Another update of the Ultimate PCAP is available. Again, there are some special new packets in there which I want to point out here. Feel free to download the newest version to examine those new protocols and packets by yourself. Featuring: SNMPv3, WoL, IPMI, HSRP, Zabbix, Pile of Poo, and Packet Comments. ✅
SNMPv3 with AuthPriv
We all know that SNMPv2c (the “security not my problem” protocol) is heavily insecure, hence we should use SNMPv3 with AuthPriv to get authentication and privacy. Here are some packets to look at. A checkmk instance queries a Meinberg LANTIME M200 NTP server. IPv6 and legacy IP:
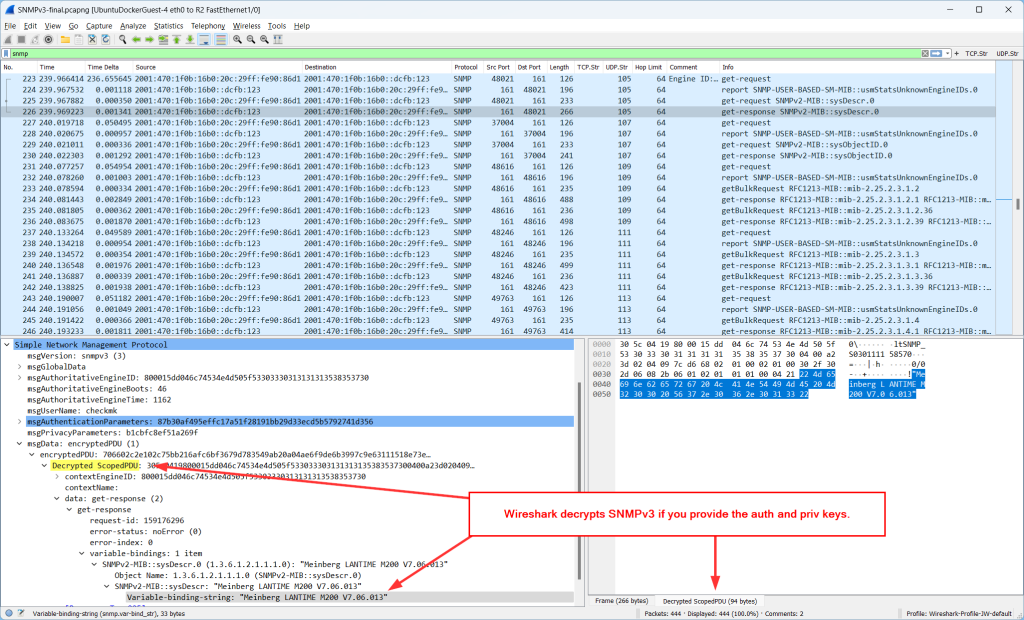
Now, here is the neat thing about Wireshark: You can add the auth and priv keys to get those packets decrypted. Here they are for those packets:
- Username: checkmk
- SHA256: rWezwNZIbgLN6Fka4iZ8
- AES128: jwmY294SQXt4AD9kPGKD
I also added that information in the packet comments of the very first SNMPv3 packet for IPv6 and legacy IP. This is how you can add them: Edit -> Preferences -> Protocols -> SNMP -> Users Table -> Edit -> Create new entry:
After that, Wireshark shows “Decrypted ScopedPDU” data in readable text within the Packet Details pane as well as at the Packet Bytes pane:
Wake-on-LAN, WoL
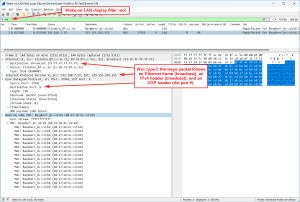
Waking up a Raspi via Wake-on-LAN packets. There are two variants to send the magic packet, which is sixteen repetitions of the target computer’s 48-bit MAC address:
- directly following the Ethernet frame, Ethertype 0x0842 (though not officially registered), using this tool: sudo etherwake -i eno1 B8:27:EB:BC:CD:B4
- encapsulated in an IP and UDP packet/datagram (UDP destination port 9, the “Discard” protocol), sent to the Ethernet and IP broadcast address, using: wakeonlan B8:27:EB:BC:CD:B4
Both variants are display filtered with simply wol:
Some more details about WoL are on the Wireshark Wiki.
IPMI/RMCP+
“The Intelligent Platform Management Interface (IPMI) is a set of computer interface specifications for an autonomous computer subsystem that provides management and monitoring capabilities independently of the host system’s CPU, firmware (BIOS or UEFI) and operating system”, Wikipedia. Don’t ask me any details about it, please. :D You can monitor and power on/off servers and so on. In my case, I’m using the ipmitool (version 1.8.18) to query an HP ProLiant DL380p Gen8 server (iLO firmware 2.78) like this:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 |
weberjoh@nuc:~$ ipmitool -I lanplus -H esxi3-ilo.weberlab.de -U Testuser -P ThisIsThePassword sensor UID Light | 0x0 | discrete | 0x0180| na | na | na | na | na | na Sys. Health LED | na | discrete | na | na | na | na | na | na | na 01-Inlet Ambient | 24.000 | degrees C | ok | na | na | na | na | 42.000 | 46.000 02-CPU 1 | 40.000 | degrees C | ok | na | na | na | na | 70.000 | na 03-CPU 2 | 59.000 | degrees C | ok | na | na | na | na | 70.000 | na 04-P1 DIMM 1-3 | 36.000 | degrees C | ok | na | na | na | na | 87.000 | na 05-P1 DIMM 4-6 | na | | na | na | na | na | na | 87.000 | na 06-P1 DIMM 7-9 | 36.000 | degrees C | ok | na | na | na | na | 87.000 | na 07-P1 DIMM 10-12 | 37.000 | degrees C | ok | na | na | na | na | 87.000 | na 08-P2 DIMM 1-3 | 42.000 | degrees C | ok | na | na | na | na | 87.000 | na 09-P2 DIMM 4-6 | na | | na | na | na | na | na | 87.000 | na 10-P2 DIMM 7-9 | 36.000 | degrees C | ok | na | na | na | na | 87.000 | na 11-P2 DIMM 10-12 | 37.000 | degrees C | ok | na | na | na | na | 87.000 | na 12-HD Max | 35.000 | degrees C | ok | na | na | na | na | 60.000 | na 13-Chipset | 55.000 | degrees C | ok | na | na | na | na | 105.000 | na 14-P/S 1 | 39.000 | degrees C | ok | na | na | na | na | na | na 15-P/S 2 | 37.000 | degrees C | ok | na | na | na | na | na | na 16-P/S 2 Zone | 42.000 | degrees C | ok | na | na | na | na | 75.000 | 80.000 17-VR P1 | 43.000 | degrees C | ok | na | na | na | na | 115.000 | 120.000 18-VR P2 | 46.000 | degrees C | ok | na | na | na | na | 115.000 | 120.000 19-VR P1 Mem | 39.000 | degrees C | ok | na | na | na | na | 115.000 | 120.000 20-VR P1 Mem | 39.000 | degrees C | ok | na | na | na | na | 115.000 | 120.000 21-VR P2 Mem | 41.000 | degrees C | ok | na | na | na | na | 115.000 | 120.000 22-VR P2 Mem | 44.000 | degrees C | ok | na | na | na | na | 115.000 | 120.000 23-VR P1Vtt Zone | 38.000 | degrees C | ok | na | na | na | na | 90.000 | 95.000 24-VR P2Vtt Zone | 43.000 | degrees C | ok | na | na | na | na | 90.000 | 95.000 25-HD Controller | 76.000 | degrees C | ok | na | na | na | na | 100.000 | na 26-iLO Zone | 40.000 | degrees C | ok | na | na | na | na | 90.000 | 95.000 27-LOM Card | na | | na | na | na | na | na | 100.000 | na 28-PCI 1 | na | | na | na | na | na | na | 100.000 | na 29-PCI 2 | na | | na | na | na | na | na | 100.000 | na 30-PCI 3 | na | | na | na | na | na | na | 100.000 | na 31-PCI 4 | na | | na | na | na | na | na | 100.000 | na 32-PCI 5 | na | | na | na | na | na | na | 100.000 | na 33-PCI 6 | na | | na | na | na | na | na | 100.000 | na 34-PCI 1 Zone | 35.000 | degrees C | ok | na | na | na | na | 65.000 | 70.000 35-PCI 2 Zone | 36.000 | degrees C | ok | na | na | na | na | 66.000 | 71.000 36-PCI 3 Zone | 36.000 | degrees C | ok | na | na | na | na | 66.000 | 71.000 37-PCI 4 Zone | na | | na | na | na | na | na | 65.000 | 70.000 38-PCI 5 Zone | na | | na | na | na | na | na | 65.000 | 70.000 39-PCI 6 Zone | na | | na | na | na | na | na | 65.000 | 70.000 40-I/O Board 1 | 42.000 | degrees C | ok | na | na | na | na | 66.000 | 71.000 41-I/O Board 2 | na | | na | na | na | na | na | 66.000 | 71.000 42-VR P1 Zone | 33.000 | degrees C | ok | na | na | na | na | 95.000 | 100.000 43-BIOS Zone | 48.000 | degrees C | ok | na | na | na | na | 90.000 | 95.000 44-System Board | 39.000 | degrees C | ok | na | na | na | na | 80.000 | 85.000 45-SuperCap Max | 29.000 | degrees C | ok | na | na | na | na | 65.000 | na 46-Chipset Zone | 43.000 | degrees C | ok | na | na | na | na | 75.000 | 80.000 47-Battery Zone | 41.000 | degrees C | ok | na | na | na | na | 75.000 | 80.000 48-I/O Zone | 42.000 | degrees C | ok | na | na | na | na | 75.000 | 80.000 49-Sys Exhaust | 39.000 | degrees C | ok | na | na | na | na | 75.000 | 80.000 50-Sys Exhaust | 39.000 | degrees C | ok | na | na | na | na | 75.000 | 80.000 Fan 1 | 7.840 | percent | ok | na | na | na | na | na | na Fan 2 | 7.840 | percent | ok | na | na | na | na | na | na Fan 3 | 8.624 | percent | ok | na | na | na | na | na | na Fan 4 | 16.464 | percent | ok | na | na | na | na | na | na Fan 5 | 27.440 | percent | ok | na | na | na | na | na | na Fan 6 | 27.440 | percent | ok | na | na | na | na | na | na Power Supply 1 | 185 | Watts | ok | na | na | na | na | na | na Power Supply 2 | 0 | Watts | ok | na | na | na | na | na | na Power Meter | 196 | Watts | ok | na | na | na | na | na | na Power Supplies | 0x0 | discrete | 0x0280| na | na | na | na | na | na Fans | 0x0 | discrete | 0x0180| na | na | na | na | na | na Memory | 0x0 | discrete | 0x4080| na | na | na | na | na | na C1 P1I Bay 1 | 0x1 | discrete | 0x0180| na | na | na | na | na | na C1 P1I Bay 2 | 0x1 | discrete | 0x0180| na | na | na | na | na | na C1 P1I Bay 3 | 0x1 | discrete | 0x0180| na | na | na | na | na | na C1 P1I Bay 4 | 0x1 | discrete | 0x0180| na | na | na | na | na | na C1 P2I Bay 5 | 0x1 | discrete | 0x0180| na | na | na | na | na | na C1 P2I Bay 6 | 0x1 | discrete | 0x0180| na | na | na | na | na | na C1 P2I Bay 7 | 0x1 | discrete | 0x0180| na | na | na | na | na | na C1 P2I Bay 8 | 0x1 | discrete | 0x0180| na | na | na | na | na | na weberjoh@nuc:~$ weberjoh@nuc:~$ weberjoh@nuc:~$ ipmitool -I lanplus -H 192.168.3.83 -U Testuser -P ThisIsThePassword power status Chassis Power is on weberjoh@nuc:~$ |
This is how it looks like in Wireshark. No session setup since it relies on UDP (port 623). The protocol is detected as IPMB and RMCP+ (display filters: ipmb and rmcp), while you can see some more flags in the Info column. It seems like encryption is used – but don’t ask me how.
On a Palo, it is detected as “rmcp”:
For more information about IPMI, have a look at these very detailed Wiki articles at Thomas-Krenn.AG.
HSRP Version 1 aka 0
It’s a common best practice to set standby version 2 whenever you’re using HSRP on a Cisco router. That’s why I only had those version 2 HSRP packets in the Ultimate PCAP. Nevertheless, I let out this version statement just to capture some HSRP version 1 packets, which are specified for IPv4 only. Obvious differences: the destination IPv4 multicast address is 224.0.0.2 (rather than 224.0.0.102) and Wireshark lists its protocol as HSRP rather than HRSPv2. Little confusion though the “version” field within the HSRP packets is set to 0. But this seems to be correct according to RFC 2281. (Captured out of GNS3, by the way.)
Zabbix Traffic
Thanks to Markku Leiniö I added some different Zabbix connections. Please refer to his GitHub repo or his blog posts concerning any details. As of now (Wireshark version 4.0) there is no official Zabbix dissector integrated.
Filtering for Pile of Poo
Just something funny at the end. At the keynote of the Wireshark conference “SharkFest” 2022 in Europe, Gerald Combs, the creator of Wireshark, talked about various new display filter possibilities, e.g., filtering for emojis such as the pile of poo. Challenge accepted. ;) Here is my proof of concept, or, as @noIPv6 has pointed out, it is a poo of concept. Search for udp contains "?" within the Ultimate PCAP and you’ll find it. Try it by yourself by doing a DNS lookup of “pile-of-poo.weberdns.de”.
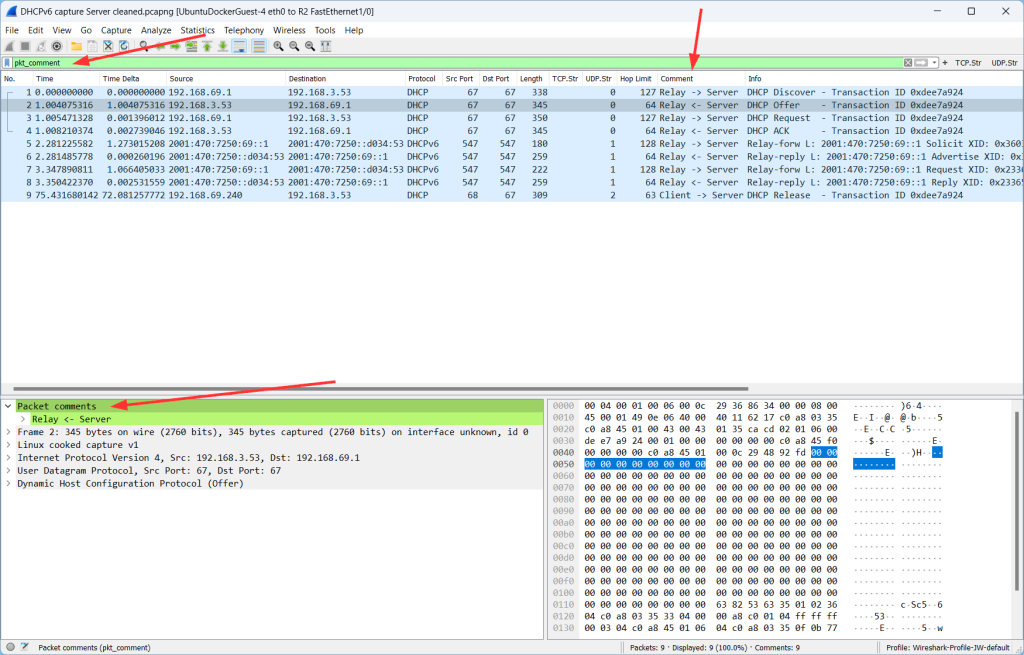
Packet Comments
No protocol, but a Wireshark feature: you can add/read/edit/delete packet comments. Find some in my DHCP captures, for example. Either by using the display filter pkt_comment, by finding one of those packets (green bar within the packet details), or by a custom column:
Soli Deo Gloria.
Photo by Amber Flowers on Unsplash.










One thought on “More Capture Details III”