For some reason, I am currently using a FortiGate on a location that has no native IPv6 support. Uh, I don’t want to talk about that. ;) However, at least the FortiGate firewalls are capable of 6in4 tunnels. Hence I am using the IPv6 Tunnel Broker from Hurricane Electric again. Quite easy so far.
But note, as always: Though FortiGate supports these IPv6 features such as a 6in4 tunnel or stateful/-less DHCPv6 server, those features are NOT stable or well designed at all. I had many bugs and outages during my last years. Having “NAT enabled” on every new IPv6 policy is ridiculous. Furthermore, having independent security policies for legacy IP and IPv6 is obviously a really bad design. One single policy responsible for both Internet protocols is a MUST. Anyway, let’s look at the 6in4 tunnel:
Configuring this IPv6-in-IPv4 tunnel is quite easy since HE itself offers the configuration:
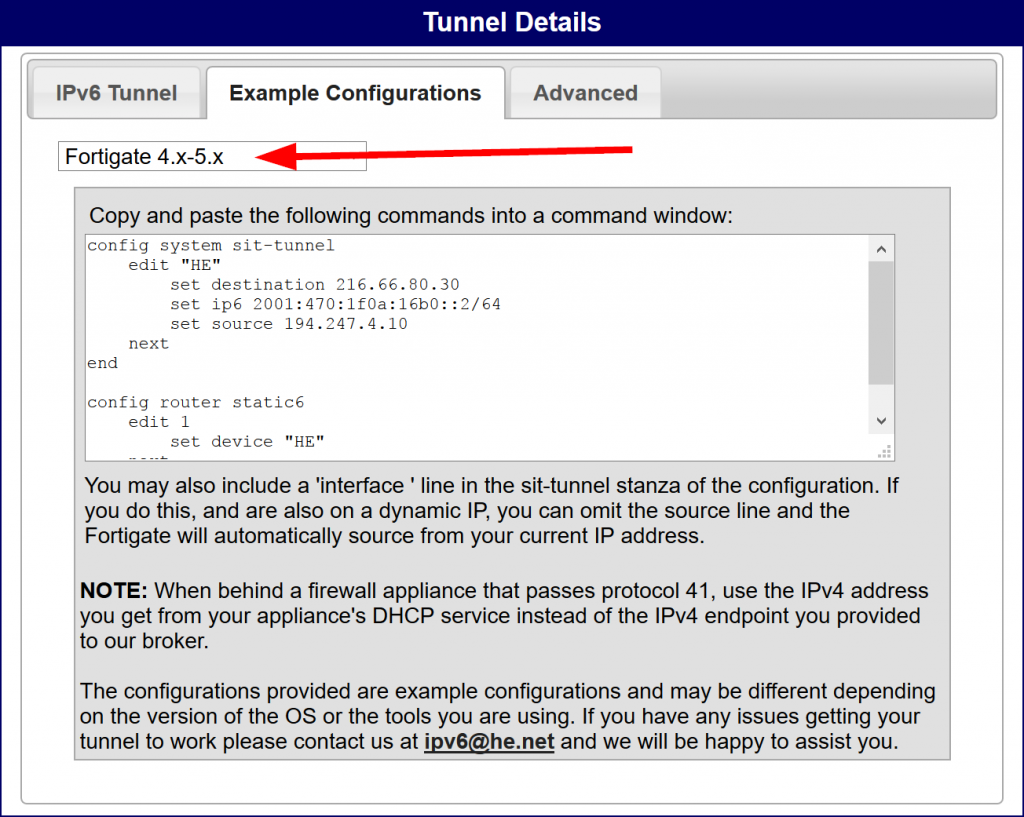
Of course, you need an internal layer 3 interface as well. That is, a complete configuration (6in4 tunnel, default route, inside interface with RDNSS) looks like that:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 |
config system sit-tunnel edit "HE" set destination 216.66.80.30 set ip6 2001:470:1f0a:16b0::2/64 set source 194.247.4.10 next end config router static6 edit 1 set device "HE" next end config system interface edit "internal" config ipv6 set ip6-address 2001:470:1f0b:16b0::1/64 set ip6-allowaccess ping https ssh set ip6-send-adv enable config ip6-prefix-list edit 2001:470:1f0b:16b0::/64 set autonomous-flag enable set onlink-flag enable set rdnss 2620:fe::fe set dnssl "weberlab.de" next end end next end |
Finally, you need some IPv6 policy entries to permit traffic. Again, note that you MUST NOT select the NAT, which is stupidly pre-selected by Fortinet:
On every new IPv6 policy on a @Fortinet FortiGate firewall the default selection is "NAT". #fail #IPv6 pic.twitter.com/BfS4qKEfc6
— Johannes Weber ? (@webernetz) March 1, 2017
Stumbling Blocks
I am using a FortiGate FG-90D with FortiOS 5.6.8 build1672 (GA).
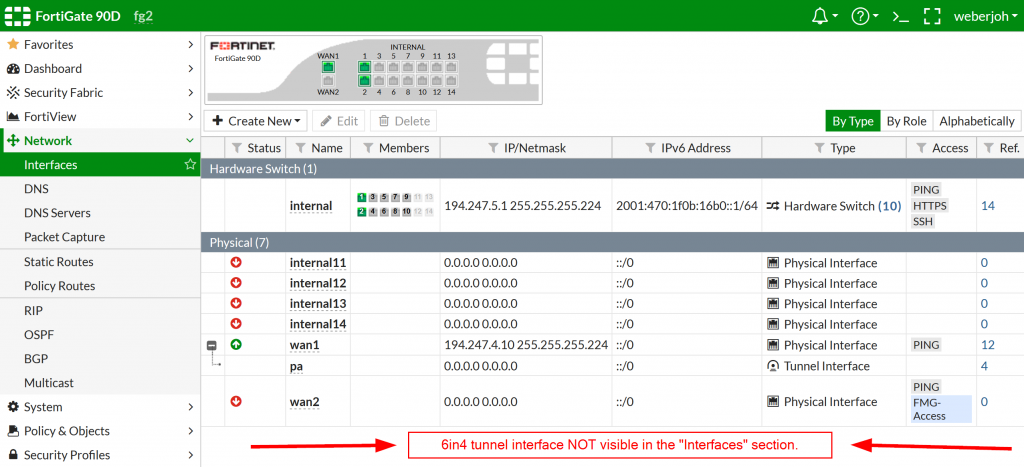
Note that this “HE” interface, as it is named in the example configuration above, is NOT visible in the interface section in the GUI:
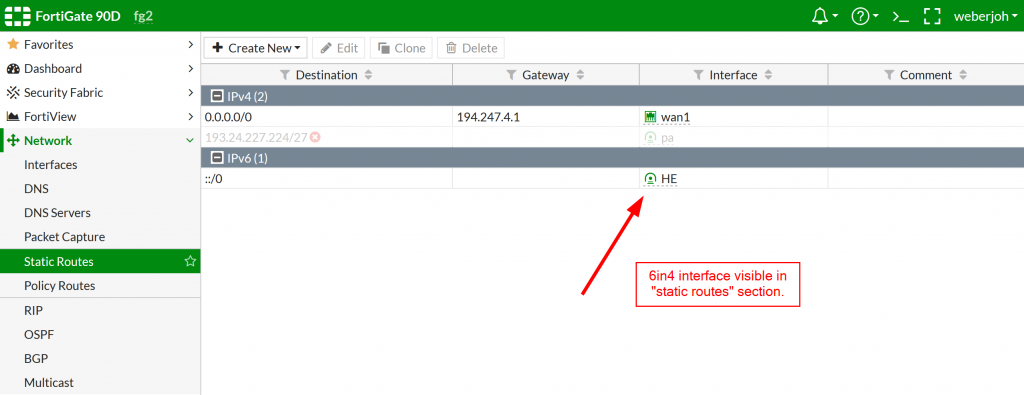
while it IS visible in the routing section:
Honestly: Who is approving such decisions at Fortinet? This is not sound at all, isn’t it?
Verifying
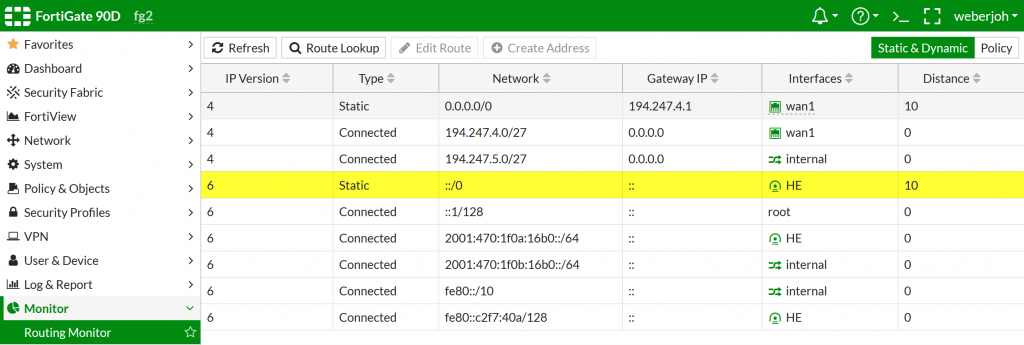
You can have a look at the routing monitor to see the default route in place:
Some CLI commands are as follows. Getting information about the tunnel interface you can use this kind of hidden command: fnsysctl ifconfig such as:
|
1 2 3 4 5 6 7 8 9 |
fg2 # fnsysctl ifconfig HE HE Link encap:Unknown HWaddr C2:F7:04:0A:00:00 inet addr6: 2001:470:1f0a:16b0::2 prefixlen 64 link-local6: fe80::c2f7:40a prefixlen 128 UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1480 Metric:1 RX packets:664858 errors:0 dropped:0 overruns:0 frame:0 TX packets:1015185 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:179754139 (171.4 MB) TX bytes:114587175 (109.3 MB) |
IPv6 routing table:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
fg2 # get router info6 routing-table IPv6 Routing Table Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 I - IS-IS, B - BGP * - candidate default Timers: Uptime S* ::/0 [10/0] via ::, HE, 01w2d12h C ::1/128 via ::, root, 04w2d19h C 2001:470:1f0a:16b0::/64 via ::, HE, 01w2d12h C 2001:470:1f0b:16b0::/64 via ::, internal, 01w2d11h C fe80::/10 via ::, internal, 01w2d11h C fe80::c2f7:40a/128 via ::, HE, 01w2d12h |
And some basic network connectivity test, aka ping:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
fg2 # execute ping6-options reset fg2 # execute ping6 weberblog.net PING weberblog.net(2a01:488:42:1000:50ed:8588:8a:c570) 56 data bytes 64 bytes from 2a01:488:42:1000:50ed:8588:8a:c570: icmp_seq=1 ttl=56 time=9.13 ms 64 bytes from 2a01:488:42:1000:50ed:8588:8a:c570: icmp_seq=2 ttl=56 time=11.4 ms 64 bytes from 2a01:488:42:1000:50ed:8588:8a:c570: icmp_seq=3 ttl=56 time=9.57 ms 64 bytes from 2a01:488:42:1000:50ed:8588:8a:c570: icmp_seq=4 ttl=56 time=10.3 ms 64 bytes from 2a01:488:42:1000:50ed:8588:8a:c570: icmp_seq=5 ttl=56 time=10.1 ms --- weberblog.net ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss, time 4045ms rtt min/avg/max/mdev = 9.136/10.145/11.487/0.806 ms |
That’s it. Thanks for watching. ;) Don’t forget to hit the subscribe button.
Featured image “Make It Count” by Mr. Nixter is licensed under CC BY-NC 2.0.



Hi Johannes,
also auf meiner Fortigate sehe ich in der Consolidated Policy kein NAT:
https://www.imagebanana.com/s/1476/bi5EZH7m.html
;-)
VG
Dominik
Hey Dominik.
Naja, wenn man es genau nimmt, dann ja doch. ;) Du hast halt das Zentral NAT aktiviert. Dennoch wird es bei einer IPv6 Policy eingeblendet, also der NAT Bereich. Schlimm genug. :)
I have a question about factory resetting a Fortinet. After running a the factory reset command i booted to the back up firmware and it still had a host name, password and user setup. When i logged into the backup none of the ‘execute command was not available to execute the factory reset . How would you go about resetting it.
Hi Sean.
Uh, good question. To be honest, I don’t know. I have not yet tried to boot into the backup firmware after a reset. Sorry. Please ask your question to the official Fortinet support. (It’s probably not good at all that the backup firmware still has configurations on it after a “factory reset”. To my mind, this should not be the case.)
Johannes