If you want to establish an Internet connection (that is: IPv6 and IPv4) right away from your firewall through xDSL connections, you need quite some technologies: PPPoE and PPPoEv6 (PPP IPV6CP) along with DHCPv6-PD. Fortunately, with PAN-OS 11.0 and 11.1, those missing IPv6 links were finally added by PANW to their Strata firewalls. (I have been awaiting them since 2015!)
So, here it is: Connecting a Palo through an xDSL modem to a residential ISP:
I’m using a PA-440 with PAN-OS 11.2.4-h2, connected through a DrayTek Vigor167 modem to the German ISP “Deutsche Telekom” on ethernet1/2. No VLAN config is needed since the DSL modem already encapsulates the traffic within VLAN 7 on the ISP side.
Side note: Unfortunately, we don’t have static IP addresses nor static IPv6 subnets on most German residential ISPs. Hence, after every DSL reconnect or firewall reboot, we’ll get new public IPv4/IPv6 addresses along with a new IPv6 prefix. 🤦
PPPoE for legacy IP
Quite straightforward: Layer 3 interface of type PPPoE, adding username & password:
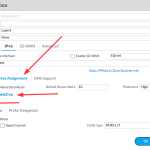
PPPoEv6 & DHCPv6-PD for IPv6
A few more options and submenus regarding IPv6. In addition, note the quite good documentation from Palo Alto Networks itself.
- Type PPPoEv6 Client, enable, and “Apply IPv4 Parameters” since the same login should be used
- followed by the address assignment that “Accept Router Advertised Route” along with the Autoconfig enabled, since, in my case, the firewall gets its WAN IPv6 address through a Router Advertisement (SLAAC) from the ISP’s router rather than through stateful DHCPv6
- still at the address assignment: enabling DHCPv6 but only with the Prefix Delegation options, giving the pool a name, in my case: DTAG. Note that the DHCP prefix length is just a hint and probably not honored by the ISP
- and finally, the DNS support, at least for the DNS resolver while the search list remains useless from the ISP
For IPv4 client networks, you can now add (sub-)interfaces with RFC 1918 addresses together with an SNAT rule using the WAN interface. For IPv6 downstream interfaces, you have to configure “Inherited” networks that are using a /64 prefix out of the proposed one from your ISP, such as shown here. No NAT is needed. ✅
Commit ;)
Client Runtime Information
Through the GUI, you can look up several runtime information such as the PPPoE and PPPoEv6 IP addresses, the DHCPv6-PD prefix, the actually assigned prefixes to downstream interfaces, the (default) routes within the forwarding table of the logical router, as well as appropriate system logs:
Some basic show commands are these: (Always remember that you can find all CLI commands concerning a keyword such as “pppoe” in the following way: find command keyword pppoe.)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 |
weberjoh@pa-home> show pppoe interface ethernet1/2 Interface: ethernet1/2 PPPoE State: Connected PPP State: Connected Connected since: Mon Dec 16 14:12:39 2024 Connection up for: 0 days, 2:28:10 Access Concentrator: FDBJ00 AC MAC: 3c:61:04:50:d2:1a Authentication via: PAP Passive mode: Disabled Username: 001234567890#098765432123#0001@t-online.de Local IP: 84.139.79.37 Primary DNS IP: 217.237.150.51 Secondary DNS IP: 217.237.148.22 Primary WINS IP: 0.0.0.0 Secondary WINS IP: 0.0.0.0 Remote IP: 62.155.246.34 Session ID: 10 Link MTU: 1492 PPPoE/PPP Counters: PPPoE control packets received: 2 PPPoE control packets sent: 2166 PPP control packets received: 2676 PPP control packets sent: 2655 weberjoh@pa-home> weberjoh@pa-home> weberjoh@pa-home> show pppoe ipv6 interface ethernet1/2 Interface: ethernet1/2 PPPoE State: Connected PPP State: Connected Connected since: Mon Dec 16 14:12:39 2024 Connection up for: 0 days, 2:28:46 Access Concentrator: FDBJ00 AC MAC: 3c:61:04:50:d2:1a Authentication via: PAP Passive mode: Disabled Username: 001234567890#098765432123#0001@t-online.de Session ID: 10 Link MTU: 1492 Client Identifier: 3e:fa:30:ff:fe:03:12:11 Server Identifier: 3e:61:04:ff:fe:50:d2:1a Address Assignment: Stateless Address Autoconfig: Enabled DHCPv6 Config: Enabled Current Address Assignment Mode: Stateless Global IPv6 Address: 2003:c6:afff:4fe0:3efa:30ff:fe03:1211 Link Local IPv6 Address: fe80:0:0:0:3efa:30ff:fe03:1211 PPPoE/PPP Counters: PPPoE control packets received: 2 PPPoE control packets sent: 2166 PPP control packets received: 2687 PPP control packets sent: 2666 Stateless Autoconfig: SLAAC Address: 2003:c6:afff:4fe0:3efa:30ff:fe03:1211 Gateway: fe80:0:0:0:3e61:4ff:fe50:d21a Managed flag: False Valid lifetime: 14400 Preferred lifetime: 1800 Remaining Valid lifetime: 0 days, 3:51:54 Remaining Preferred lifetime: 0 days, 0:21:54 DHCPv6 Details: Interface: ethernet1/2 Rapid Commit: Disabled State: BOUND Client: Address: fe80::3efa:30ff:fe03:1211 DUID: 000100012ef2e3c73cfa30031211 (Type: LLT) Server: Address: fe80::3e61:4ff:fe50:d21a DUID: 00020000058333633a36313a30343a35303a64373a6330000000 Preference: 0 Gateway: fe80::3e61:4ff:fe50:d21a Remaining lease time: 0 days 21:31:18 IPv6 Address (IA_NA): IPv6 Address (IA_TA): Delegated Prefix: IAID: 19000011 IPv6 Prefix (IA_PD): Prefix: 2003:c6:af4f:6d00::/56 Preferred Lifetime (sec): 86400 Valid Lifetime (sec): 86400 DNS Server: 2003:180:2:8000::53 2003:180:2:8100::53 DNS Suffix: Counters: DHCPv6 control packets received: 3 DHCPv6 control packets sent: 3 RA control packets received: 18 RS control packets sent: 1 weberjoh@pa-home> weberjoh@pa-home> |
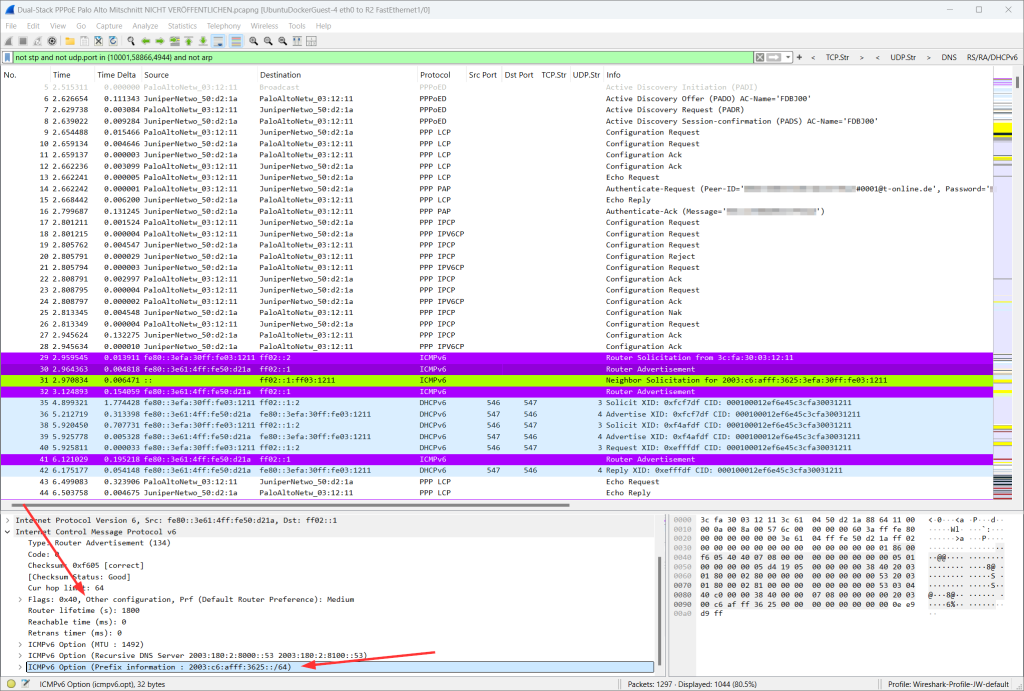
A Little Wiresharking
This is what it looks like on the wire between the Palo and the modem, captured with a real network TAP, the ProfiShark 1G. You can see the whole PPPoE process with its sub-protocols PPP LCP, PPP PAP, PPP IPCP, and PPP IPV6CP 😂, followed by an RA from the ISP with the O-flag and a prefix option (packet nr. 30, red arrows down below), the DAD message from the Palo (31), and the DHCPv6-PD process (35ff). This capturing took place at a later date, hence the shown IP addresses are different from the screenshots above. Never mind.
That’s it. Happy networking. ;)
Soli Deo Gloria!
Photo by Jonny Gios on Unsplash.