b2f.f901 4s 0x0 0x30 0x20 0x3D Age of the port in the current state: 0d:06h:35m:30s Port: Gi1/0/2 ------------ Port state = Up Mstr Assoc In-Bndl Channel group = 1 Mode = Active Gcchange = - Port-channel = Po1 GC = - Pseudo port-channel = Po1 Port index = 0 Load = 0x00 Protocol = LACP Flags: S - Device is sending Slow LACPDUs F - Device is sending fast LACPDUs. A - Device is in active mode. P - Device is in passive mode. Local information: LACP port Admin Oper Port Port Port Flags State Priority Key Key Number State Gi1/0/2 SA bndl 32768 0x1 0x1 0x103 0x3D Partner's information: LACP port Admin Oper Port Port Port Flags Priority Dev ID Age key Key Number State Gi1/0/2 SA 32768 5849.3b2f.f901 28s 0x0 0x30 0x21 0x3D Age of the port in the current state: 0d:06h:35m:24s Port-channels in the group: --------------------------- Port-channel: Po1 (Primary Aggregator) ------------ Age of the Port-channel = 0d:06h:44m:16s Logical slot/port = 10/1 Number of ports = 2 HotStandBy port = null Port state = Port-channel Ag-Inuse Protocol = LACP Port security = Disabled Ports in the Port-channel: Index Load Port EC state No of bits ------+------+------+------------------+----------- 0 00 Gi1/0/1 Active 0 0 00 Gi1/0/2 Active 0 Time since last port bundled: 0d:06h:35m:24s Gi1/0/2 PA-TESTSW01# PA-TESTSW01# PA-TESTSW01#show lldp neighbors Capability codes: (R) Router, (B) Bridge, (T) Telephone, (C) DOCSIS Cable Device (W) WLAN Access Point, (P) Repeater, (S) Station, (O) Other Device ID Local Intf Hold-time Capability Port ID PA-TESTSW02 Gi1/0/4 120 B Gi1/0/4 PA-1 Gi1/0/2 120 O,R ethernet1/18 PA-1 Gi1/0/3 120 O,R ethernet1/15 PA-1 Gi1/0/1 120 O,R ethernet1/17 Total entries displayed: 4 PA-TESTSW01# PA-TESTSW01# PA-TESTSW01#show lldp neighbors gi1/0/1 detail ------------------------------------------------ Chassis id: 001b.17eb.830c Port id: ethernet1/17 Port Description - not advertised System Name: PA-1 System Description: Palo Alto Networks PA-3000 series firewall Time remaining: 107 seconds System Capabilities: O,P,B,R Enabled Capabilities: O,R Management Addresses - not advertised Auto Negotiation - not supported Physical media capabilities - not advertised Media Attachment Unit type - not advertised Vlan ID: - not advertised Total entries displayed: 1 PA-TESTSW01# PA-TESTSW01# PA-TESTSW01#show lldp neighbors gi1/0/2 detail ------------------------------------------------ Chassis id: 001b.17eb.830c Port id: ethernet1/18 Port Description - not advertised System Name: PA-1 System Description: Palo Alto Networks PA-3000 series firewall Time remaining: 108 seconds System Capabilities: O,P,B,R Enabled Capabilities: O,R Management Addresses - not advertised Auto Negotiation - not supported Physical media capabilities - not advertised Media Attachment Unit type - not advertised Vlan ID: - not advertised Total entries displayed: 1 PA-TESTSW01# PA-TESTSW01# |
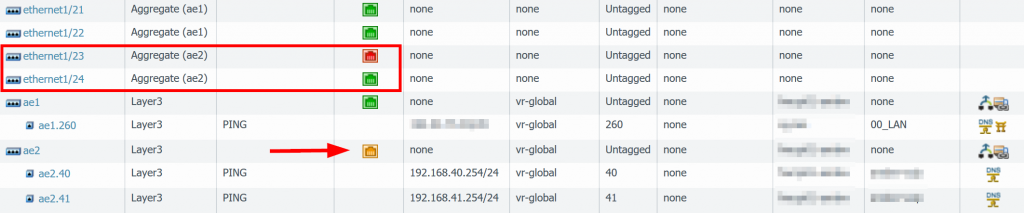
One more screenshot from another Palo Alto firewall, in which one of two ports was down, hence the AE port turned yellow:
Links
- Podcast Heavy Networking 690: LACP Is Not Link Aggregation
- Palo Alto Live Community – How to Configure LACP
- Cisco Systems – Link Aggregation Control Protocol (LACP) (802.3ad) for Gigabit Interfaces
- Wikipedia – Link Aggregation Control Protocol
Featured image: “Langzeitbelichtung Autobahn” by Pette Photography is licensed under CC BY-NC-ND 2.0.


![[Optional] Enable LLDP.](https://weberblog.net/wp-content/uploads/2017/05/Palo-Alto-LACP-2-with-LLDP-150x150.png)

Was working on this today with a Cisco 3750X stack running software 15.0(2)SE10a. You are correct that it only supports slow LACP timers, however upgrading to 15.2(4) apparently does support fast ones. Anyway I got different failover times on depending on who was active vs. passive:
Cisco Passive, Palo Alto Active: 25-30 seconds
Cisco Active, Palo Alto Passive: 12-15 seconds
Also worth noting that since the Palo Alto disables interfaces when the device is standby, it helps immensely to have the Port-Channel in Spanning-Tree Edge mode aka Portfast, since going through the blocking and learning states will add another 25 seconds.
Hi John,
thanks for your comment. Have you tested to change the “Palo Alto disables interfaces when the device is standby” option? Have a look at the HA settings on both devices. The “Passive Link State: shutdown” is default, but you can set it to “auto” which leaves them up. This should accelerate your HA times.
Hello,
I am setting up a pair of Palo Alto 3260 in Ha mode active/passive to a pair of Cisco Catalyst in stack.
I have configured a pair of interfaces in lacp in the Palo Alto, so one pair of interfaces on the Active unit and one pair of interfaces on the standby unit.
On the cisco switch, i have xonfigured two etherchannels one for one palo alto unit.
It is working but i was wondering if it is the right approach. From the switch perspective, the palo alto are two diferent devices. Can you please confirm if my approach is good?
Furthermore, the same Palo Alto units have another lacp pair to the same switch, the outside interface of the palo alto. Is this configuration for palo alto possible with 2 lacp group to the same switch lacp neighbor id being the same ?
Hey Ashley,
it depends. ;) Your approach seems to be ok. This is quite normal. You have an LACP channel from the active Palo to a switch and an own LACP channel from the passive Palo to another switch. If the firewall HA state changes, the other switch gets/sends traffic to/from the Palo. Yes, from the switches point of view, they are connected to different devices. But that’s ok. You can set the “Enable in HA Passive State” option for LACP so that the passive Palo already talks LACP to the switch.
Palo with two LACPs channels to the same switch: no problem as long as you’re using different port-channel groups on the Cisco switch. And, of course, select the appropriate VLANs.
Hello!
Thanks for this tutorial.
Could you describe the settings for LLDP profile (named “send-all”) and Cisco side? (example: “lldp run”)
Regards
Sim
Hey Sim,
yes, sorry, I did not explain it in detail in this post.
Plese refer to my other blogpost about LLDP: https://weberblog.net/palo-alto-lldp-neighbors/
Cheers,
Johannes
Hi Johannes,
today I spent time configuring HA of our new 5220 devices.
During testing I came across a few issues. First of all I tested without “Enable in HA Passive State” and the failover took about 50 seconds to work. Of course this is unacceptable in particular if you compare this result with our current setup without LACP where the failover time is below 1 sec.
After that there was still a delay of 20 seconds because of Spanning Tree. After configuring edge ports (spanning-tree porfast trunk) on Cisco side the failover took roughly 2 seconds. Still to much.
Tomorrow I try to do more tests with different modes and transmission rates.
Do you use mode active on both sides?
Kind regards
Tobias
I could finally tweak the failover time under 1 second. The key was to set Palo Alto LACP mode on passive and on Cisco side on active. Moreover “lacp rate fast” on Cisco is necessary.
Hi Tobi,
thanks a lot for your input. To be honest: I have not tried failover times to under 1 second. Hence no advice from me here. ;(
(And since I used it only with non-Nexus Cisco switches, “LACP fast rate” was not available anyway.)
Hi johan,
I configured my PA 5060 port 23 and 24 as abundle,however port 24 is down. Tried on nother firewall the same how to verify this
Hey Walt. I don’t have a concrete hint for you, but only some general advices on how to troubleshoot such issues:
– Try port 24 without a bundle
– SFP problems? Have a look at my CLI commands, search for SFP: https://weberblog.net/cli-commands-for-troubleshooting-palo-alto-firewalls/
– Cabling error? Have a look at the interface counters
– LACP timing errors?
Cheers, Johannes
Hi Johannes,
What’s the difference between the L2 and L3 aggregation on Palo Alto?
Can we use – spanning-tree portfast on the Cisco side, while having L2 or L3 aggregation?
Thank you,
Hey Supun,
your question about “difference between L2 and L3 on Palo Alto” is independent of aggregation. While I am normally recommending L3 in any case (with or without aggregation), you can use L2 as well (with or without aggregation), if your scenario requires it. Yes, you can use “spanning-tree portfast” on the Cisco side in both scenarios, but please be careful when designing your network.
Basically: A L3 interface is like a “routed interface” on a Cisco router or on a Cisco L3-Switch with “no switchport”, while a L2 interface behaves like a normal switch port on any Cisco switch. That is: Somewhere you need a VLAN interface (L3) to have routing functionality. Either on the Cisco switch or on the Palo.
But again: This depends on your network design. You can do both with either Cisco and Palo.
Couple of years ago I wrote something about L2 interfaces on Palo with Cisco: https://weberblog.net/layer-2-redundancy-with-stp-palo-alto-firewall-cisco-switches/
I used this template to get a new PA-400 working to a pair of old 2960X switches. The switches have an etherchannel between them for layer-2 vlans and such, but the firewall I want to run in layer-3. Since the switches cannot do stacking, I’m left with alternate methods.
What I did is create an AE group on the Palo and put one interface into each switch. A port channel was created on the switches (with 1 member). In the AE’s LACP tab, I set the maximum number of ports to 1. That means only one switch port is active at a time. (All other traffic can travel between switches to get there). The Palo puts the other interface in LACP standby jail.
All this works great, however, which port is active (cisco or palo) is almost random. It’s whichever port was up first. Changing LACP port priorities on either side makes no difference.
Do you know of a way on the switch or firewall to do preemptive switch back? I can’t find the magic bullet to make my switch 1 always the active one to the Palo, when possible.
Hi Robert.
Uh, good question. But I don’t have an answer – I’m sorry. You are stacking those two 2960X switches and using the Etherchannel as a VPC, correct?
(I don’t see a reason for using only one of these ports other than a feeling, right? ;))
No VPC in the Nexus sense. Each switch only sees one port. Maybe it will work. I’ll play with it more. thanks
what about the MAC setup after we enable HA Passive State under LACP for the aggregate interface?
We’re setting up active-passive in HA; in setting up the new firewalls; I’d like to create Port-Channel group from our Cisco 4331and to our PA1420 using LACP.
Is this possible on the PA in HA?
PA-Active (Port 3) === (ae1)====——portchannel ge 0/1/1 interface——Cisco 4331
PA-Passive (Port 3)===(ae1) ====——portchannel ge0/1/2 interface——Cisco 4331
Hey Shawn. I’m quite sure that this is NOT possible. This is not how it’s supposed to work. If you want to use a port channel for port redundancy or bandwidth aggregation, you MUST use one port channel per firewall. That is:
PA-active (port 3 & 4 for example) === ae1 === ge0/1/1-ge0/1/2
PA-passive (port 3 & 4 again) === ae2 === ge0/1/3-ge0/1/4
That is: The Palos are really active OR passive. You cannot split one ae in half. I even think that this won’t work with LACP, because the “system ID” which is sent from the Palos is different, since those are two different devices. Hence the Cisco switch won’t accept this single port aggregation.
Your design is not safe and sound anyway since your switch will be a single point of failure. If you want a high availability setup, you MUST have 2x of your Cisco switch anyway.
(Sorry for the late reply, by the way.)
Cheers
Johannes