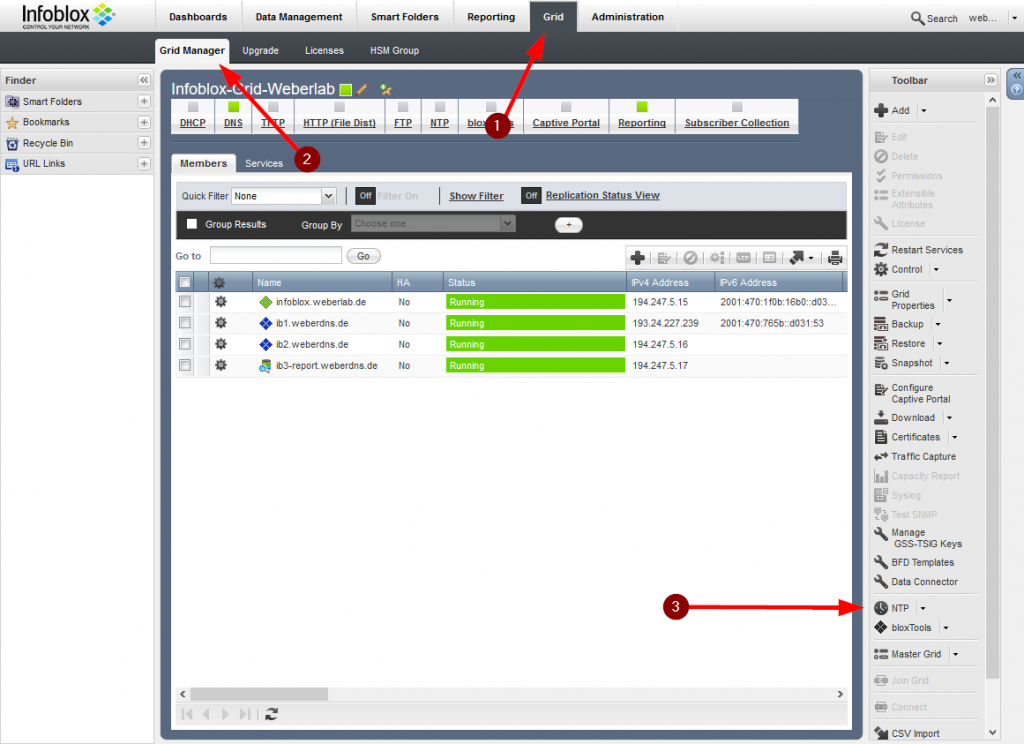
Configuring NTP authentication on the Infoblox Grid Master is quite simple. Everything is packed inside the single “NTP Grid Config” menu. You just have to enter the NTP keys respectively key IDs and enable authentication on the appropriate servers. In the case of incorrect authentication values an error message is logged. Very good, since this is not the case on some other network security devices (Palo, Forti).
Too bad that it only supports MD5 while SHA-1 should be used instead of.
For a secure environment you should use 3x your own stratum 1 NTP servers along with NTP authentication. Refer to Why should I run own NTP Servers?. I am using 2x Raspberry Pis (based on DCF77 and GPS) and a Meinberg M200. NTP authentication is enabled on any of them. For each NTP server I have different NTP keys since you must use different key IDs for each of them. You can’t use the same ID with different keys anywhere.
I am using vNIOS version 8.3.4 for the following setup. Find the NTP config at: Grid -> Grid Manager -> (right-hand side) NTP -> NTP Grid Config.
My config looks like that:
Note the MD5 keys rather than SHA-1. :( Anyway, better than nothing.
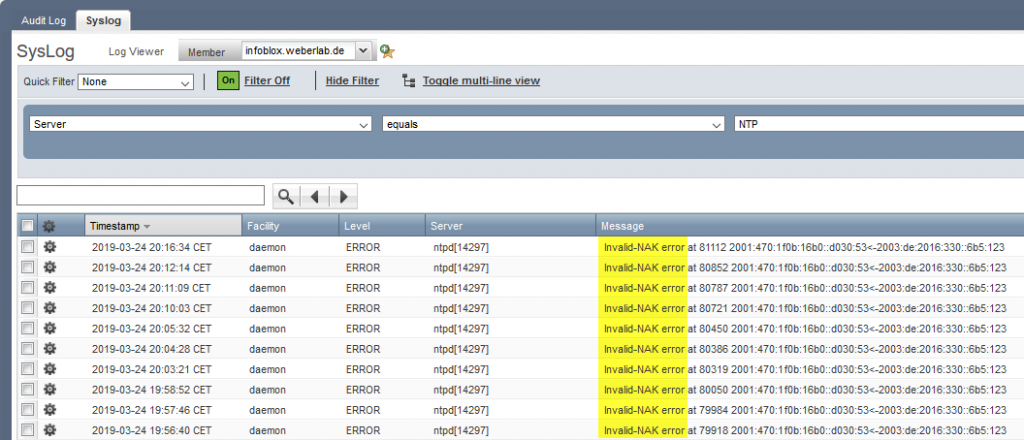
For testing purposes, I have entered a falsified NTP key (ID 2). Using the show ntp command reveals a state of .INIT. for that one (line 7):
|
1 2 3 4 5 6 7 8 9 |
Infoblox > show ntp remote refid st t when poll reach delay offset jitter ============================================================================== 127.127.1.1 .LOCL. 12 l 23h 64 0 0.000 0.000 0.000 +2a01:4f9:2b:a5a 51.174.131.248 2 u 245 256 377 33.536 -3.225 6.057 *2003:de:2016:33 .PZF. 1 u 197 256 377 8.079 -0.128 0.638 2003:de:2016:33 .INIT. 16 u - 256 0 0.000 0.000 0.000 +2003:de:2016:33 .DCFa. 1 u 13 256 377 14.818 -1.194 0.711 -2a02:c205:2009: 26.91.187.18 2 u 236 256 377 12.652 0.639 0.570 |
While the logs clearly state the authentication error. Nice!
However, please note that I am not completely happy with the CLI output from the above mentioned “show ntp” because it does NOT explicitly show which NTP servers are in fact using authentication. I would like to have a more detailed NTP output as on Cisco routers with their “show ntp associations detail”.
Featured image “Weitsicht” by Norbert Reimer is licensed under CC BY-SA 2.0.