Klemmt es im Netzwerk, so helfen Ping und Traceroute, Fehler und Engpässe einzukreisen. Wir erklären die Funktionsweise und helfen Angriffe aufzudecken.
Continue reading Netzwerk-Monitoring: Ping und Traceroute richtig interpretieren
Klemmt es im Netzwerk, so helfen Ping und Traceroute, Fehler und Engpässe einzukreisen. Wir erklären die Funktionsweise und helfen Angriffe aufzudecken.
Continue reading Netzwerk-Monitoring: Ping und Traceroute richtig interpretieren

Angreifer verwenden gern Ping und Traceroute, um Server im Internet ausfindig zu machen. Das bringt viele Security-Admins in Versuchung, den Ping- und Traceroute-Verkehr mittels ihrer Firewall in ihrem Netz zu unterbinden. Doch damit behindern sie nur die Arbeit von Server-Administratoren, denn es gibt noch viel mehr Möglichkeiten, Server aufzuspüren.

I was missing a generic layer 4 ping in my toolbox. Initially searching for a mere TCP ping, I have found Nping which completely satisfies my needs and gives so much more. ;)
What’s a layer 4 ping, and why? –> A normal ping (= ICMP echo-request) reveals whether the destination IP address, that is: the mere server/VM, is up and running. That’s great for a layer 3 networker since routing to and from the destination is already working. However, it does NOT reveal whether or not a service at layer 4 (TCP or UDP) is up and running as well. That’s what a layer 4 ping is about: sending TCP SYNs to the port in question, waiting for a “SYN ACK” (port is listening) or “RST”/no reply (port is not available). Common use cases: Waiting for a service to start again after an upgrade, or waiting for new firewall policies (to allow or deny) a certain port.

This post is not about software but hardware tools for network admins. Which network gadgets am I using during my daily business? At least three, namely the Airconsole, the Pockethernet and the ProfiShark, which help me in connecting to serial ports, testing basic network connectivity, and capturing packets in a high professional way. Come in and have a look at how I’m working.

Some time ago I published a pcap that can be used to study basic IPv6 protocol messages such as ICMPv6 for Router Advertisements, Neighbor Solicitations, etc.: “Basic IPv6 Messages: Wireshark Capture“. You can use it to learn the basic IPv6 address assignment and layer 2 address resolution. However, that pcap does not include any upper layer protocols.
This time I captured a few application layer protocols that I used over IPv6 rather than over legacy IP. Common user protocols such as DNS, HTTP/S, IMAP, SMTP (with STARTTLS), as well as some network administration protocols: SSH, SNMP, and Ping. It is not that interesting at all ;) though you can use it to have some examples for Wireshark to prove that those application protocols are almost the same when run above IPv6 compared to IPv4.

I just want to share my happiness about the RIPE Atlas measurements. If you have not heard about it yet, keep on reading. Following is a very basic overview of how the Atlas tool from the RIPE NCC can be used to test the connectivity of your own equipment.

I really love ping! It is easy to use and directly reveals whether the network works or not. Refer to Why Ping is no Security Flaw! (But your Friend) and Advanced Tracerouting. At least outgoing pings (from trust to untrust) should be allowed without any security concerns. However, many companies are denying these ICMP echo-requests from untrust into the DMZ which makes it difficult to test whether all servers are up and running.
I was sitting at the customer’s site replacing the DMZ firewall. Of course I wanted to know (from the outside) whether all servers are connected correctly (NAT) and whether the firewall permits the connections (policy). However, ping was not allowed. Therefore I used several layer 7 ping tools that generate HTTP, DNS, or SMTP sessions (instead of ICMP echo-requests) and revealed whether the services (and not only the servers) were running. Great!
This post shows the installation and usage of httping, dnsping, and smtpping on a Linux machine, in my case a Ubuntu server 14.04.4 LTS, as well as some Wireshark screenshots from captured sessions. Finally, a pcap file can be downloaded that shows the sample runs of all three tools.

Just a short post this time, but an interesting fact concerning different Internet Service Providers (ISPs) and their routing to/from other countries. I have a customer in Germany that has a remote office in France, connected via a site-to-site VPN. Around April last year the french office decided to change the ISP to a cheaper competitor that offers the same speed/bandwidth and therefore has no disadvantages… Well, I disagree.

Seit wenigen Tagen bin ich glücklicher Kunde eines Telekom Glasfaseranschlusses. Mit satten 50/10 MBit/s rasen die Daten bei mir ein und aus. Neben der deutlich höheren Geschwindigkeit war ich aber auch an den Latenzen der beiden Anschlüsse interessiert und habe entsprechende Tests gemacht. Hier kommen die Ergebnisse.
Continue reading Ping Times/Latency: DSL vs. Glasfaser, IPv4 vs. IPv6

A common misunderstanding of traceroute is that it fully relies on ping. “If I block ping at my firewall, no one can use traceroute to reveal my internal routing path”. Unfortunately, this is not true. If traceroute is used with TCP SYN packets on permitted TCP/UDP ports, all intermediary firewalls will handle the IP packets with TTL = 0 corresponding to the RFCs and will reply with an ICMP time exceeded packet to the source.
In this post, I am listing an example that uses traceroute with TCP port 25 (SMTP) to traverse a firewall. A sample pcap file can be downloaded while some Wireshark screenshots show a few details.

One core topic when designing firewall policies is the following question: Is ping a security attack? Should ICMP echo-request messages be blocked in almost any directions?
My short answer: Ping is your friend. :) You won’t block hackers if you block ping. Instead, ping is quite useful for network administrators checking basic network connectivity. That is: I suggest allowing ping anywhere around, accept incoming connections from the Internet to the trusted networks.
Here comes a discussion:
Continue reading Why Ping is no Security Flaw! (But your Friend)

Hier kommen zwei interessante Graphen von der AVM FRITZ!Box, welche mit einem gängigen DSL-Anschluss im Internet hängt:
Continue reading Ping-Zeiten der FRITZ!Box unter (Netzwerk-) Last
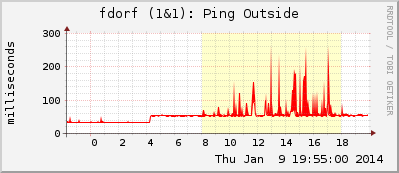
MRTG can also evaluate values from external scripts such as the “mrtg-ping-probe” program which returns the round-trip time from the initiated ping command to the specified destination host. With an additional GraphStyle called “range” from Routers2, these ping times can be displayed in the monitoring system. This graph style shows the “min” and “max” RTT in one vertical line instead of two independent lines.
Since there is not much to say about this process, I will only paste my MRTG/Routers2 config for mrtg-ping-probe and will show a few example graphs here.